OSINT Unleashed: 5 More Tools For Cyber Investigators
We’re back with more essential tools for all investigators, both professional and hobbyists.
In this article, we initially explored fundamental tools that were able to be be used for various purposes, being useful for enumeration of websites and sourcing of open source information. Today, we’ll be looking at some more useful tools that can be used for these purposes. With everything from RF analysis to hard drive inspection tools, if your area of interest is cyber or information security then you’ll be bound to find something of interest.
What can they Do and Why are they Needed:
As we’ve explained previously, before we can effectively select and use tools, we need to understand what we are able to do with them and what we are looking to achieve by using them. With many tools for dozens of specialized tasks, it’s easy to get lost in a sea of information when you’re looking for the things you need to set your investigative environment. While you can look at using pre installed environments designed by some one else, there’s a distinct advantage by setting and developing your own workflow.
Because of this when we’re looking and using our tools, it’s important we understand our goals and how we are going to implement them. If you’re simply looking for a quick search result, or doing singular tasks you might like web interfaces and streamlined methods of achieving your goals. However if you’re a power user or are looking to grow your technical skills then you may be more comfortable using or learning to use a terminal, or if you’re particularly adept you may even look to write your own scripts and codes specifically written for your own situation and purposes.
Our tools today will be a mixture of wifi, disk and video analysis along with a sneaky little tip for increasing your security while carrying out your searches, so let’s get started.
Aircrack-NG
More a package of tools rather than a singular program, Aircrack-ng is a popular suite of tools used for wireless network security assessment and analysis. It’s commonly used by penetration testers, security researchers, and network administrators to identify vulnerabilities and weaknesses in wireless networks. The suite primarily focuses on assessing the security of WEP and WPA/WPA2-PSK (Pre-Shared Key) protected networks.
Aircrack-ng includes several tools that collectively assist in various aspects of wireless network security assessment:
- airmon-ng: This tool is used to enable and disable monitor mode on wireless network interfaces. Monitor mode allows the capture of wireless packets without being connected to any specific network, which is essential for capturing traffic for analysis.
- airodump-ng: Airodump-ng is used to capture raw 802.11 frames from wireless networks. It collects information about nearby access points (APs) and connected clients, including MAC addresses, signal strength, channel, encryption type, and data rates.
- aireplay-ng: Aireplay-ng is used for packet injection and replay attacks. It can generate artificial traffic to stimulate interaction with target networks and clients, which is useful for certain types of attacks, such as deauthentication attacks.
- aircrack-ng: The namesake tool of the suite, aircrack-ng, is used for cracking WEP and WPA/WPA2-PSK encryption keys. It uses captured packets to perform brute-force or dictionary-based attacks to recover the passphrase of a protected network.
- airdecap-ng: This tool is used to decrypt WEP and WPA/WPA2 encrypted traffic. It requires the network’s encryption key to be known or cracked using other tools.
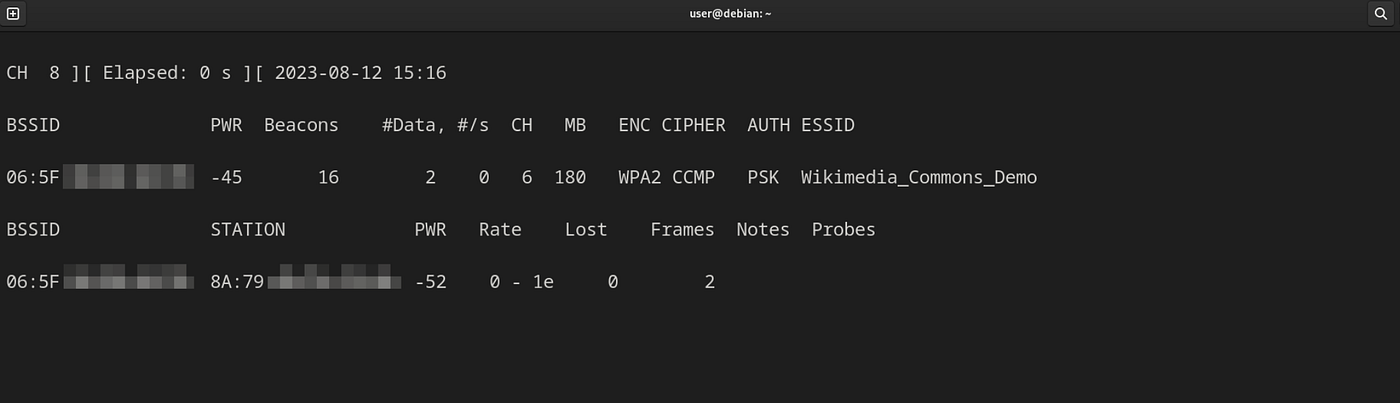 Aircrack-ng is a useful, command line based package for Wifi Interception. Source: Wikipedia
Aircrack-ng is a useful, command line based package for Wifi Interception. Source: Wikipedia
Kismet Wireless
Kismet Wireless is a widely used open-source network detection and intrusion detection system designed to monitor and analyze wireless network traffic. It provides comprehensive insights into various aspects of wireless networks, including detecting and identifying nearby access points, clients, bluetooth devices and their associated information. Kismet is known for its ability to capture and decode data from a wide range of wireless protocols, making it useful for both security professionals and enthusiasts. It aids in identifying unauthorized or potentially malicious devices on wireless networks, allowing administrators to take appropriate actions to secure their networks. Kismet’s versatility and robust feature set make it an essential tool for wireless network monitoring, analysis, and security assessment and it’s one of our favorite tools to operate on the go. Kismet + Pi Zero + Wifi Card & SDR Dongle= Data galore.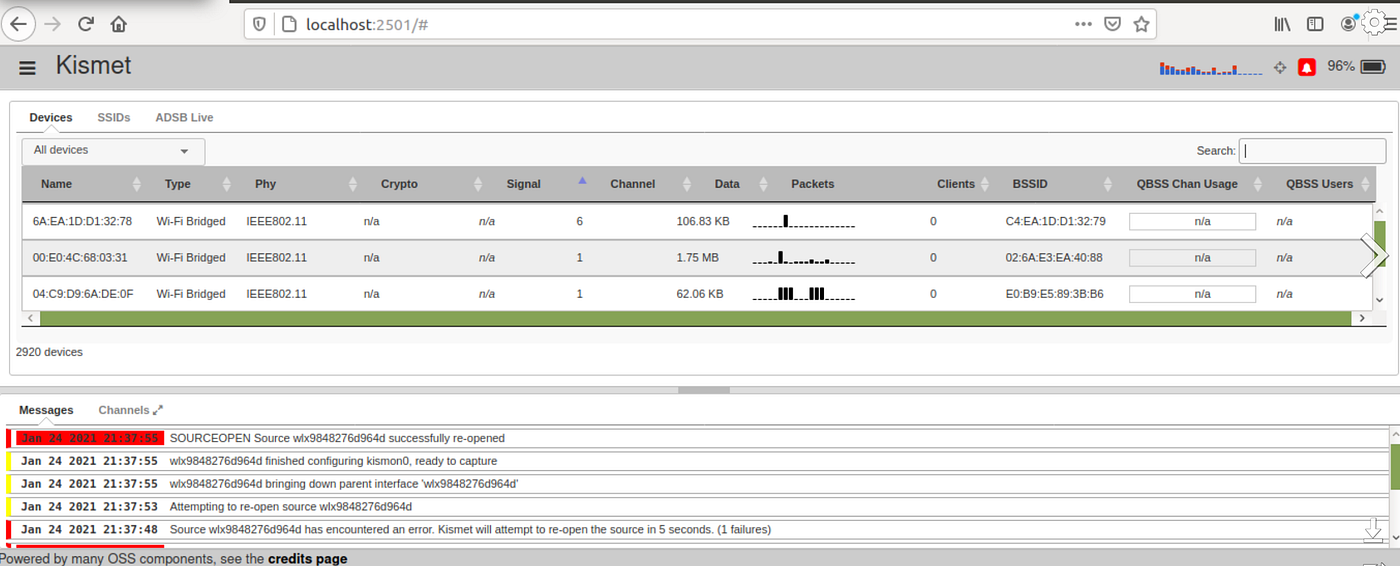 Kismet’s Web GUI. Source: Wikipedia
Kismet’s Web GUI. Source: Wikipedia
Autopsy
Autopsy, an open-source digital forensics marvel, isn’t just software. It’s the key to unlocking untold stories woven into the fabric of data. Its interface is a bridge between complexity and user-friendliness, welcoming both seasoned investigators and curious minds into its world. While learning to navigate the package might take some effort for beginners, it’s ability to piece together lost data fragments, decode intricate file systems and swiftly unearth information make it an essential tool for those conducting data recovery or analysis. A standard package on a Kali Linux install, autopsy can even recover your own lost images or files!
Probably the biggest advantage autopsy offers however is it’s clean investigative workflow that’s built in to the GUI of the software. Offering clearly marked processes with a well document workflow thats usable for evidence purposes, Autopsy is a must learn tool for hackers, digital investigators and cyber sleuths. Autopsy can even recover your own lost files. Source: kali.org
Autopsy can even recover your own lost files. Source: kali.org
Exiftool
ExifTool is a versatile and indispensable command-line tool designed for managing and extracting metadata from various types of digital files, particularly image files. This tool allows users to view, modify, and manipulate metadata embedded within files, such as EXIF (Exchangeable Image File) data found in images captured by digital cameras.
The significance of ExifTool lies in its ability to extract a wealth of information hidden within files. From camera settings and timestamps to geolocation coordinates, ExifTool provides insights that go beyond the visual content of an image. This becomes crucial in scenarios where accurate metadata is essential, such as in photography, forensics, archiving, and digital asset management.
With ExifTool, users gain the power to correct errors, adjust metadata, and this extract valuable information for further analysis. This tool’s support for a wide range of file formats make it an invaluable asset for professionals seeking accurate data preservation and in-depth analysis.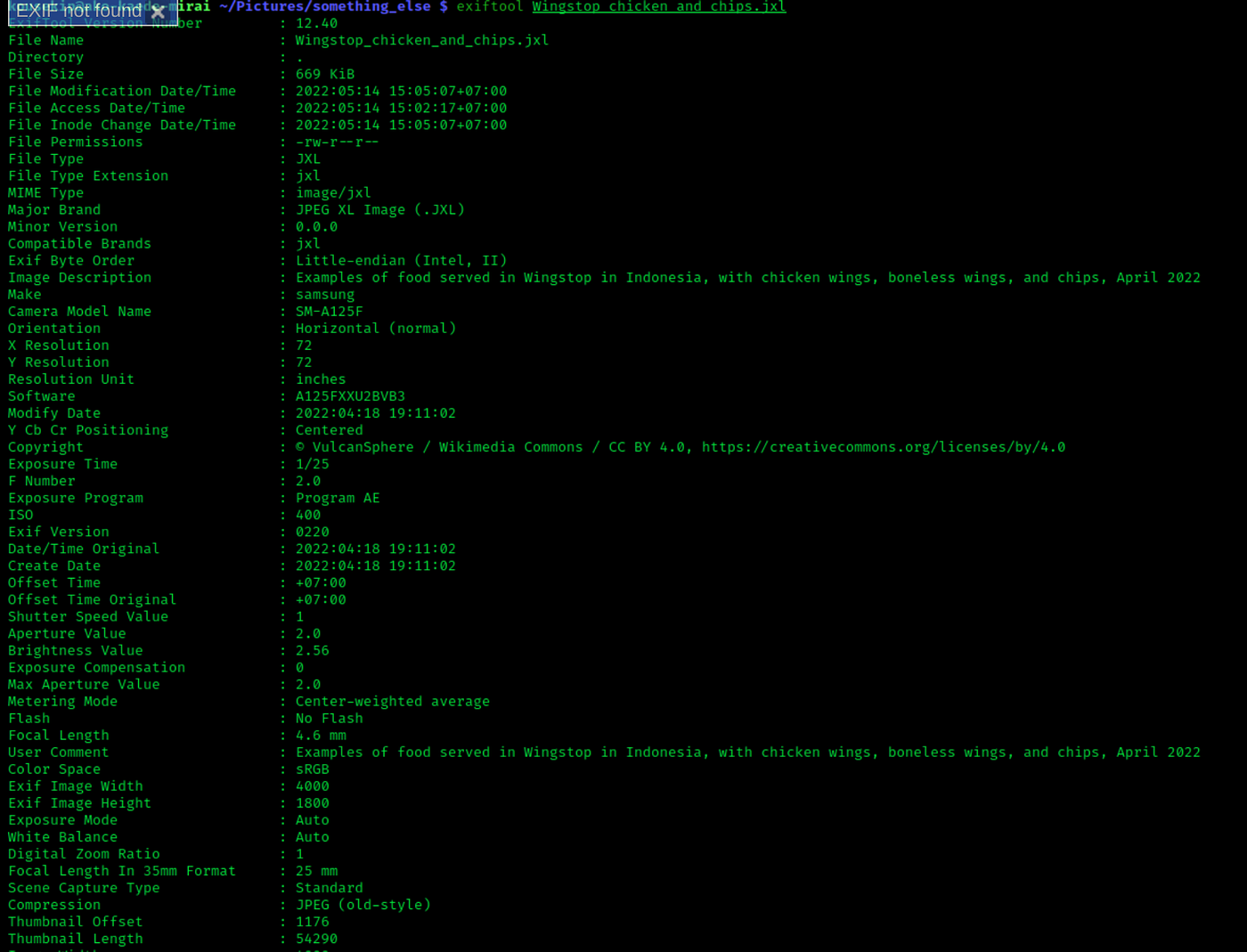 Exiftool aids in capturing the metadata that’s embedded within media. Source: Wikipedia
Exiftool aids in capturing the metadata that’s embedded within media. Source: Wikipedia
Virtual Box
More a defensive tool than an offensive weapon, VirtualBox is a powerful and widely-used open-source virtualization software that allows users to create and run virtual machines on a single physical host computer. These virtual machines emulate independent operating systems, enabling users to run different OS environments simultaneously without the need for separate hardware.
For online investigators, VirtualBox gives us a crucial advantage. It provides a controlled and isolated environment to conduct digital investigations, cybersecurity assessments, and various online research activities. Here’s a few reasons why we should use VirtualBox:
- Isolation and Security: VirtualBox creates a sandboxed environment, isolating the virtual machine from the host system. This is invaluable for analyzing potentially malicious files, websites, or software without risking the integrity of the investigator’s main system.
- Safe Testing: Investigating suspicious links, files, or software in a virtual machine ensures that any potential threats or malware don’t affect the host system. This enables investigators to analyze and understand threats without putting their own machine at risk.
- Reproducable: Virtual machines can be cloned or saved as snapshots, allowing investigators to preserve the exact state of the environment during investigations. This feature is crucial for sharing findings, collaborating with colleagues, and providing evidence in legal cases.
- Network Analysis: Investigators can set up and configure virtual networks within VirtualBox, simulating different network scenarios for analysis. This is particularly useful for studying cyber attacks, network vulnerabilities, and data breaches.
- Multiple Operating Systems: VirtualBox supports a wide range of guest operating systems, allowing investigators to analyze different OS environments without the need for separate physical machines.
- Forensics and Data Recovery: VirtualBox provides a controlled environment for data recovery and forensics analysis. Investigators can examine and extract data from various disk images or storage media safely.
As you can see, by using a virtual machine there are many advantages we obtain by operating within this secure environment. While there are some limitations to be aware of, generally speaking the benefits of operating in a sandboxxed environment generally outweigh these limitations. If you’re particularly keen you can even run Kali on virtualbox, giving you a full install with all associated tools on your everday machine. Explore virtualbox via this link Virtualbox can run full distro’s on your daily machine, fast. Source: Wikipedia
Virtualbox can run full distro’s on your daily machine, fast. Source: Wikipedia
Next Steps:
While today’s tools differ from our original article, with less web interfaces and more command line it’s important to realize that we’re still able to get started quickly and easily by using the package manager in the distro of your choice.
Using apt, we are able to install autopsy and aircrack-ng using a single command in our terminal.
To install autopsy we’d use
sudo apt install autopsy
And to install aircrack we’d use
sudo apt install aircrack-ng
and should we need assistance we can either read the manual
man aircrack-ng
and ask for a help breakdown via the command line
aircrack-ng --help
🌟 Enjoyed this article? Support our work and join the community! 🌟
💙 Support me on Ko-fi: Investigator515
📢 Join our Telegram channel for exclusive updates or,
🐦 Follow us on Twitter
🔗 Articles we think you’ll like:
- Wireshark Unleashed
- What the Tech?! Mobile Telephones
✉️ Want more content like this? Sign up for email updates here