What Is Layer 1 in Blockchain?
Layer 1 in Blockchain
Everything you need to know about layer 1, the base infrastructure of a blockchain.
If we playfully consider blockchain as the “it girl” of Web3, we’re curious to know — how does she do it all? The secret: layers.
Spanning two main types, layer 1 and layer 2, these interoperable networks work together to store, maintain and distribute information across digital decentralized databases that double as peer-to-peer, immutable public ledgers.
Here, we peel back each layer of a blockchain’s makeup for a closer look at their design, purpose and utility.
WHAT IS A LAYER 1 BLOCKCHAIN?
Layer 1 refers to the base infrastructure of a blockchain. Nicknamed “the mainnet,” layer 1 protocols have distinct functionalities such as the ability to process and finalize transactions on its own chain. As the main network within their ecosystem, they define the rules.
What Is Layer 1 in Blockchain?
Layer 1 is the fundamental base network of a blockchain platform. It executes all on-chain transactions and therefore acts as a public ledger’s source of truth.
Processing a transaction, for most networks, consists of logging a user’s cryptocurrency wallet via asymmetric key pairs and its corresponding coin or token balances. The deal passes through a consensus mechanism — which will be distinct to each platform — to verify and finalize the trade or sale. Additionally, layer 1 blockchains host their own native token, which is used to cover transaction costs, or gas fees.
Determining which consensus mechanism is fit for a platform comes down to a trade-off between three main features: security, scalability and decentralization. This compromise is commonly referred to as “the blockchain trilemma,” a concept originally identified by Ethereum co-founder Vitalik Buterin. Whatever isn’t fully covered by layer 1 protocols — typically scalability — can be compensated for in the layer 2 protocol built on top of it (more on that later), serving as an extension to the mainnet’s functionality.
Layer 1 Blockchain Examples
The following list is composed of top layer 1 blockchain networks that power the majority of decentralized applications, or dApps.
Bitcoin: Bitcoin’s layer 1 is the underlying architecture that secures the world’s largest cryptocurrency, top ranked with a live market cap of $367 billion. It operates on a proof-of-work consensus mechanism, which verifies new blocks via an algorithm that uses an computationally-intensive, cryptographic puzzle. Bitcoin is widely considered to be the most secure, decentralized platform — but processing one transaction can take 10 minutes to an hour.
Ethereum: The second largest layer 1 network in Web3 introduced the use of smart contracts, giving it a dynamicism beyond simply a cryptocurrency mine and payment platform. Smart contracts are self-executing programs that verify transactions as long as all pre-set conditions are met. Originally, Ethereum worked off of a proof-of-work consensus mechanism, recently transitioning to a proof-of-stake verification method in a move that would reduce the platform’s energy consumption by about 99.95 percent, according to its website. The convergence of the mainnet and the proof-of-stake sidechain is known as the Merge, which took place on September 15.
Algorand: An alternative layer 1 blockchain option, Algorand operates using smart contracts. It distinguishes itself from the two main players, Bitcoin and Ethereum, by its use of a pure proof-of-stake consensus mechanism. This method selects miners, or block validators, at random to directly decentralize the verification process.
Cardano: One of the first layer 1 blockchains to successfully implement a proof-of-stake model, Cardano is known for its cheap gas fees, high degree of decentralization and ability to generate passive income of its native coin, ADA, for its users. It overwhelmingly outperforms Ethereum’s transaction speed, validating more than 250 transactions per second to Ethereum’s 15.
What Is Layer 2 in Blockchain?
Layer 2 consists of any overlaying network built on top of the mainnet, the layer 1 foundation supporting a blockchain. Typically, layer 2 protocols are optimized for reducing network congestion, lightening the load and increasing throughput of the mainnet. They were created to prevent overdependence or collapse of its layer 1 counterpart. As consensus mechanisms are the defining characteristic to layer 1, so are scaling solutions to layer 2.
While layer 1 chains are the primary security provider within the context of decentralization, layer 2 chains have their own security, but to a far lesser degree, explained software engineer Arie Trouw, who holds over a decade of experience in the blockchain space.
“Layer 2 solutions provide enough security for dApp usage as an alternative to layer 1. They support some or all of the dApp’s functionalities, mimicking the mainnet,” said Trouw, who is also the co-founder of XY Oracle Network, a blockchain protocol currently building a data marketplace-in-the-making. “This allows for bridging between the two layers.”
Layer 2 systems are often confused with sidechains, according to Trouw, but they admittedly function in a similar capacity. Sidechains wholly rely on the security of whatever chain they are connected to, whether it be at a layer 1 or layer 2 capacity, he said.
Layer 2 protocols can be thought of as secondary frameworks designed to optimize a blockchain’s core functionality with a specific use case in mind.
“Improving scale at each level is important,” said Trouw, optimistic about the post-Merge landscape. “Ethereum 2.0 upgrades are a huge gain for blockchain overall, but the continued use and development of layer 2 solutions is imperative.”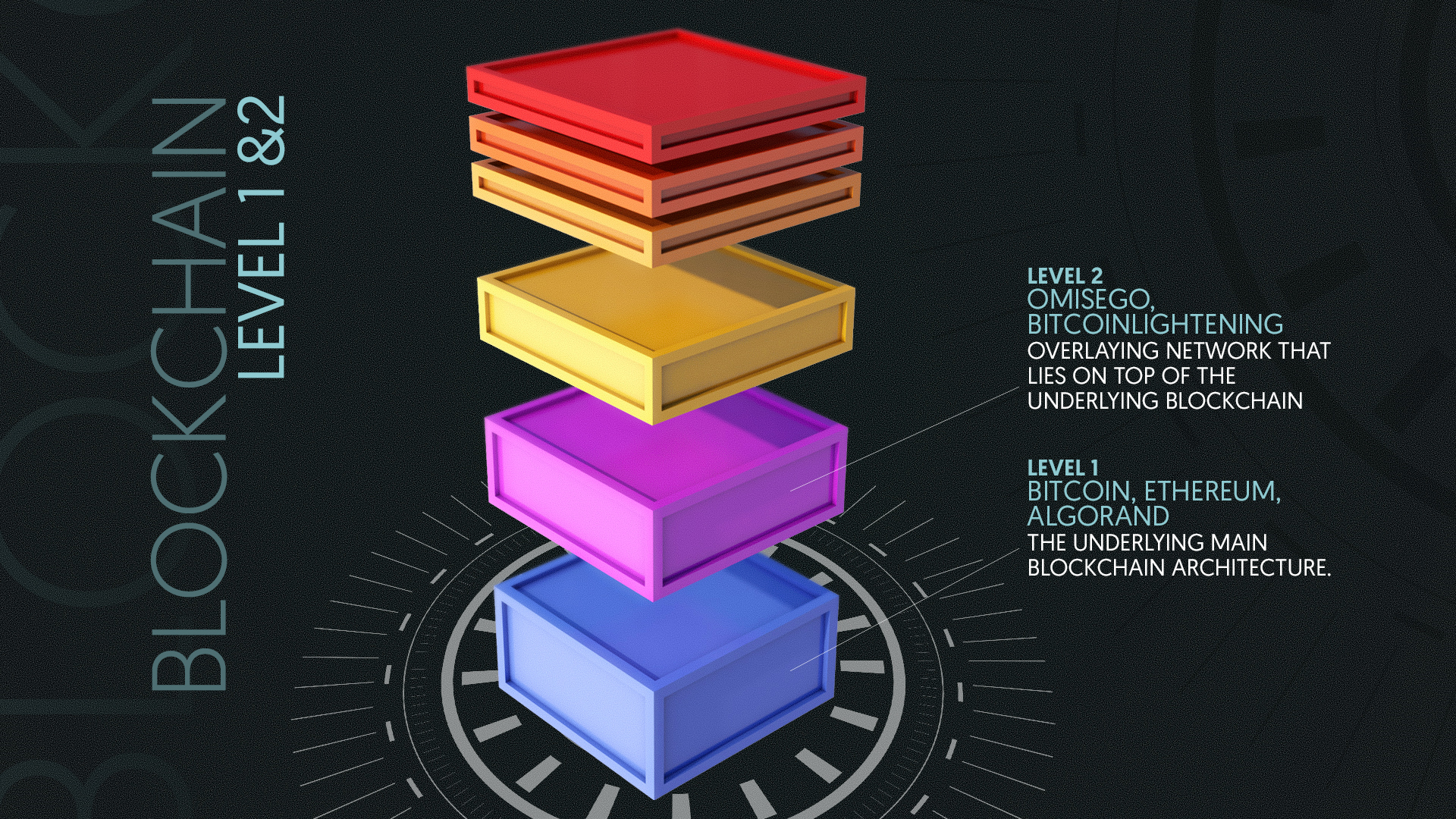
TYPES OF LAYER 2 SCALING SOLUTIONS
- State channels: These apply a two-way channel of communication, allowing participants to conduct an arbitrary amount of off-chain transactions while only needing to submit two transactions to the mainnet, to open and close the channel. State channels eliminate the need for miners and keeps communication between layer 1 and layer 2 to a minimum.
- Nested blockchains: Working co-dependently in distinguished roles, in nested blockchains, layer 2 executes transactions while layer 1 issues and verifies them.
- Rollups: The most common layer 2 scalability solutions, rollups run multiple transactions on separate, independent chains in batches, then stored on the mainnet.
- Sidechains: Interoperable channels with their own consensus mechanism that run independent to main chains, connected by a two-way bridge. This means that sidechains rely on a trusted set of parties to authenticate each user’s participation.
Layer 2 Blockchain Examples
Below are some examples of layer 2 scaling solutions ancillary to Web3’s most ambitious projects.
Lightning Network: Used to support Bitcoin’s main network, this layer 2 addition helps facilitate speedy transactions during heavy traffic — which can take hours — on separate chains independent to the mainnet, reporting the final balance on layer 1 at a calmer time.
Polygon: An assist to the Ethereum blockchain, Polygon runs a proof-of-stake blockchain concurrently alongside the base layer via multiple sidechains, known as commit chains, to increase network scalability and overall transaction speed. Commit chains operate adjacent to the layer 1 blockchain, bundling together batches of transactions to be confirmed en masse before immutably logged into the main chain.
Starknet: With Ethereum as its base, Starknet is a decentralized, permissionless, and censorship-resistant, zero-knowledge rollup. Rollups are a scalability solution that batches transactions off of the layer 1 blockchain on separate chains, to record later on the mainnet. Its speed and scalability is made possible by batching transactions and verifying them together rather than individually, periodically uploading them to the main network’s blockchain. In contrast to Polygon’s open-source layer 2 solution, Starknet is a closed-source project.
Differences Between Layers 1 and 2 in Blockchain
Since decentralization and security are the modus operandi of layer 1 protocols, layer 2 networks can concentrate their resources on providing utility and optimized scalability to a blockchain.
Witek Radomski, co-founder of Enjin, a pre-Bitcoin platform that launched a suite of NFT-oriented products, offered his insight on the differentiation.
“Layer 1 blockchains contain a permanent ledger of all transactions,” Radomski said. “A node in a layer 1 network will contain all of the history of the blockchain, whereas a layer 2 chain is a compressed version with only some of the transaction history. Layer 2 protocols are usually optimized for reducing load on the mainnet for common transactions.”
Enjin began as a community gaming platform, then pivoted to a blockchain-tech focus in 2017. In development, Radomski’s team approached scalability by first establishing their platform’s key purpose — making NFTs easy to use — then fitted a layer 1 protocol customized with only the necessary code to fulfill that objective.
“Layer 1 blockchains contain a permanent ledger of all transactions ... A node in a layer 1 network will contain all of the history of the blockchain, whereas a layer 2 chain is a compressed version with only some of the transaction history. Layer 2 protocols are usually optimized for reducing load on the mainnet for common transactions.”
“As a result, the protocol is super light,” he said. “On top of an optimized layer 1 protocol, we also conduct bulk batch operations instead of minting NFTs one-by-one. This allows us to produce at large scale with relatively light storage capacity. Together, strong infrastructure and efficient operation systems support scalability in the ecosystem.”
In terms of features, layer 1 solutions typically consist of a network of nodes and block-producing miners, storage of all transaction data and a consensus mechanism whereas their layer 2 counterparts can take on many shapes, but often feature complementary chains that implement some sort of scaling solution, as mentioned.
Every blockchain requires a layer 1 mainnet. Layer 2 protocols are considered non-essential, but welcome, to operate most blockchain-based systems.
ONE STEP BELOW: WHAT IS A LAYER 0 BLOCKCHAIN?
Developed retroactively, layer 0 blockchains run beneath a mainnet to enable interoperability across multiple layer 1 protocols. Highly versatile, layer 0 is an underlying scaling solution that, while compatible with layer 1 and layer 2, does not change a blockchain’s structure. The core standards ruling a blockchain’s ecosystem set in layer 1 are respected.
The Blockchain Trilemma
If layer 1 is the only essential layer, why complicate things further? What is the purpose of kitting out a blockchain with layers at all?
The answer to this goes back to the aforementioned triad, a kind of holy grail in the blockchain universe, between security, scalability and decentralization.
“It’s often said that you can have any two, but not all three,” said Vaclav Vincalek, Chief Technology Officer at his consulting firm 555vCTO and writer of weekly tech newsletter, Recurrent Patterns. “For example, Bitcoin and Ethereum are both secure and decentralized because they use proof of work, but neither is scalable. [Open-source platform] EOSIO, on the other hand, is scalable due to its delegated proof-of-stake consensus mechanism, but not as secure or decentralized as either Bitcoin or Ethereum.”
Vincalek’s preferred approach to the blockchain trilemma is sharding. Simply put, sharding is a way of splitting a blockchain network into multiple, smaller networks, or shards, to delegate computational and storage workloads.
“Although no one has been able to definitively solve the blockchain trilemma, which is one of the main obstacles to widespread crypto adoption ... I believe that [dynamic sharding] will help us achieve scalability and decentralization without compromising on security.”
“Sharding allows for a more efficient and scalable way of processing transactions,” he said. “This can help to improve transaction speed and reduce congestion on the network.”
Nischal Shetty, co-founder of Shardeum, an Ethereum-based layer 1 network that uses dynamic sharding to achieve linear scalability, shares a similar approach. In this version of the database partitioning technique, each node holds a different address range with a significant overlap between the address sets assigned to their respective nodes. But what sets Shardeum apart is its ability to combine a number of transactions to be processed as one and deliver fast finality while sharding, Shetty said, ensuring that each node added to the network immediately helps increase the transaction rate per second.
“Although no one has been able to definitively solve the blockchain trilemma, which is one of the main obstacles to widespread crypto adoption,” he said, “I believe that [dynamic sharding] will help us achieve scalability and decentralization without compromising on security.”
Another option: removing the need for consensus from blockchains altogether.
XY Oracle Network co-founder Trouw believes that variations of the encrypted, code-based communication techniques used to secure blockchains, known as cryptography, will eventually settle the debate. He sees self-verifying cryptography, such as zero knowledge proofs, as “the only way to solve the trilemma.”
His platform performs many of the decentralized functions currently executed on other layer 1 and layer 2 systems without consensus, using cryptography in its place.
There is one impasse that is yet to be ironed out, however. Known as the double-spend problem, Trouw said that the duplication of digital tokens, when crypto is mistakenly or fraudulently spent more than once, can only be prevented through a consensus mechanism at this time.
“So removing [the consensus mechanism] is not yet possible,” he said. Still, Trouw is convinced that it’s a matter of when, not if. “Accomplishing security through cryptography instead of consensus is the fusion energy that will give crypto unlimited scale.”
References
- Morris, David Z. (15 May 2016). "Leaderless, Blockchain-Based Venture Capital Fund Raises $100 Million, And Counting". Fortune. Archived from the original on 21 May 2016. Retrieved 23 May 2016.
- Popper, Nathan (21 May 2016). "A Venture Fund With Plenty of Virtual Capital, but No Capitalist". The New York Times. Archived from the original on 22 May 2016. Retrieved 23 May 2016.
- "Blockchains: The great chain of being sure about things". The Economist. 31 October 2015. Archived from the original on 3 July 2016. Retrieved 18 June 2016. The technology behind bitcoin lets people who do not know or trust each other build a dependable ledger. This has implications far beyond the crypto currency.
- Narayanan, Arvind; Bonneau, Joseph; Felten, Edward; Miller, Andrew; Goldfeder, Steven (2016). Bitcoin and cryptocurrency technologies: a comprehensive introduction. Princeton, New Jersey: Princeton University Press. ISBN 978-0-691-17169-2.
- Iansiti, Marco; Lakhani, Karim R. (January 2017). "The Truth About Blockchain". Harvard Business Review. Cambridge, Massachusetts: Harvard University. Archived from the original on 18 January 2017. Retrieved 17 January 2017. The technology at the heart of bitcoin and other virtual currencies, blockchain is an open, distributed ledger that can record transactions between two parties efficiently and in a verifiable and permanent way.
- Oberhaus, Daniel (27 August 2018). "The World's Oldest Blockchain Has Been Hiding in the New York Times Since 1995". Vice. Retrieved 9 October 2021.
- Lunn, Bernard (10 February 2018). "Blockchain may finally disrupt payments from Micropayments to credit cards to SWIFT". dailyfintech.com. Archived from the original on 27 September 2018. Retrieved 18 November 2018.
- Hampton, Nikolai (5 September 2016). "Understanding the blockchain hype: Why much of it is nothing more than snake oil and spin". Computerworld. Archived from the original on 6 September 2016. Retrieved 5 September 2016.
- Bakos, Yannis; Halaburda, Hanna; Mueller-Bloch, Christoph (February 2021). "When Permissioned Blockchains Deliver More Decentralization Than Permissionless". Communications of the ACM. 64 (2): 20–22. doi:10.1145/3442371. S2CID 231704491.
- Sherman, Alan T.; Javani, Farid; Zhang, Haibin; Golaszewski, Enis (January 2019). "On the Origins and Variations of Blockchain Technologies". IEEE Security Privacy. 17 (1): 72–77. arXiv:1810.06130. doi:10.1109/MSEC.2019.2893730. ISSN 1558-4046. S2CID 53114747.
- Haber, Stuart; Stornetta, W. Scott (January 1991). "How to time-stamp a digital document". Journal of Cryptology. 3 (2): 99–111. CiteSeerX 10.1.1.46.8740. doi:10.1007/bf00196791. S2CID 14363020.
This content is for informational and educational purposes only. Built In strives to maintain accuracy in all its editorial coverage, but it is not intended to be a substitute for financial or legal advice.