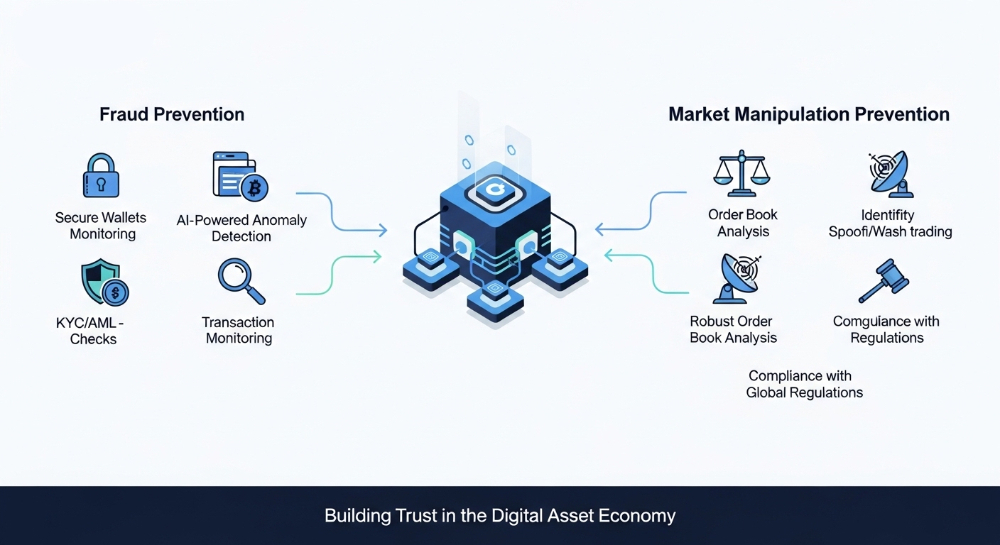
How Crypto Exchange Development Helps Prevent Fraud and Market Manipulation
The rapid growth of cryptocurrency adoption across the United States and the United Kingdom has transformed digital asset trading from a niche activity into a mainstream financial service. Institutional investors, retail traders, fintech startups, and traditional financial firms are all entering the crypto market at scale. However, this expansion has also intensified concerns around fraud, market manipulation, insider trading, and operational risk. Regulators such as FinCEN, the SEC, and state authorities in the US, along with the FCA and UK AML bodies, are placing increased scrutiny on how crypto exchanges are built, operated, and governed.
In this environment, the role of professional crypto exchange platform development is no longer limited to enabling trading functionality. Secure architecture, compliance-ready workflows, surveillance systems, and transparent operational controls have become essential foundations for trust. Exchanges that fail to implement robust security and monitoring mechanisms risk regulatory penalties, reputational damage, and loss of user confidence. As a result, businesses are increasingly turning to an experienced cryptocurrency exchange development company to design platforms that proactively prevent fraud rather than react to it after incidents occur.
Effective crypto exchange development services combine secure system design, advanced identity verification, market surveillance, custody protection, and automated compliance into a unified platform. These elements work together to reduce vulnerabilities, detect abnormal behavior in real time, and provide auditable evidence of compliance for regulators in both the US and UK markets.
This article explores how modern cryptocurrency exchange software development directly addresses fraud and market manipulation risks by focusing on six critical areas:
- Secure architecture and system design that reduce attack surfaces and internal abuse
- Strong authentication, KYC, and access controls aligned with US and UK regulations
- Real-time market surveillance tools to detect spoofing, wash trading, and price manipulation
- High-integrity trading engines that ensure fair order matching and execution
- Robust custody and wallet security models that protect customer funds
- Automated compliance, auditing, and incident response frameworks
By understanding how these components are implemented by a capable crypto exchange development company, decision-makers can better evaluate the long-term security, compliance readiness, and credibility of their trading platforms in highly regulated markets like the United States and the United Kingdom.
Secure Architecture and Design: The Foundation Against Fraud
A secure system architecture is the first and most important defense against fraud and market manipulation. Many of the most damaging incidents in crypto markets have not resulted from exotic attacks, but from poor design decisions that expanded the attack surface or allowed unauthorized access to critical systems. In crypto exchange platform development, security must be embedded from the earliest design stages rather than added as an afterthought.
Secure-by-design principles
Secure-by-design means building systems that assume attacks will occur and are structured to limit their impact. In crypto exchange software development, this typically involves isolating critical components, minimizing privileges, and enforcing strict boundaries between systems. For example, user-facing applications should never have direct access to private keys or internal trading logic. Segregation ensures that even if one component is compromised, attackers cannot easily move laterally to more sensitive areas.
A crypto exchange development company will often recommend layered defenses, combining network-level controls, application security, and operational safeguards. This approach aligns well with expectations in both the US and UK, where regulators increasingly look at systemic resilience rather than isolated controls.
Threat modeling and secure coding
Threat modeling is a structured process that identifies potential attackers, attack vectors, and failure scenarios before systems are built. In the context of cryptocurrency exchange software development, threat modeling helps teams anticipate risks such as insider abuse, API manipulation, denial-of-service attacks, or abuse of administrative functions. Secure coding practices then translate these insights into concrete controls, such as input validation, strict authentication checks, and defensive error handling.
Ongoing code reviews and security testing further reduce the likelihood that vulnerabilities make it into production. While no system can be perfectly secure, disciplined development practices significantly lower the probability of exploitable flaws.
Role of a crypto exchange development company in architecture
A professional crypto exchange development company brings experience from previous projects and knowledge of common failure patterns. This allows them to design architectures that balance performance, scalability, and security without unnecessary complexity.
Recommended architecture components often include:
- Segmented microservices for user management, trading, wallets, and reporting
- Isolated networks for production, staging, and development environments
- Hardware security modules or equivalent secure enclaves for sensitive operations
- Centralized logging and monitoring systems with restricted access
From a regulatory perspective, architecture reviews should also consider US and UK requirements, such as data protection obligations, auditability, and operational resilience expectations. By addressing these concerns early, crypto exchange platform development can reduce the risk of fraud while also supporting smoother regulatory engagement.
Authentication, Access Controls, and Identity Verification
Strong authentication and identity controls are critical to preventing fraud in crypto exchanges. Account takeovers, unauthorized withdrawals, and insider misuse of privileged access are among the most common sources of losses. Effective crypto exchange development integrates technical controls with regulatory-compliant identity verification processes.
KYC and AML workflows
Know Your Customer and Anti-Money Laundering processes are legal requirements in both the US and the UK, but they also play a vital role in fraud prevention. Properly designed KYC workflows help ensure that bad actors cannot easily create anonymous accounts to manipulate markets or launder funds. In crypto exchange software development, KYC systems must be tightly integrated with account creation, trading limits, and withdrawal controls.
Typical KYC verification steps include:
- Collection and validation of government-issued identification
- Proof of address verification
- Screening against sanctions and watchlists
- Ongoing monitoring for changes in customer risk profiles
A cryptocurrency exchange development company ensures these workflows are scalable and configurable, allowing platforms to adapt to different regulatory requirements across jurisdictions.
Technical controls for identity assurance
Beyond regulatory KYC, technical authentication mechanisms protect user accounts and internal systems. Multi-factor authentication is now considered a baseline requirement, particularly for withdrawals and sensitive actions. Hardware tokens, mobile authenticators, and biometric options add layers of protection that make account compromise significantly more difficult.
Role-based access control is equally important for internal users. Developers, support staff, and compliance officers should only have access to the systems and data necessary for their roles. Privileged access management tools can further reduce the risk of insider fraud by enforcing approvals, logging actions, and limiting session duration.
How crypto exchange software development implements these controls
In crypto exchange software development, identity and access controls must be consistently enforced across all interfaces, including web applications, mobile apps, and APIs. Inconsistent enforcement is a common source of vulnerabilities.
Compliance considerations for the US and UK include:
- Alignment with FinCEN guidance and state money transmitter laws in the US
- FCA registration requirements and UK AML regulations
- Data protection and privacy obligations, particularly around identity data
By combining regulatory-compliant identity verification with robust technical authentication and access controls, crypto exchange development services help platforms significantly reduce fraud risk while maintaining a smooth user experience.
Market Surveillance and Anti-Manipulation Mechanisms
Market manipulation undermines confidence in trading platforms and can attract severe regulatory consequences. Practices such as wash trading, spoofing, and layering distort prices and volumes, harming legitimate traders. Modern crypto exchange platform development therefore places strong emphasis on market surveillance and real-time monitoring.
Real-time monitoring and anomaly detection
Effective market surveillance systems continuously analyze trading activity, order book behavior, and account interactions. These systems look for patterns that deviate from normal market behavior, such as repeated self-trading, sudden spikes in order placement and cancellation, or coordinated activity across multiple accounts.
Crypto exchange software development teams often integrate rule-based detection with statistical analysis to identify potential manipulation early. Alerts can then be escalated to compliance or risk teams for review.
Algorithmic controls and circuit breakers
In addition to monitoring, exchanges can implement preventive controls that limit the impact of manipulative behavior. Circuit breakers, for example, temporarily halt trading during extreme volatility or abnormal activity. Order size limits and throttling mechanisms can reduce the effectiveness of spoofing strategies that rely on flooding the order book.
These controls must be carefully calibrated to avoid disrupting legitimate trading. A crypto exchange development company brings experience in balancing market integrity with usability.
Integration by a crypto exchange platform development team
Market surveillance capabilities should be deeply integrated into the trading engine and data infrastructure. This allows real-time visibility and rapid response, rather than relying on delayed, post-trade analysis.
Key indicators of market manipulation include:
- High volumes of canceled orders relative to executed trades
- Repeated trades between the same beneficial owners
- Abnormal price movements unsupported by broader market activity
Operational responses may involve warnings, account restrictions, trade reversals, or regulatory reporting, depending on severity and jurisdiction. In the US and UK, clear documentation of surveillance processes is essential for demonstrating compliance and cooperation with regulators.
Secure Trading Engine and Order Matching Integrity
The trading engine is the heart of any exchange, and its integrity is critical to preventing both technical abuse and market manipulation. Poorly designed matching systems can enable unfair advantages, front-running, or disputes over execution fairness.
Deterministic matching and timestamp authenticity
Deterministic matching ensures that orders are executed strictly according to transparent rules, typically based on price and time priority. Accurate timestamping is essential to enforce fairness, especially during periods of high activity. In crypto exchange development services, this often involves synchronized clocks, consistent order sequencing, and immutable logs.
Clear and deterministic behavior helps resolve disputes and supports regulatory audits, particularly in the UK, where market fairness is a key FCA concern.
Mitigations for front-running and latency manipulation
Front-running occurs when actors gain advance knowledge of orders and trade ahead of them. While some risks are inherent to public blockchains, crypto exchange platform development can reduce exposure by controlling internal information flows, limiting privileged access, and monitoring latency patterns.
Design choices such as batching orders or randomizing processing within narrow windows can further reduce opportunities for abuse without compromising performance.
How crypto exchange development services ensure trading integrity
A crypto exchange development company typically implements comprehensive logging and audit trails within the trading engine. These records support investigations, compliance reviews, and user inquiries.
Best practices for trading engine design include:
- Clear separation between order intake and matching logic
- Comprehensive event logging for all order lifecycle stages
- Regular performance testing under simulated peak loads
Hardware and network considerations, such as low-latency but controlled infrastructure, also play a role in ensuring consistent and fair execution. Together, these measures help prevent both technical fraud and perceived manipulation.
Custody, Wallet Security, and Safe Funds Management
Custody failures remain one of the most visible and damaging forms of fraud in crypto markets. Loss of customer funds due to hacks or internal misuse can be catastrophic. As a result, wallet security is a central focus of cryptocurrency exchange development company offerings.
Cold storage and multi-signature strategies
Most exchanges use a combination of hot and cold wallets to balance security and liquidity. Cold storage keeps the majority of assets offline, significantly reducing exposure to online attacks. Multi-signature schemes require multiple approvals for transactions, reducing the risk of single-point failures or insider abuse.
These strategies are well aligned with expectations in the US and UK, where regulators increasingly scrutinize custody arrangements.
HSMs and secure key lifecycle
Hardware security modules or equivalent secure key management systems protect private keys throughout their lifecycle, from generation to storage and use. Crypto exchange software development integrates these systems to ensure that keys are never exposed in plaintext and that access is tightly controlled.
Operational policies are equally important. Clear procedures for key rotation, backup, and recovery reduce the risk of both accidental loss and malicious compromise.
Custody solutions by a cryptocurrency exchange development company
A professional cryptocurrency exchange development company helps clients design custody solutions that match their risk profile and regulatory obligations. This includes advising on insurance options, segregation of client and operational funds, and transparent reporting mechanisms.
Wallet security checklists often cover:
- Withdrawal limits and anomaly detection
- Multi-level approval workflows for large transfers
- Regular reconciliation and proof-of-reserves reporting
These measures not only prevent fraud but also build user trust, which is essential for long-term success.
Compliance Automation, Auditing, and Incident Response
Preventing fraud and market manipulation is not only about prevention but also about detection, response, and accountability. Compliance automation and incident response capabilities are therefore essential components of crypto exchange software development.
Automated AML and reporting
Automated transaction monitoring systems analyze on-chain and off-chain activity to identify suspicious patterns. These systems support AML obligations in the US and UK by flagging high-risk transactions and generating reports for compliance teams.
Automation reduces human error and ensures consistent application of policies, even as transaction volumes grow.
Forensic logging and audit readiness
Comprehensive logging enables exchanges to reconstruct events, investigate incidents, and demonstrate compliance. Logs should cover user actions, administrative changes, trading activity, and system events, and they should be protected against tampering.
Audit readiness is particularly important in regulated markets. Clear documentation and accessible records help exchanges respond efficiently to regulatory inquiries and independent audits.
Incident response and regulatory notification in US and UK
Despite best efforts, incidents can still occur. Crypto exchange development services therefore include incident response planning, with defined roles, escalation paths, and communication strategies.
Essential elements include:
- Predefined incident severity levels and response timelines
- Internal and external communication plans
- Regulatory notification procedures aligned with US and UK expectations
By preparing in advance, exchanges can contain damage, protect users, and maintain credibility even in difficult situations.
Conclusion: Building Trust Through Secure and Compliant Crypto Exchange Development
Preventing fraud and market manipulation is not a single feature or tool—it is the result of deliberate, well-architected crypto exchange development that integrates security, compliance, and transparency at every layer of the platform. As regulatory oversight increases in the United States and the United Kingdom, exchanges must demonstrate not only technical sophistication but also operational discipline and accountability. This makes professional crypto exchange software development a strategic investment rather than a technical expense.
Throughout this article, we have explored how a cryptocurrency exchange development company can help businesses mitigate risks through secure architecture, identity verification, market surveillance, trading integrity, custody protection, and automated compliance. When these elements are designed cohesively, they create an environment where fraudulent behavior is difficult to execute, quickly detected, and effectively contained.
Key takeaways for US and UK exchange operators include:
- Secure-by-design architecture significantly reduces internal and external fraud risks
- Strong KYC, AML, and access controls align platforms with FinCEN and FCA expectations
- Real-time market surveillance helps prevent manipulation before it impacts users
- Fair and transparent trading engines protect against front-running and abuse
- Advanced custody and wallet security models safeguard user assets
- Automated compliance and audit readiness simplify regulatory interactions
For businesses planning to launch or upgrade a trading platform, partnering with a capable crypto exchange development company ensures that fraud prevention and market integrity are embedded from the start. High-quality crypto exchange development services provide not only technical implementation but also regulatory awareness and operational best practices tailored to US and UK markets.
As competition intensifies and regulators demand higher standards, exchanges that prioritize secure, compliant, and transparent crypto exchange platform development will be best positioned to earn user trust, attract institutional participation, and achieve sustainable growth. Engaging an experienced cryptocurrency exchange software development partner is a critical step toward building a resilient platform that can withstand both technical threats and regulatory scrutiny.