A Dive into Phalcon Block: Real-Time Defense Against Smart Contract Hacks
In this article, we’ll unravel the capabilities of BlockSec’s Phalcon Block, a cutting-edge tool designed to automatically block smart contracts and DeFi hacks in real time. We will explore this revolutionary tool with a live demonstration, replicating the $7 million hack on HundredFinance.
What is Phalcon Block
Let’s kick things off by delving into the inner workings of Palcon Block, you can also dive into the following video which covers all the information that is presented in this article:
https://youtu.be/J03-rNzKbXU
Phalcon Block Complete Guide
Phalcon Block goes beyond conventional attack monitoring, introducing a robust system that automatically responds to web3 threats. With a proven track record of successfully thwarting over 20 real-world hacks and rescuing more than $14 million worth of assets, Phalcon Block stands as a guardian for Web3 protocols. As the only security product with a proven record of automatically blocking multiple crypto hacks, Phalcon Block stands as a strong tool in the Web3 security space.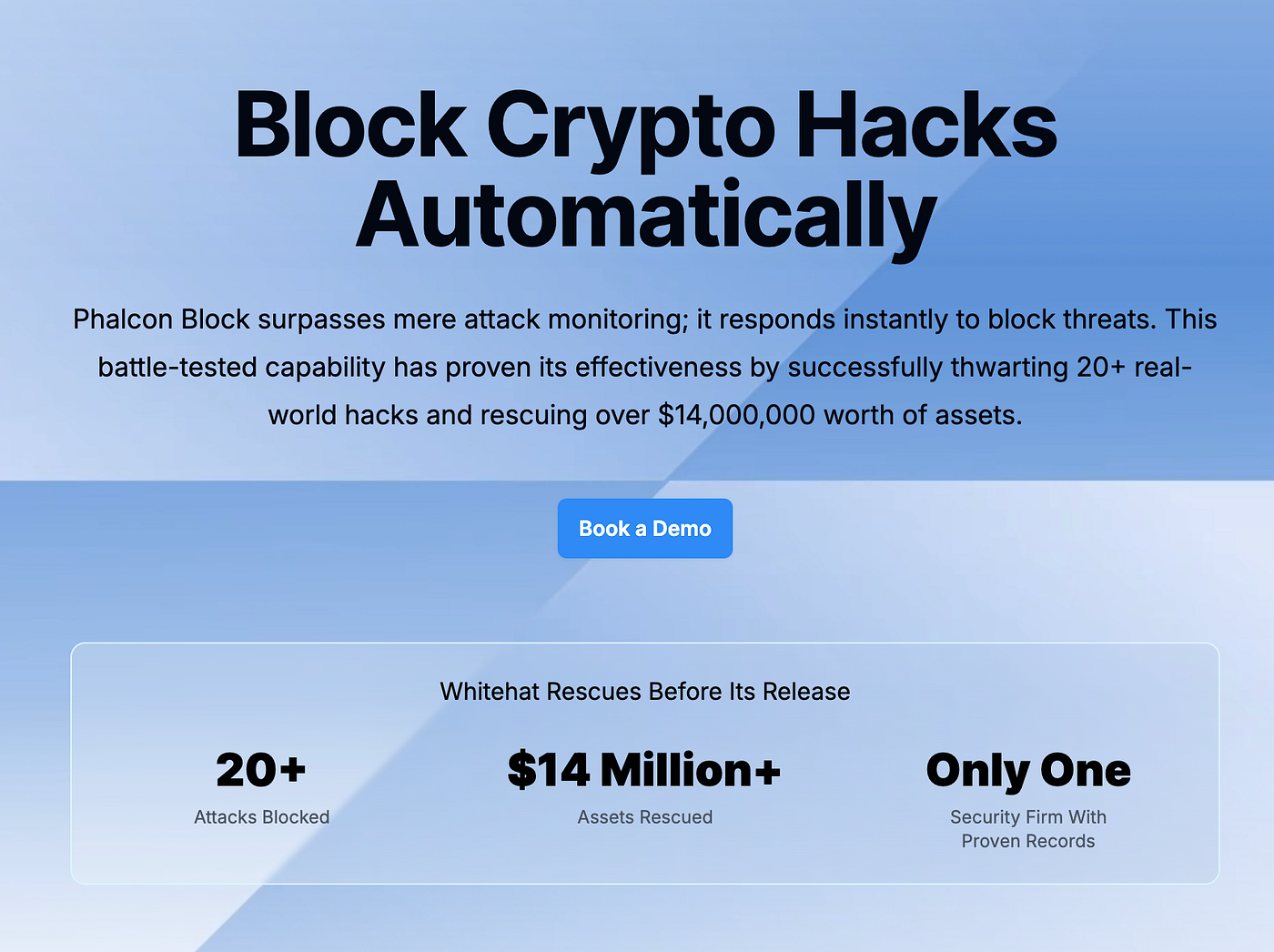
Phalcon Block by BlockSec
Phalcon Block is currently in beta mode and operating on a waiting list basis. If you wish to expedite your access to this cutting-edge tool, utilize this special link: https://johnnytime.xyz/phalcon-block-johnny-vip
By doing so, the BlockSec team will promptly review your request, potentially accelerating your access approval. You will have the chance to experience Phalcon Block firsthand and be among the first to benefit from its innovative features.
Precise Attack Detection
At the core of Phalcon Block’s effectiveness lies its precise attack detection mechanism. The engine meticulously scans both pending and on-chain transactions, employing algorithms that prioritize accuracy. This ensures minimal false positives. Operating around the clock, Phalcon Block takes automatic actions 24/7, ensuring continuous security without the need for human intervention.
Automatic Attack Blocking
Phalcon Block takes security to the next level by automatically initiating a blocking transaction faster than attackers can execute their hacks. This essentially frontruns the attack transaction and makes it ineffective. Users have the freedom to configure different response actions tailored to specific attack types and impacts.
How Does Phalcon Block Work?
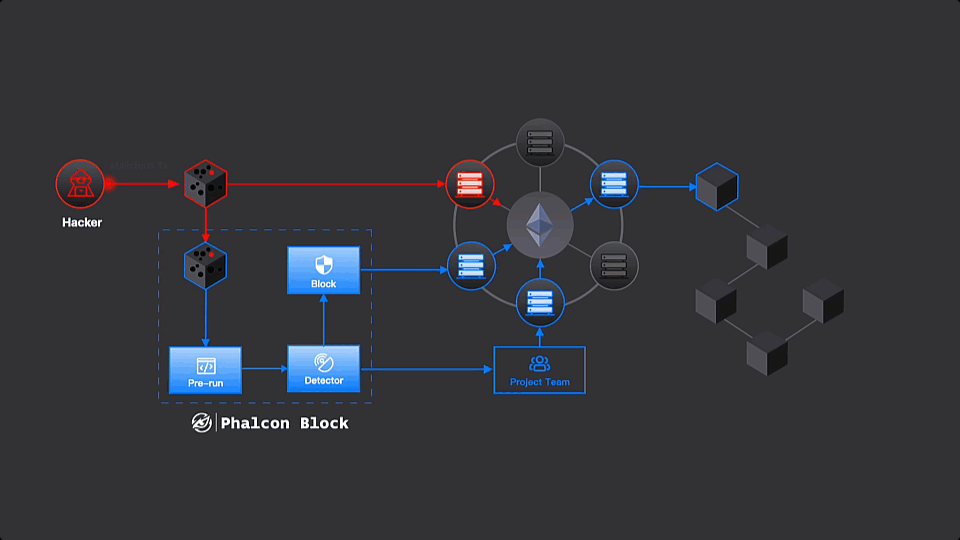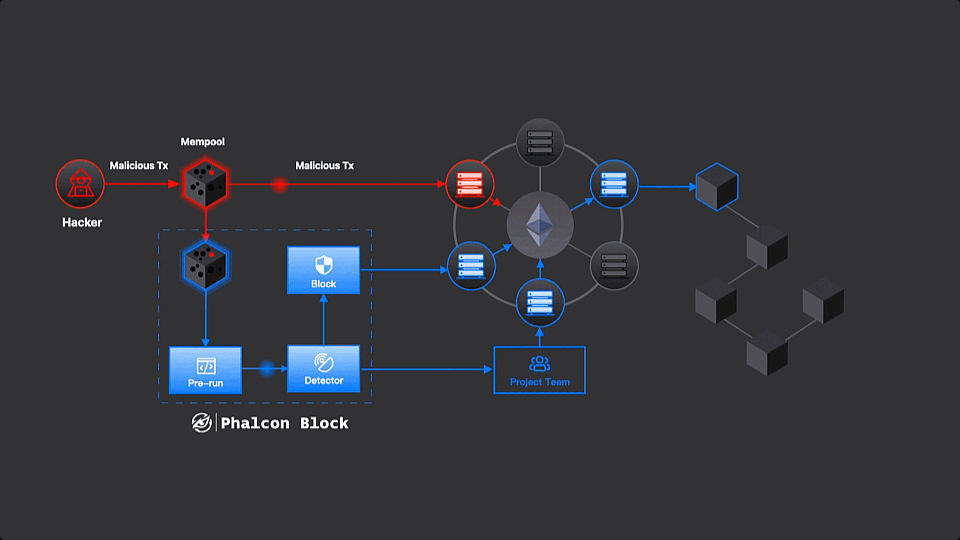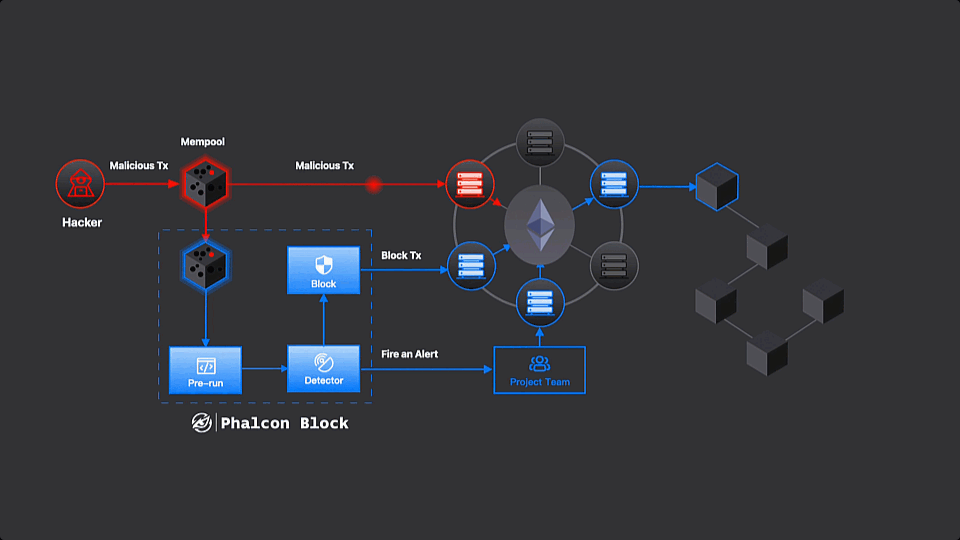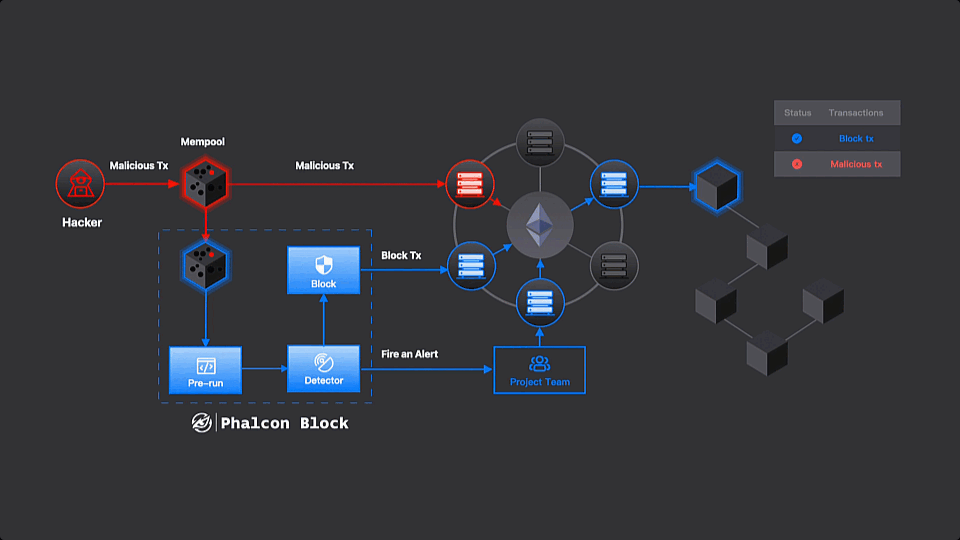
Phalcon Block in Action
Step 1: Monitoring
Phalcon Block monitors the mempool, where every transaction starts its journey. Employing a variety of techniques, Phalcon Block meticulously analyzes and simulates each transaction destined for protocol smart contracts before reaching the “validation” phase. This process classifies transactions into three categories:
- Attack Transaction: Transactions falling into this category are deemed highly likely to be malicious, posing a threat to exploit the protocol.
- Suspicious Transaction: Transactions categorized as suspicious indicate a significant probability of attempting to exploit the protocol.
- Regular Transaction: Legitimate transactions that pose no harm to the protocol or its users fall into this category.
Step 2: Blocking
Before a transaction gets the green light (validated and included in the next block), Phalcon Block takes the lead. It sends a special “block transaction” with a higher priority (higher gas). This transaction gets confirmed first before any malicious transactions are executed.
The block transaction can do a couple of things. It might be a pre-signed admin transaction, hitting the pause button on the protocol temporarily. Or, it could be a quick attempt to copy the attack faster than the original malicious transaction, saving and rescuing the funds in the process.
Replicating Hundred Finance $7 Million Hack
In April 2023, Hundred Finance experienced a significant hack, losing $7.4 million to an attacker who utilized a flash loan attack to manipulate token exchange rates and drain value from the protocol. The attacker exploited a vulnerability in the hTokens contracts, specifically targeting an unused and empty contract that manipulated the exchange rate, allowing the attacker to drain all the funds from the protocol.
Hundred Finance Shut Down After the Exploit
Today we will deploy the identical vulnerable protocol on Binance Smart Chain. Our objective is to replicate the earlier attack on this simulated protocol and assess Phalcon Block’s capability to identify and block the attack. We deployed the Hundred finance vulnerable contracts in the following addresses: Unitroller, Comptroller, and hToken.
Monitoring The Contract in Phalcon Block
First, let’s add our contracts to Phalcon Block, we want to monitor the hUSDC contract which holds the liquidity (USDC tokens) and this is the contract that was exploited in the original hack. In the Phalcon block we will go to contracts: Adding a new contract to Phalcon Block
Adding a new contract to Phalcon Block
Then we will click the “Add New Contract” button and fill in all the details: Adding a new contract to Phalcon Block
Adding a new contract to Phalcon Block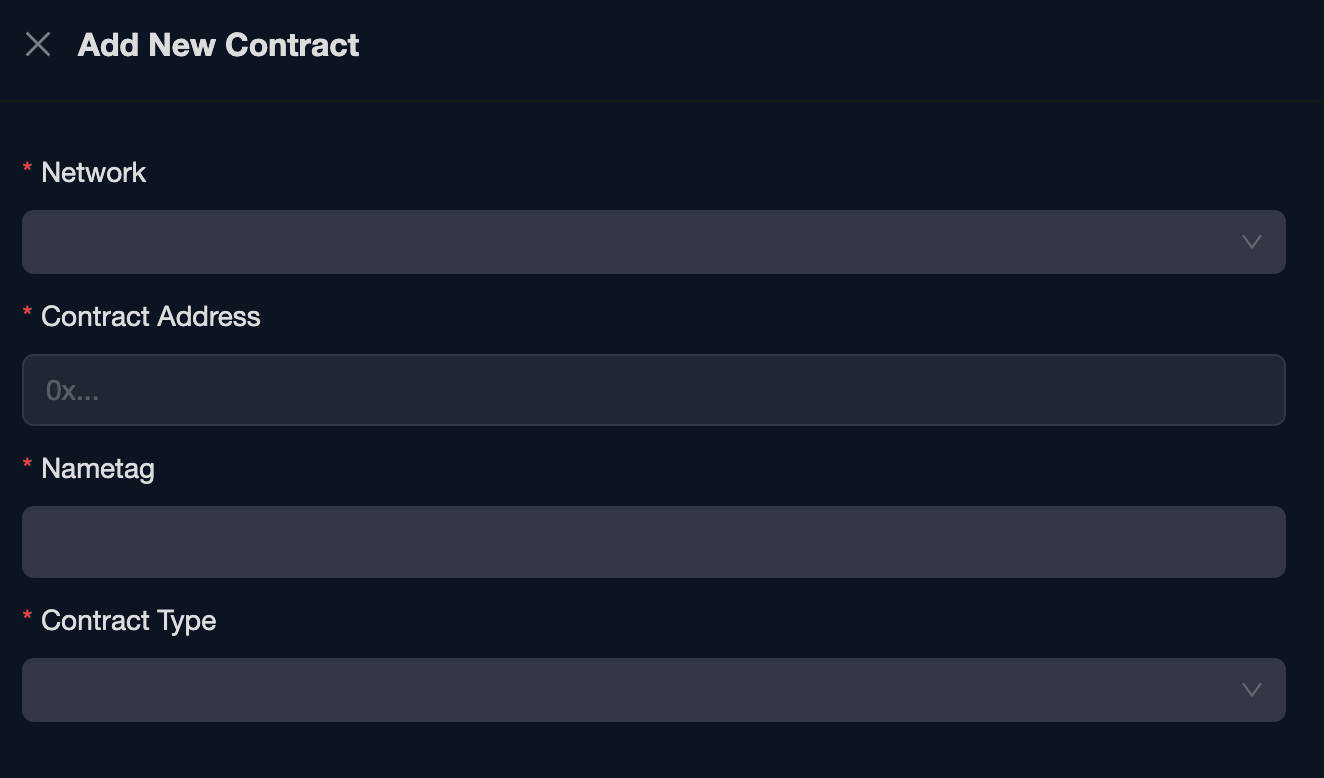 Adding a new contract to Phalcon Block
Adding a new contract to Phalcon Block
And now we can see that the contract was added:
Phalcon Block Contracts
Once our contract is added to the system it’s time to define a monitoring rule, in the main menu we will click monitor, and then the “Create New Monitor” button:
Creating a New Monitor in Phalcon Block
We will select our contract and then create “Create Now” to create a new monitor rule: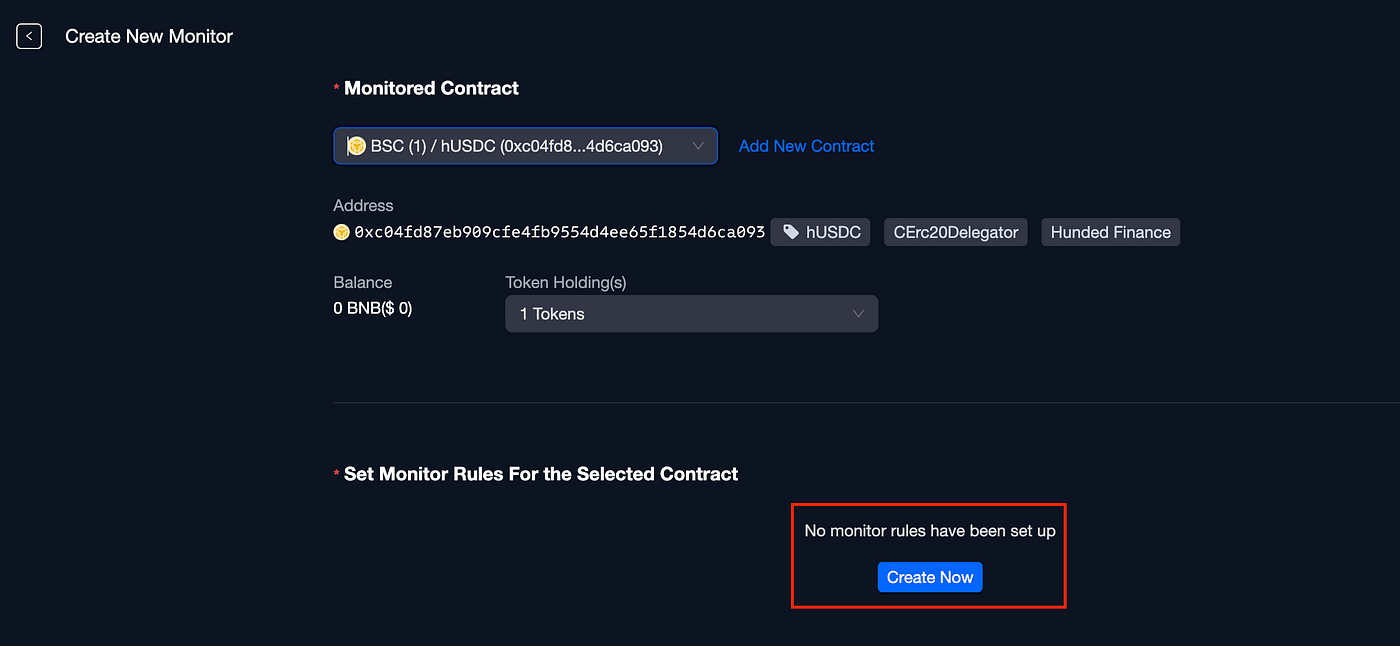
Creating a New Monitor in Phalcon Block
We have flexibility when it comes to things that we can monitor in our smart contract, in our case we will monitor if the liquidity is “leaving” our contract, so we will choose the “Token Amount” monitor and click Next: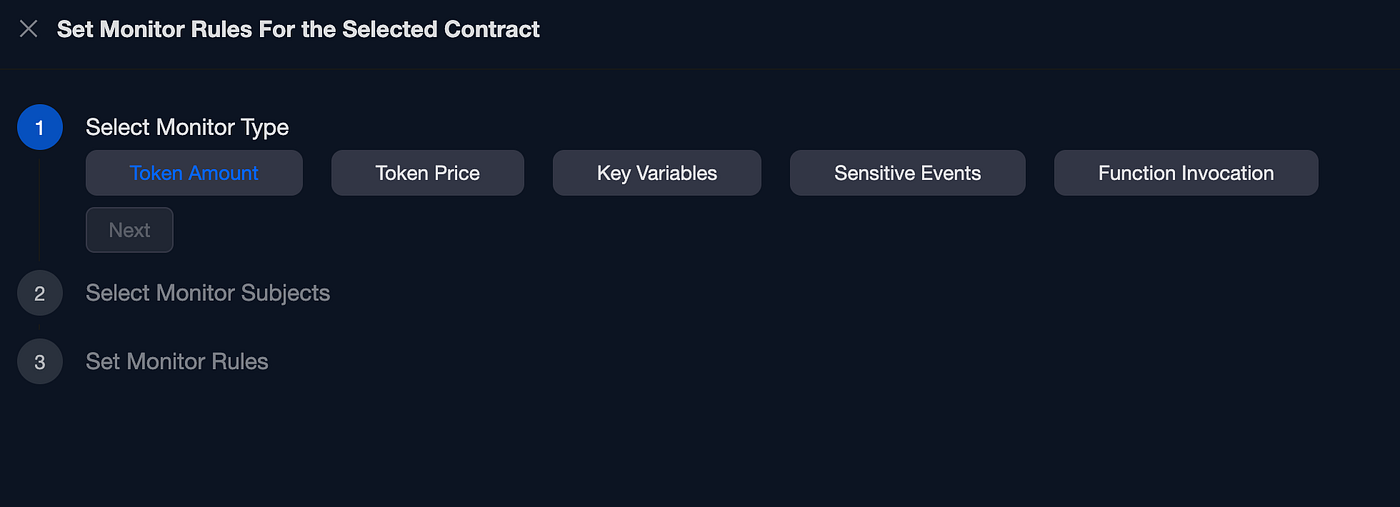
Monitoring contract’s Token Balances
Next, we’ll pick the USDC token and opt for “Attack Tx,” focusing solely on transactions marked as “Attack Transactions” by the Phalcon Engine. Following that, we’ll specify that if the USDC token balance within the hUSDC contract decreases by over 1%, we intend for this monitor rule to activate: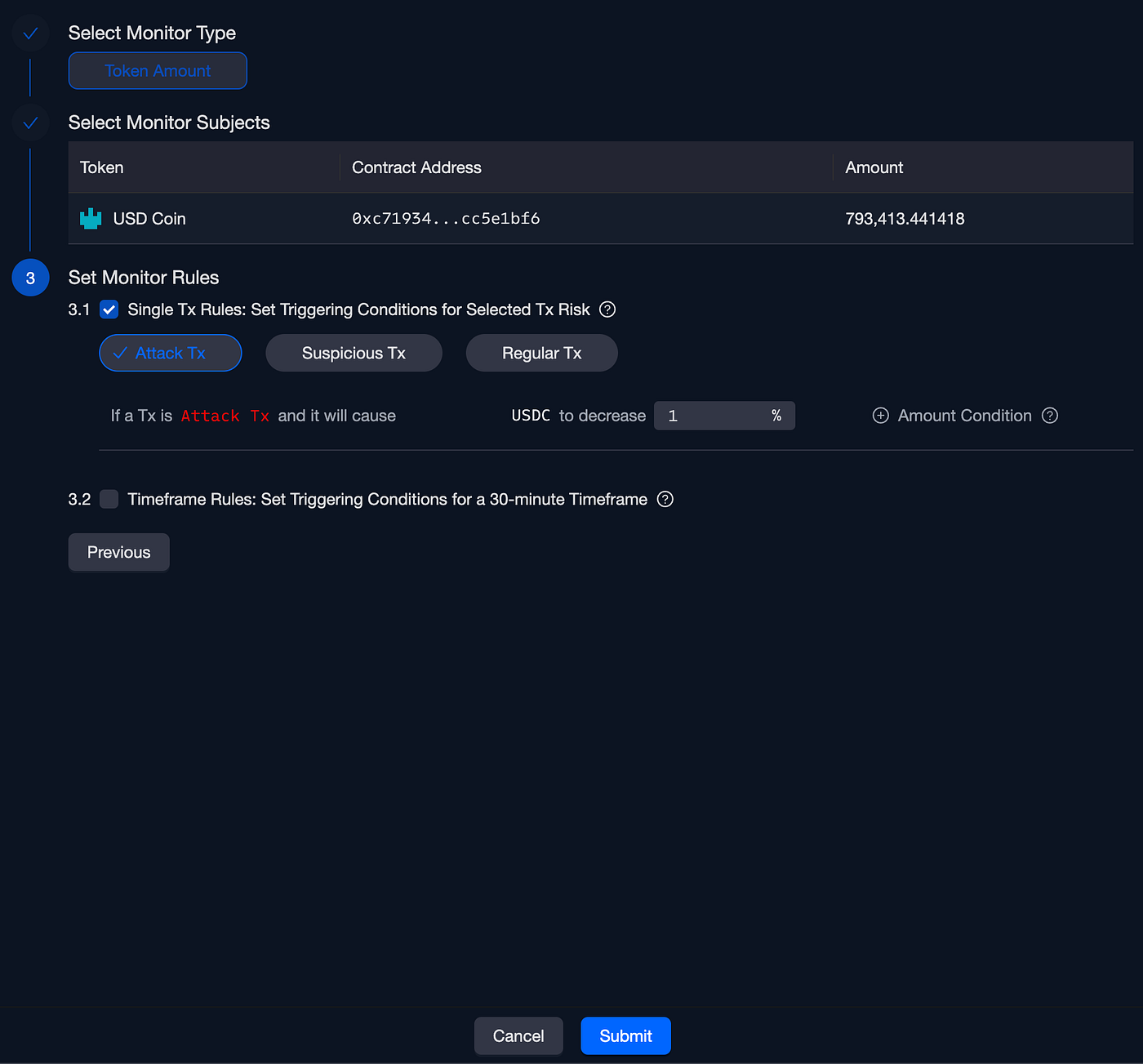
Configuring our Monitor Rule
Now if we scroll down we can configure a “Notification Channel”, and we can add different channels, Phalcon Block supports Email, Telegram, Webhook, and Slack notifications: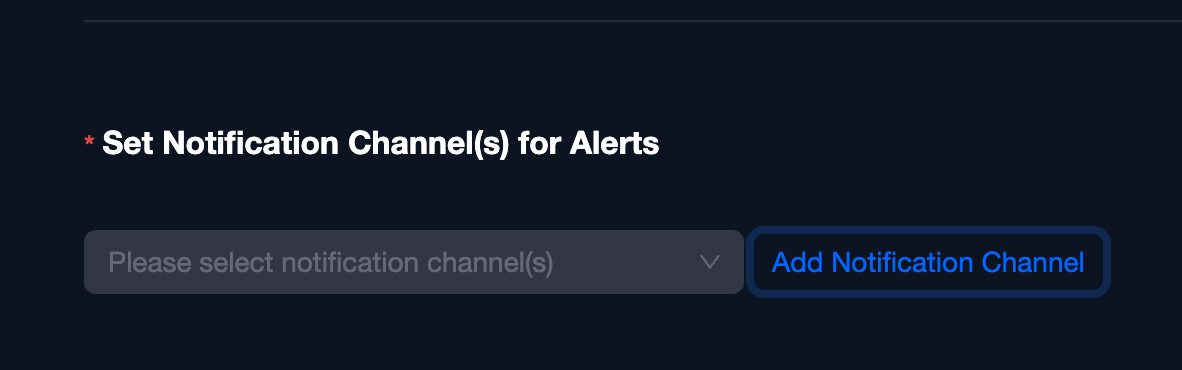 Adding a notification channel
Adding a notification channel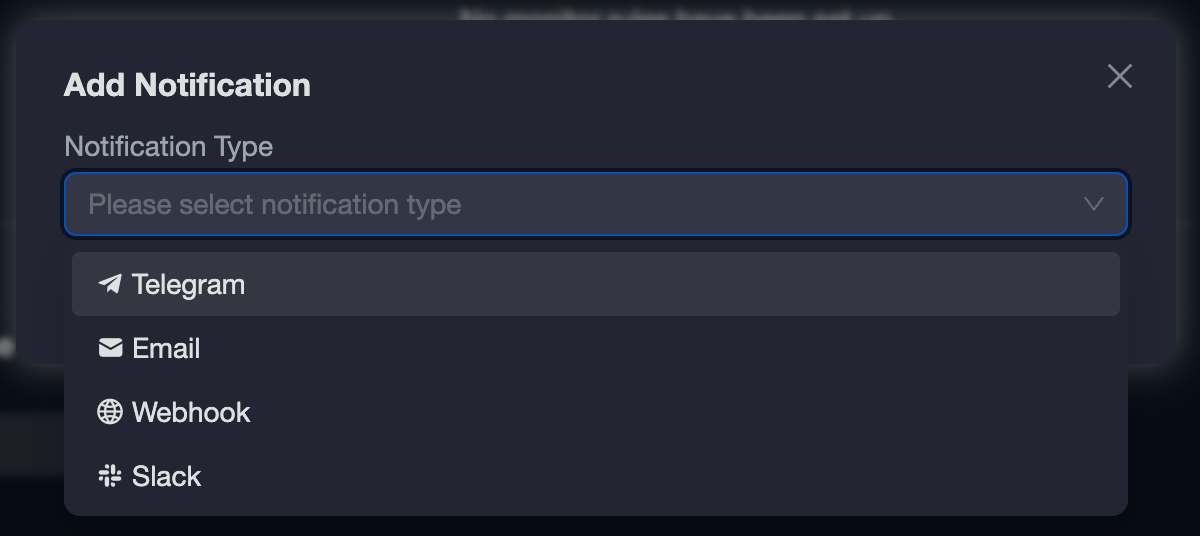
Creating a New Notification Channel
Adding Automatic Defense
Great! Now we don’t want only to monitor the attack but we want also to automatically block it! Let’s head over to the Defense section on the website and create a new Defense: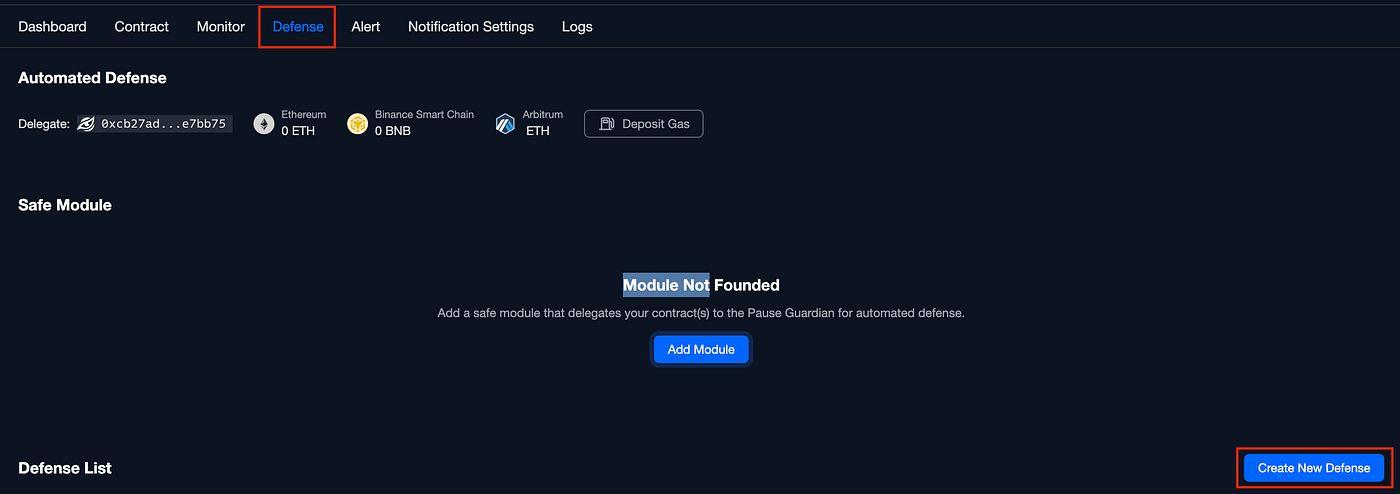
Phalcon Block: New Defense
In our defense we’re going to pause all the lending pools so in case there is an attack it will fail, let’s add a name and a description: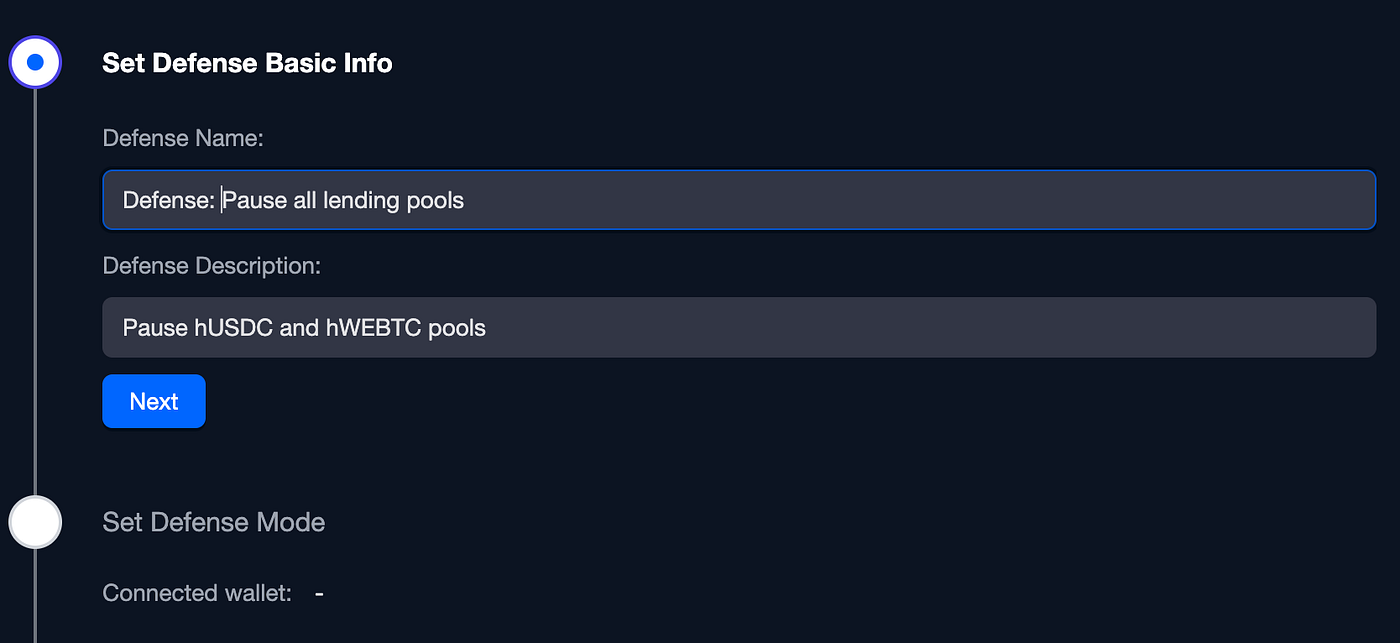
Defining our New Defense
Now we can choose our Defense Mode, wither “Pre-signed Transaction” or “Delegate Mode” we are going to choose Pre Signed transaction that we will prepare in advance using our Guardian account. Then we will select BSC as the network and paste our Guardian EOA account address: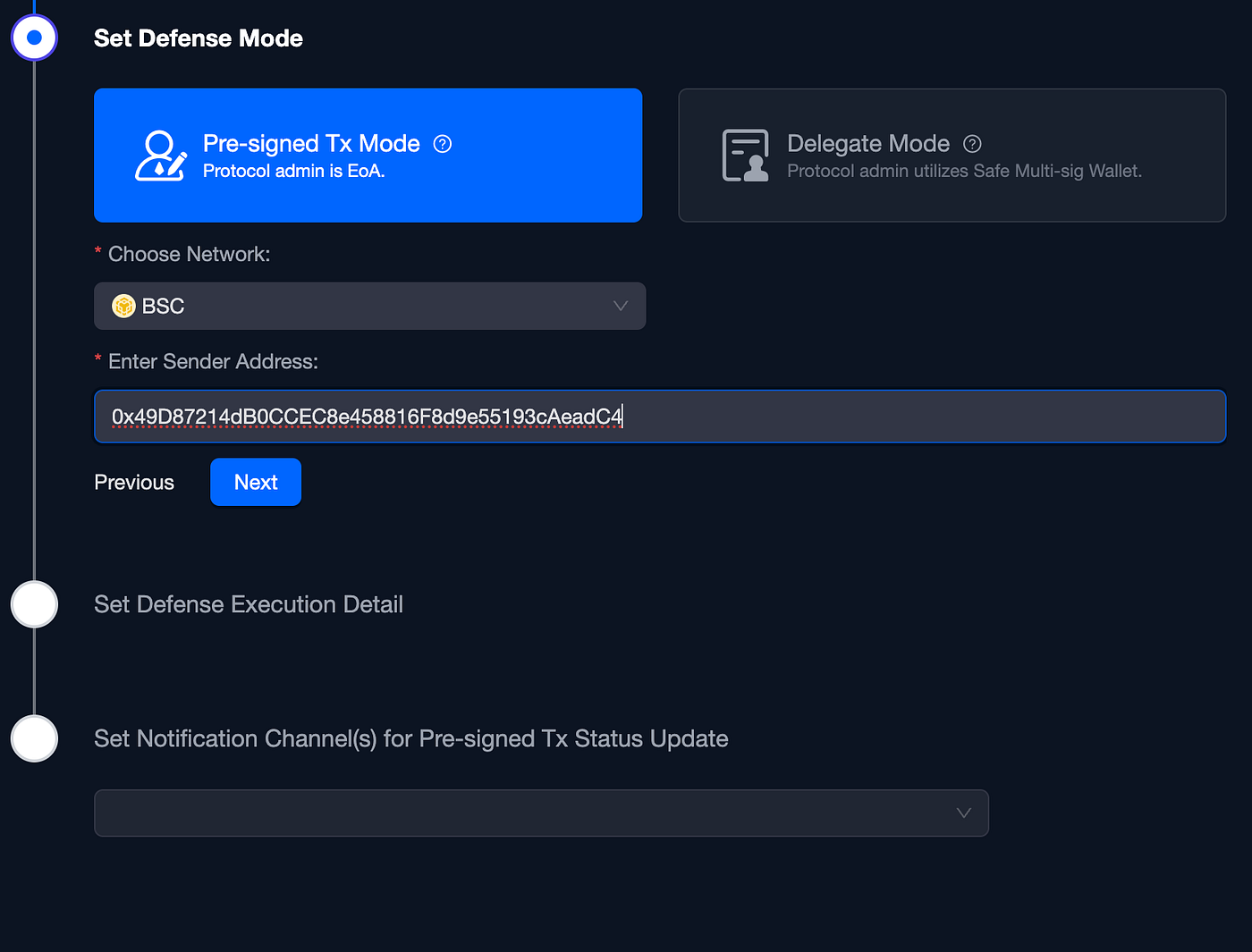
Pre-signed Transaction Defense Mode
We can now incorporate our pre-signed transaction. Earlier, we created a script to generate and sign a transaction capable of pausing the hUSDC and hWBTC.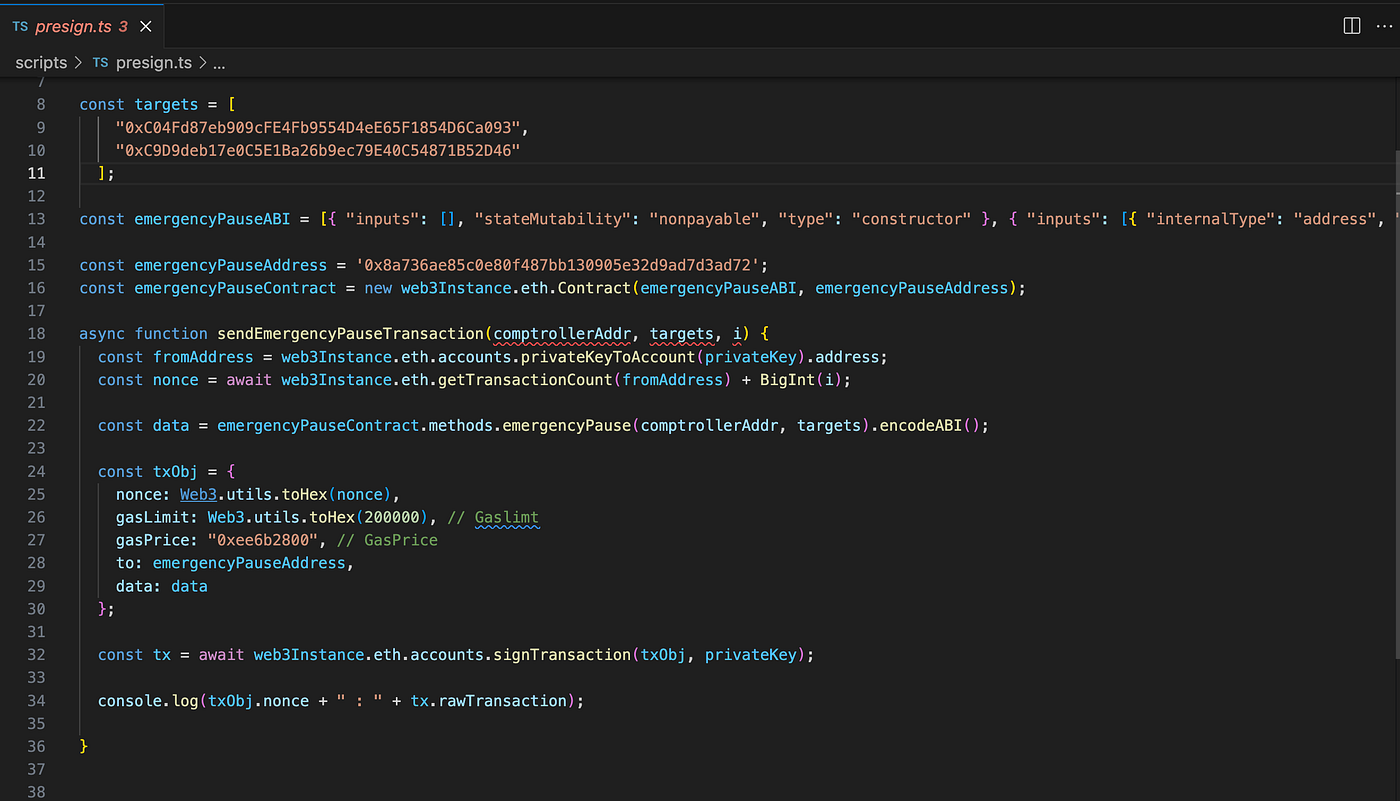
Script to Pre-sign the Pause Transaction
Ensure the transaction carries the correct nonce; Phalcon Block retrieves the latest transaction from the blockchain, indicating the current nonce. Additionally, you have the flexibility to include multiple pre-signed transactions. Should one transaction be utilized, Phalcon Block seamlessly moves on to the next one in the list: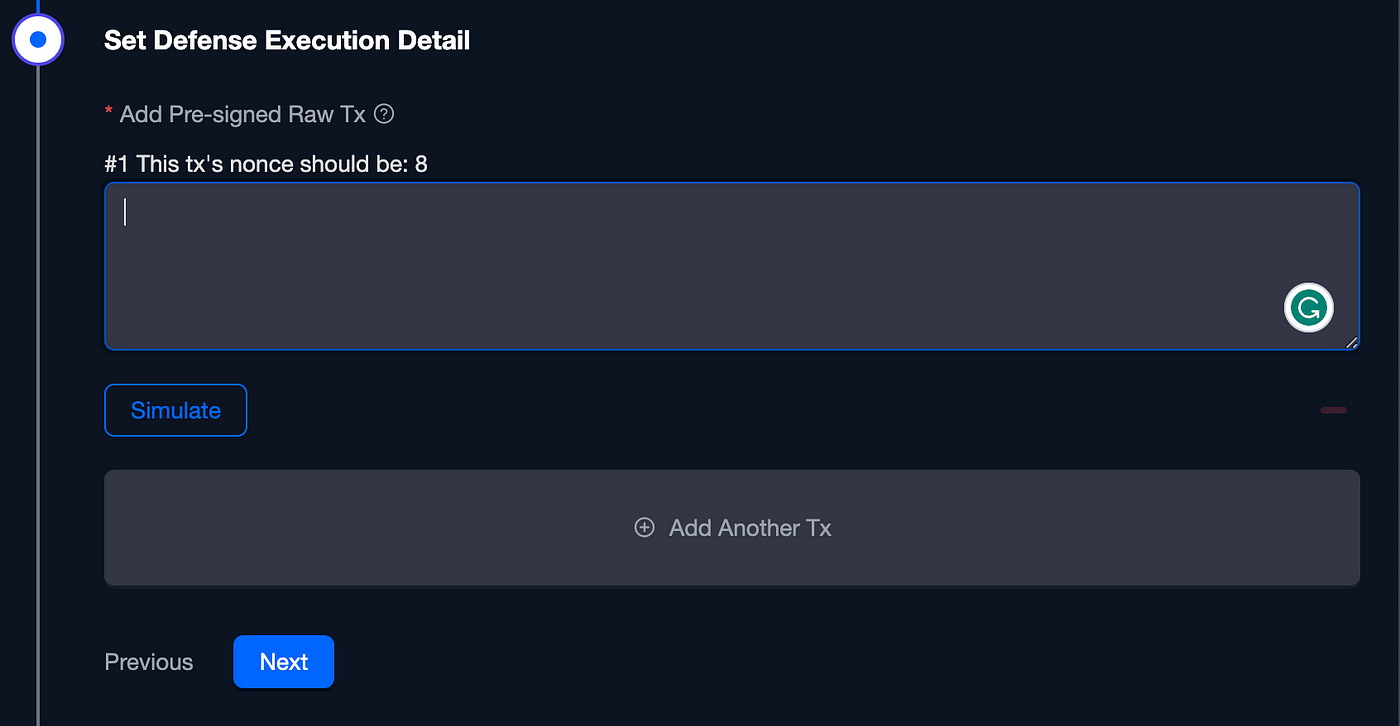 Adding our pre-signed transaction
Adding our pre-signed transaction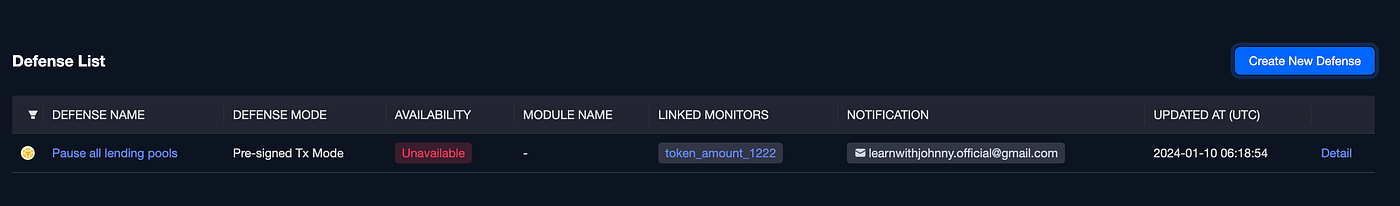
Our New Defense was Created!
The final step involves linking the new defense we crafted to the previously created monitor rule. This can be done by editing the monitor rule and integrating the new Defense: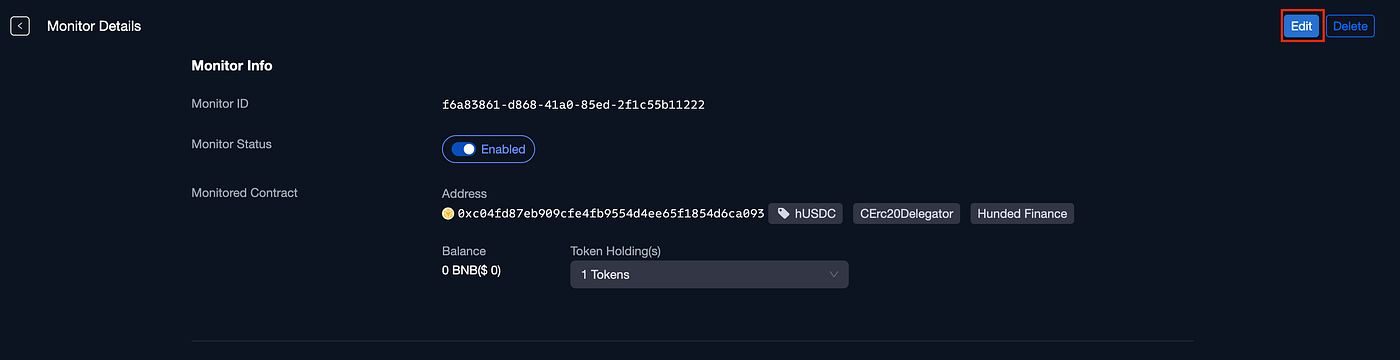
Editing the monitor rule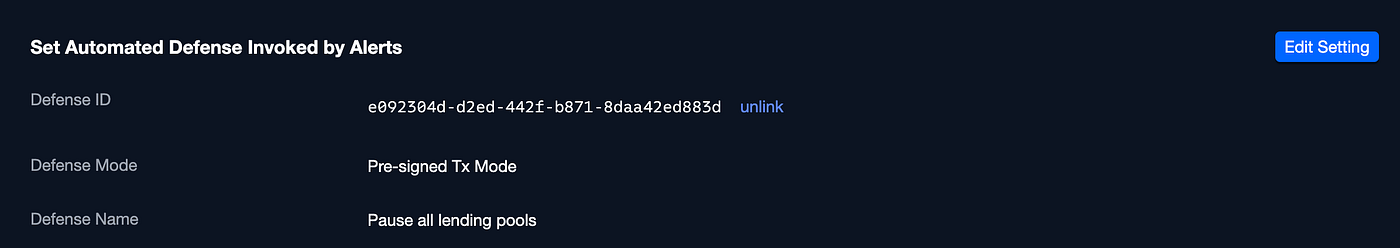
Attaching the new Defense
Launching the Attack
Now it’s the money time! We will try to replicate the same attack, steal the USDC tokens from the hUSDC smart contract, and see whether Phalcon Block can detect the attack and block it!
Our Attack Script
We will launch our attack script and let’s see what happens: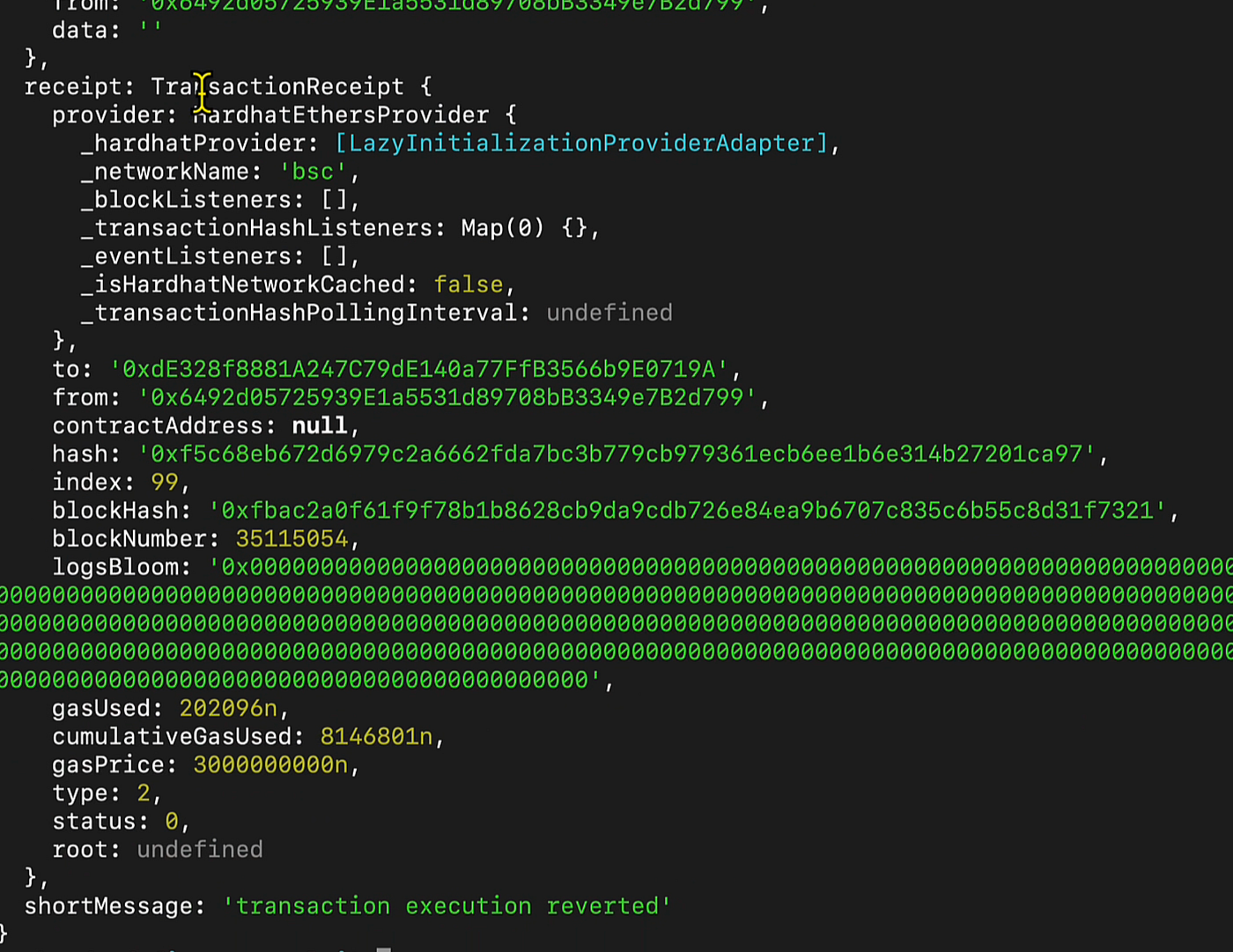
Error While trying to execute the attack
Excellent! Our attack script didn’t succeed, and the transaction execution was reverted. This likely occurred because the Phalcon Block tool initiated a pause on the pools. Let’s verify this assumption…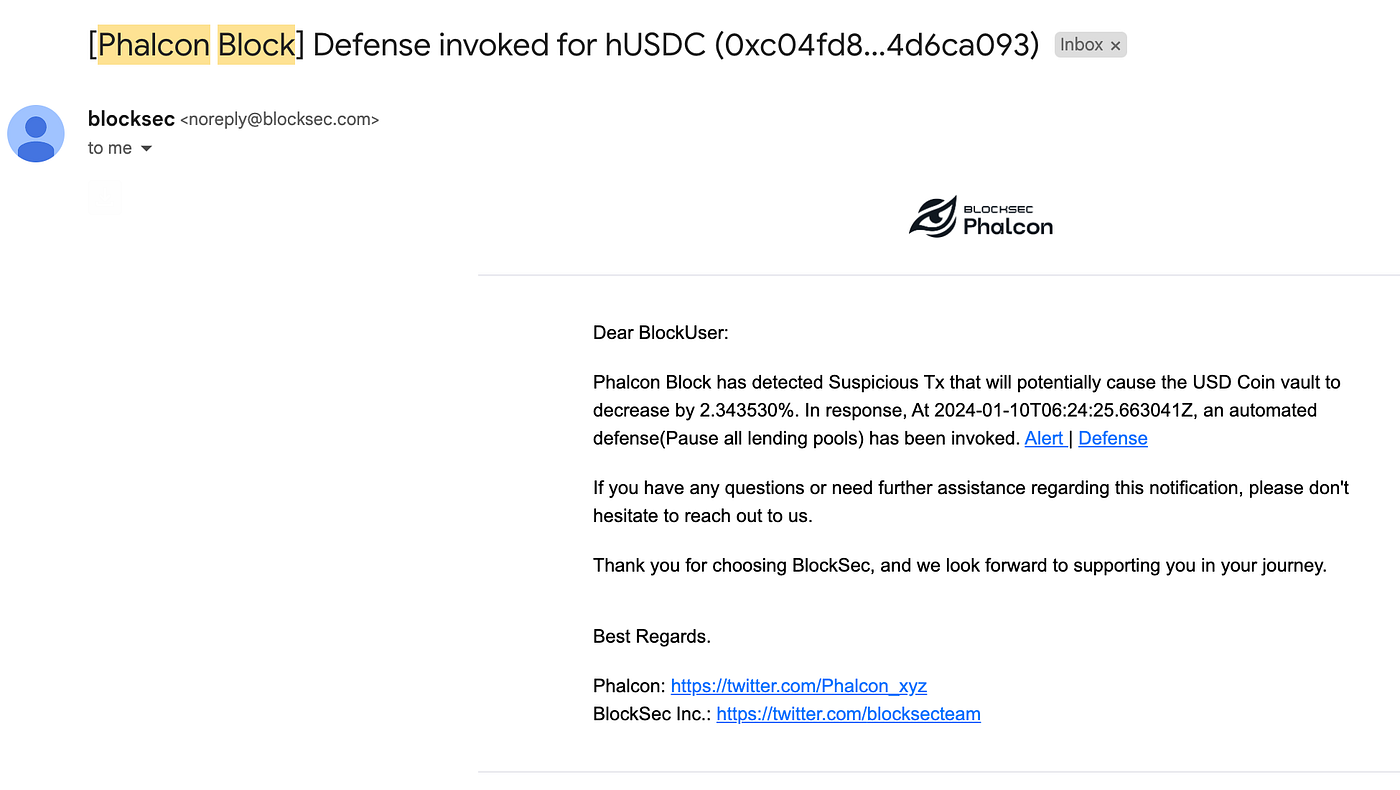
Email from Phalcon Block
We received an email that Phalcon Block has identified a suspicious transaction that might lead to a 2.34% decrease in the USD Coin. In response, an automated defense, “Pause all lending pools,” was triggered at a specific time. Let’s click the defense link and see what happened!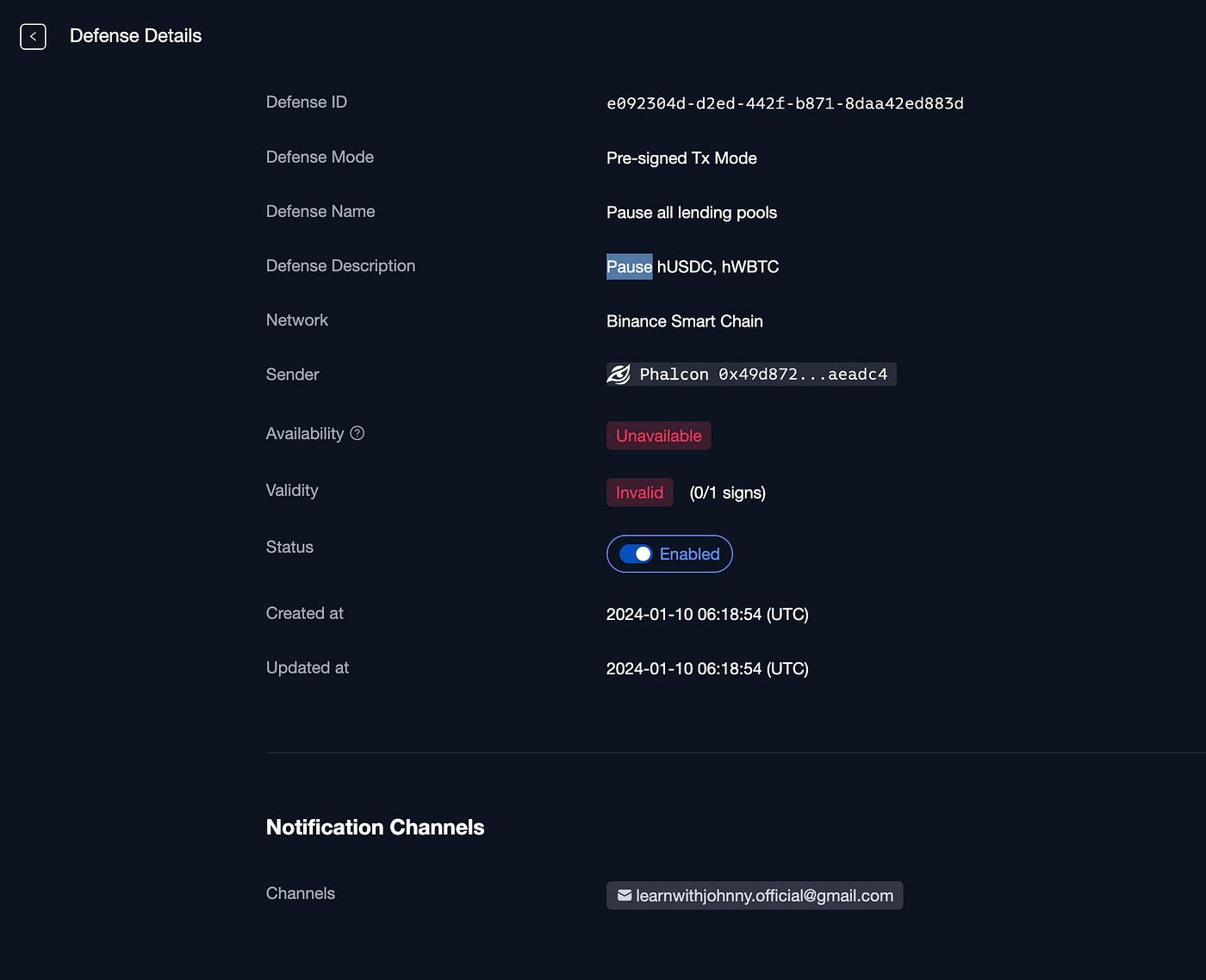
Phalcon Successfully Blocked the Attack
We can also analyze the malicious transaction in Phalcon Explorer and see that it failed due to the fact the “minting is paused” because the pause transaction was mined before the attack transaction 💪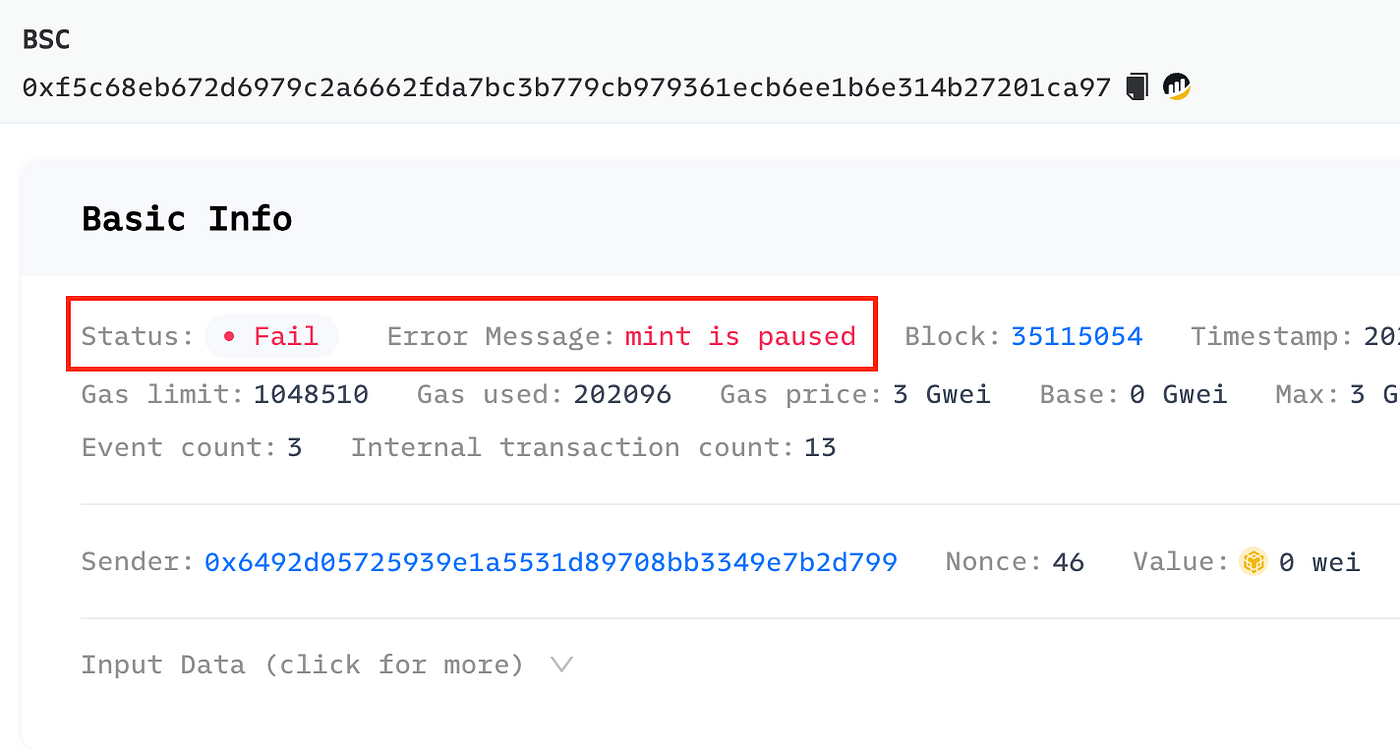
Attack was Blocked by Phal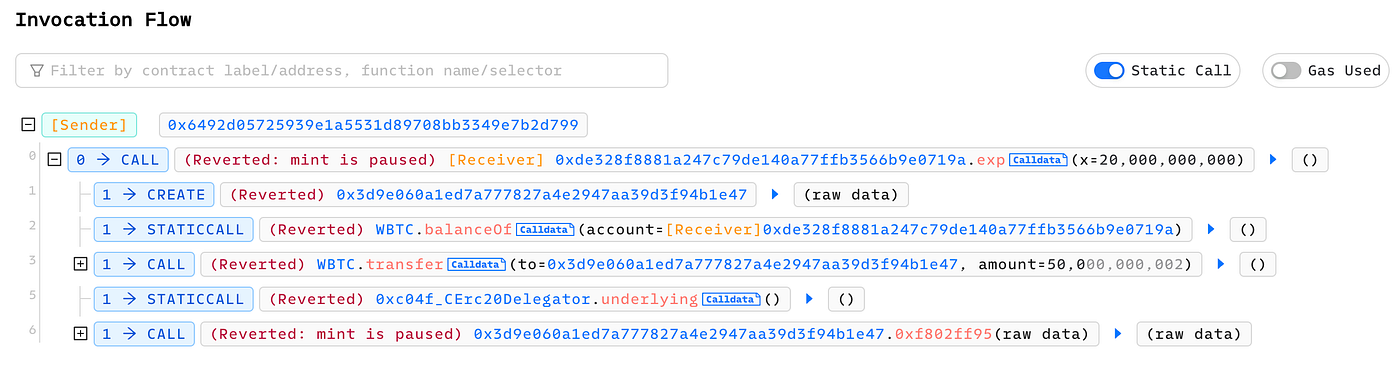
Attack was Blocked by Phalcon
As you can see the attack transaction failed to transfer the WBTC tokens because the pools were paused.
As I mentioned before, Phalcon Block is currently in beta mode and operating on a waiting list basis. If you wish to expedite your access to this cutting-edge tool, utilize this special link: https://johnnytime.xyz/phalcon-block-johnny-vip
By doing so, the BlockSec team will promptly review your request, potentially accelerating your access approval. You will have the chance to experience Phalcon Block firsthand and be among the first to benefit from its innovative features.
Summary
- We explored BlockSec’s Phalcon Block, a tool with a proven record of blocking over 20 real-world hacks and rescuing $14 million in assets for Web3 protocols.
- Phalcon Block excels in accurate attack detection, scanning transactions with algorithms for minimal false positives, providing 24/7 security without human intervention.
- Phalcon Block initiates a blocking transaction faster than attackers, allowing users to configure responses to specific attack types.
- Phalcon Block monitors and classifies transactions (Attack, Suspicious, Regular), preemptively blocking potential attacks before validation.
- We recreated the $7M Hundred Finance hack, testing Phalcon Block’s ability to detect and block on Binance Smart Chain.
- Phalcon Block successfully blocks a replicated attack, triggering an automated defense that pauses lending pools.