Ukraine Update: Strava Strikes Again
The Fitness Heat Map has betrayed military secrets before. Now Strava information looks to have cost an RU Officer his life.
We’re always looking for interesting OSINT based stories, and while our content for the week is ready to go, this story was so bizarre it simply couldn’t go unnoticed. In today’s article, we’ll be looking at bad OPSEC paired with good OSINT that appears to have lead to the assassination of a Russian Submarine Commander. Let’s get to it.
The first rumblings about this event occurred on Telegram, and it took a few hours for things to filter through and information to unfold. Eventually however we saw this article linked to the event via mainstream news.
Russian commander killed while jogging may have been tracked on Strava app | CNN
A Russian submarine commander shot to death while jogging on Monday may have been targeted by an assailant tracking him…
edition.cnn.comD
It’s worth mentioning that the NATO summit at Vilnius was underway as this information was being released. Despite the attention you’d expect an event like that to bring, this headline still held it’s own in terms of the attention it drew. Searching for more information on Twitter leads us to this tweet.
For those of you with a keen eye you may notice Patron in the profile picture of that tweet. This tells us there is more to this than meets the eye. Now we have the makings of a current event news story! Let’s break down what we know. Stanislav Rzhitsky. Source: Ukraine GUR
Stanislav Rzhitsky. Source: Ukraine GUR
The Background:
Stanislav Rzhitsky was a member of the Russian Navy, or more precisely the commanding officer of a modified Kilo Class Submarine, known as the Krasnodar (B-265).
Also referred to as Project 636.3, these were an improved version of the late Cold War era Kilo Class, an extremely quiet and capable diesel electric submarine operated by several nations. Claimed by Russia to be the world’s quietest Diesel-Electric boat, the 636.3’s are particularly useful in shallow waterways, having a range around 7,500 nm. With 6, 533mm Torpedo tubes and a carrying capacity of 18 Torpedos as well as additional weapons, the 636.3 has legitimate teeth.
Krasnodar is particularly noteworthy, as it is one of the few improved Kilo Class boats that is capable of firing the 3M54–1 Kalibr Cruise Missile. 3M54–1 Kalibr. Source: Wiki
3M54–1 Kalibr. Source: Wiki
The Kalibr, which first saw extensive use over Syria has also seen further use during the Russian War in Ukraine where it has been used to conduct missile strikes on Ukrainian cities. Due to the effectiveness of Ukraine in threatening Russia’s naval assets with few ships of their own, we see that submarines became more important to Russian forces. This is because a submarine has the ability to submerge, providing a significant level of security against a country with minimal naval assets and no anti submarine warfare capability. The end result of this is that cruise missile strikes are able to be conducted with impunity due to Ukraine’s inability to prosecute naval assets past a certain point. Obviously this constitutes a problem with no immediate solution.
While Ukraine had this problem with no apparent solution, it’s worth mentioning that by day 500 of the “Special Military Operation” they were adept at creating solutions using many non conventional means. Often, this meant using technology to assist in achieving these goals. If you feel that’s an unfair comment, we’d like to quietly remind you that this is the nation that achieved the following objectives all while being attacked.
- Paired US AGM-88 HARM’s to ex soviet MiG-29 Fulcrums,
- Used Starlink to create a remote naval drone responsible for this attack,
- Used modified FPV drones as cheap, effective Kamikaze weapons,
- Adapted US designed RIM-7 missiles to fire from Soviet era Buk Launchers and.
- Modified western Storm Shadow cruise missiles to be fired from the Soviet designed SU-24.
With that said, it’s also worth mentioning they’ve made extensive use of military intelligence for strategic purposes, using intel to guide strikes on weapon dumps, chain of command structure and other hi value targets as you’d expect during a hi intensity conflict.
Strava: Fitness is King
Strava is no stranger to the limelight, being used by fitness fanatics the world over to track workouts, connect with fellow enthusiasts and provide heat mapping services based around activity. However Strava is also no stranger to controversy, with several instances over the years of sensitive information being inadvertently leaked.
To realise how big a deal this is, you need to understand the background behind OPSEC. While mobile phones have been recognized for some time due to the threat level they provide, Wi-Fi or Bluetooth based fitness trackers and other smart devices took far longer to develop a safety net and protocol around them. While they aren’t able to provide the same type of data as a GSM device, a skilled military or open source analyst can still draw many conclusions by analysing this data. For the US military, this wasn’t uncovered until 2018 when an Australia based, student analyst released this tweet. Uncovering significant parts of the US footprint within the Middle East, the information showed the vulnerability of smart devices particularly when it’s able to paired with open source intelligence techniques.
This is a great reminder of how a single individual can do significant research into certain situations using nothing more than freely available open source data to leverage information.
However to further understand the risk level behind Strava we also need to understand it also acts as a pseudo social media, allowing fitness enthusiasts to form networks, obtain friends, post workout information and follow other Strava members. You might be starting to sense how in an active warzone, this may provide some significant security issues. An image from the account of interest. Source: Strava
An image from the account of interest. Source: Strava
The Event:
Now we understand our background, we can analyse our event in further detail and try to understand what went wrong. It’s important to note before we do so however, that the fog of war is real. While we’ve taken all best measures to validate our information as true and accurate, we do need to include the disclaimer that things may change at a later date. And even if they don’t we should expect both sides to actively use information warfare techniques. This means that corroboration is extremely important, as adding to this disinformation pile is something we’d rather not do. So with that said lets check it out.
Our earlier tweet gives the game away, however for those that can’t speak Russian or read Cyrillic, our tweet of interest shows 2 screen shots.
One is a tweet from our Submarine Commander, Stansilav. It appears that he’s a Strava enthusiast who enjoys posting his pictures and workouts to Strava. Unfortunately he’s not too concerned about Op Sec like he should be, as that particular Strava account remains public. If you’d like to check it out, you can via this link which shows the last exercise uploaded. To save you the time though, we’ve enclosed a screenshot below which gives you a general idea of activity level and what’s visible.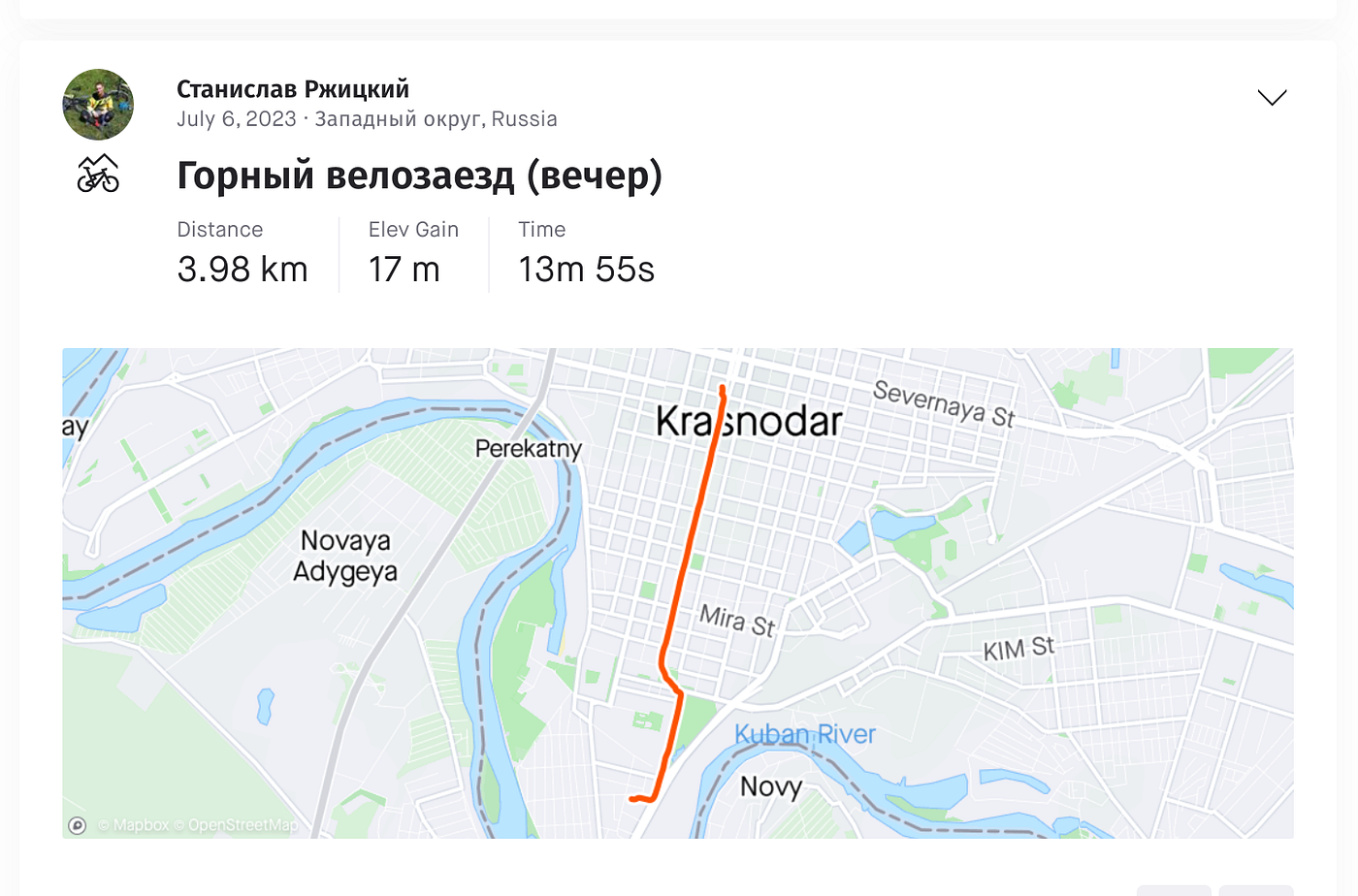 Bad Op Sec is Killer. Source: Strava
Bad Op Sec is Killer. Source: Strava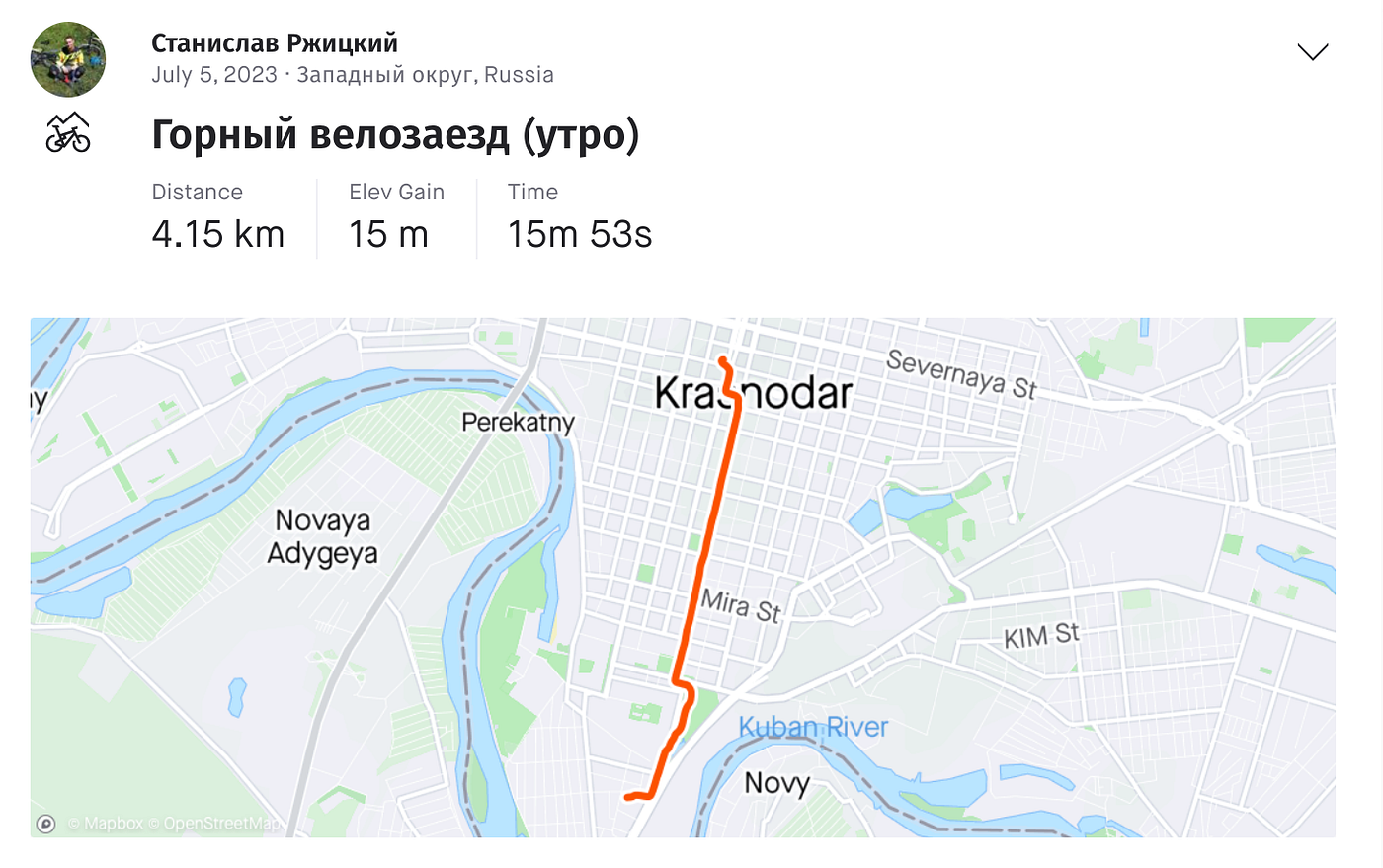 We see recurrences of the same route posted publicly. Source: Strava
We see recurrences of the same route posted publicly. Source: Strava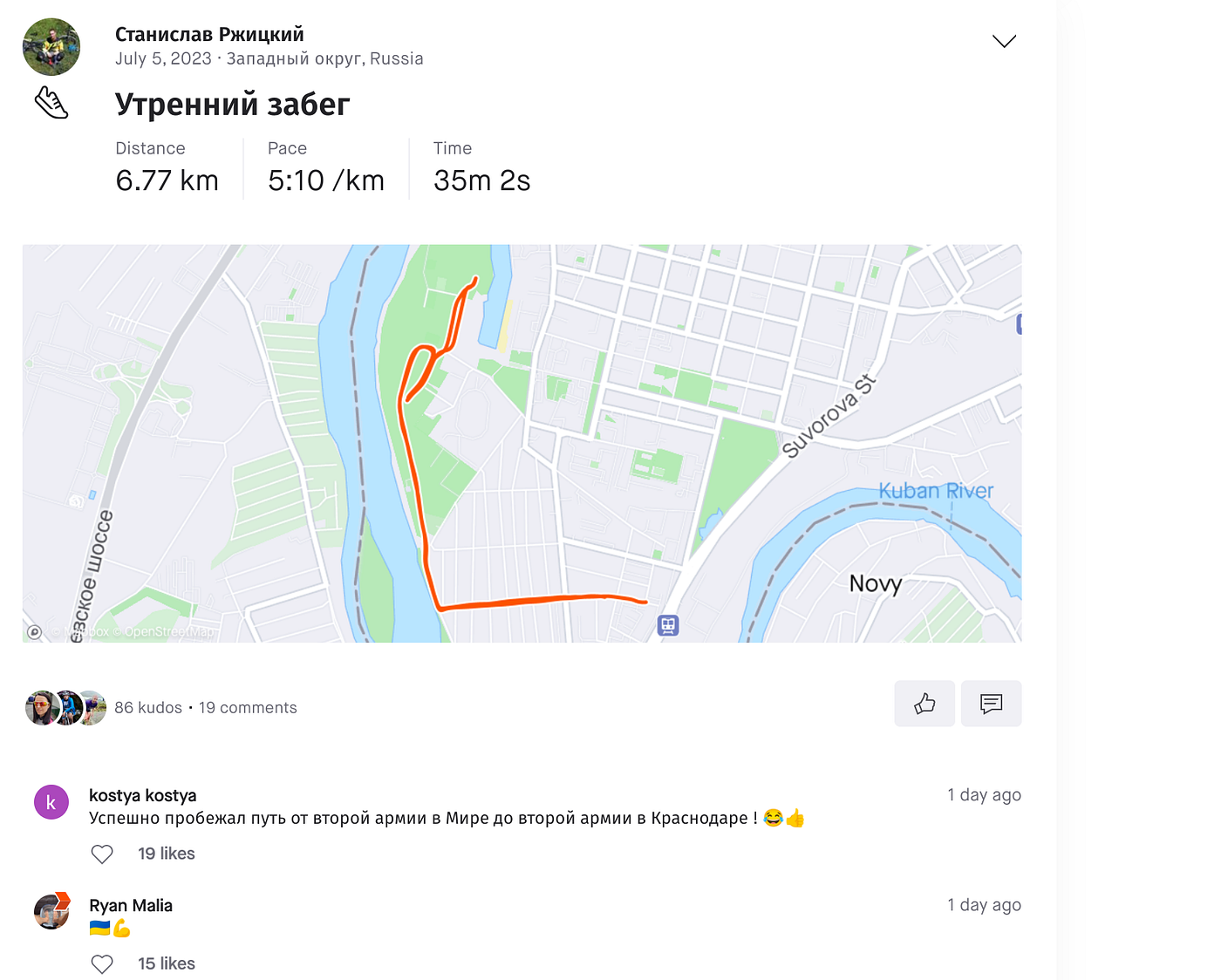 We also see pro ukraine information in the comments. This indicates a badly kept, or non existent secret. Source: Strava.
We also see pro ukraine information in the comments. This indicates a badly kept, or non existent secret. Source: Strava.
Looking a bit further at the information we see an interesting picture among the followers and kudos. That’s Patron, the well known UA detection dog, and mascot for the UXO campaign. He’s a cute Jack Russel terrier.
In case you’re Cyrillic is a bit rusty, Кирйоло Буданов translates to Kyryolo Budanov.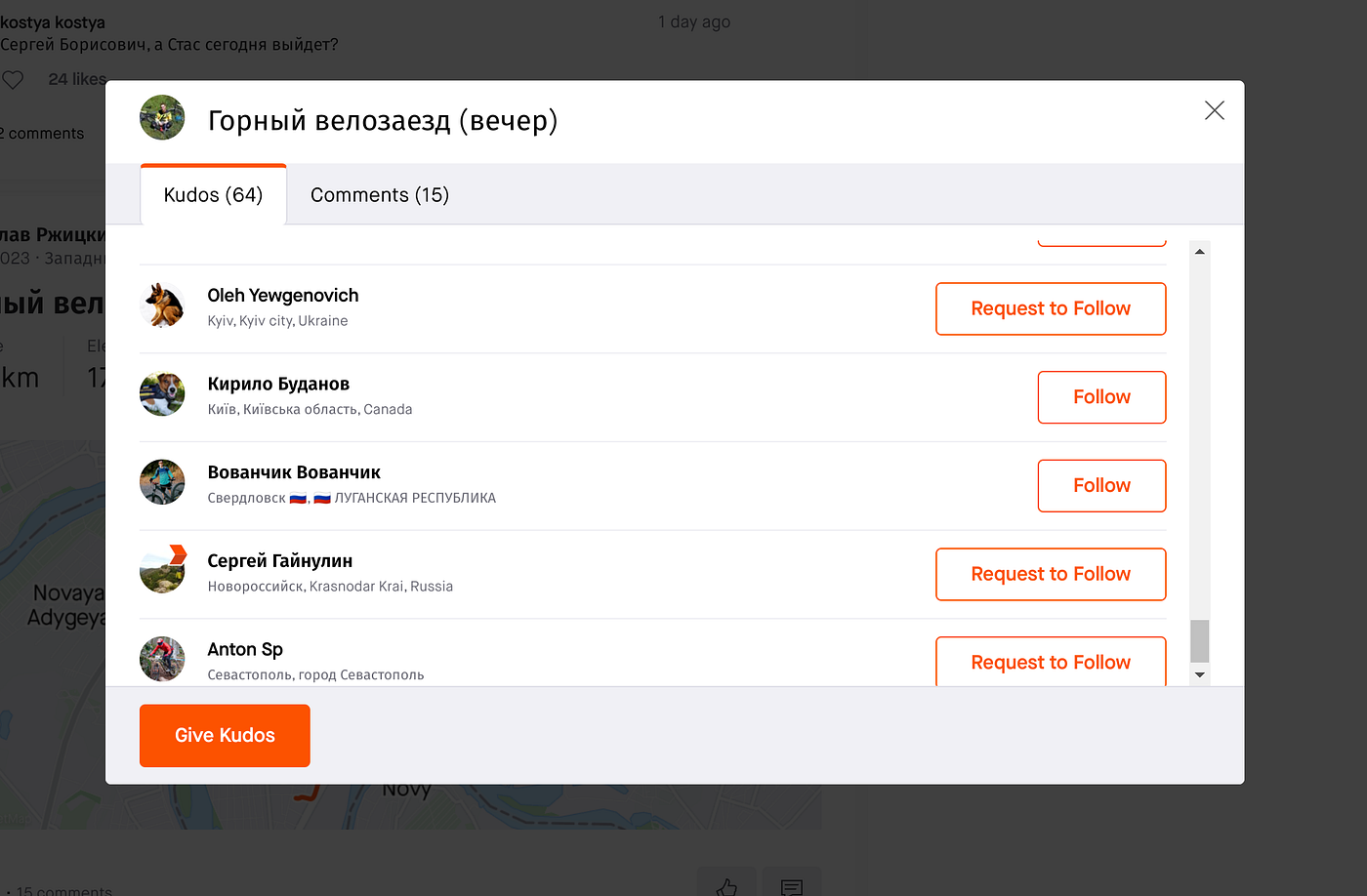 Hello Patron, Lovely to see you. Source: Strava
Hello Patron, Lovely to see you. Source: Strava
In case you’re wondering just who that is we’ve included a screen cap for you.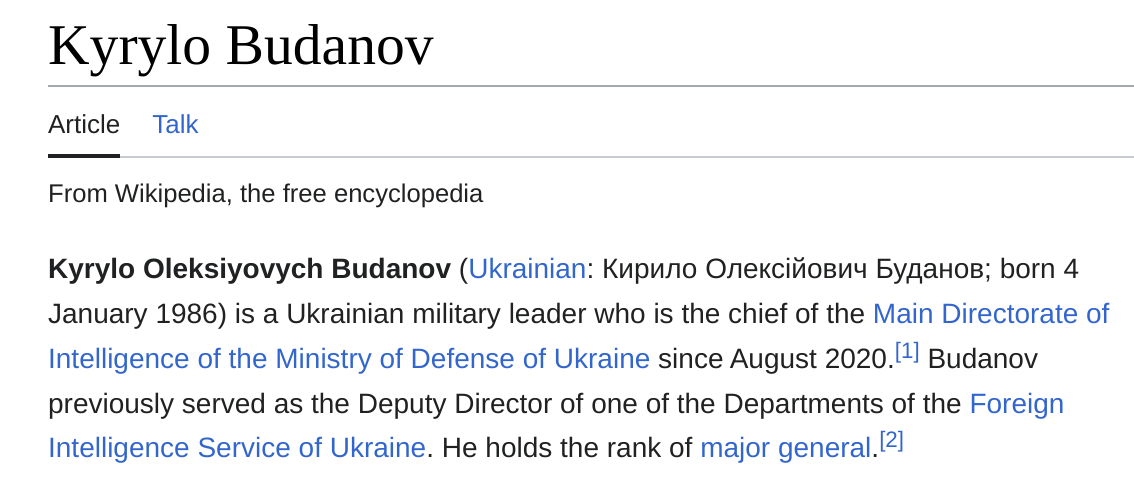
 Kyrylo Budanov, is the Chief of the Main Directorate of Ukrainian Intelligence. While it’s plausible it’s a Sock Puppet (fake) account, it’s worth mentioning here that UA is well known for a well developed online footprint, using this to gather intelligence to assist in the defense of their homeland. It’s also well accepted at this point that Ukraine uses intelligence gathered by nation states, like the US and NATO by extension as well as large amounts of open source intelligence that is gathered using information scraped from the internet. Either way, if you’re on Team Russia, drawing this type of attention from the other side during a war is never a good thing.
Kyrylo Budanov, is the Chief of the Main Directorate of Ukrainian Intelligence. While it’s plausible it’s a Sock Puppet (fake) account, it’s worth mentioning here that UA is well known for a well developed online footprint, using this to gather intelligence to assist in the defense of their homeland. It’s also well accepted at this point that Ukraine uses intelligence gathered by nation states, like the US and NATO by extension as well as large amounts of open source intelligence that is gathered using information scraped from the internet. Either way, if you’re on Team Russia, drawing this type of attention from the other side during a war is never a good thing.
Conclusions:
While we’d pointed out there is a chance it’s a Sock Puppet account it’s also worth mentioning that as the underdog fighting with significant restrictions Ukraine has a history of undertaking operations that punch far beyond their weight in terms of threat mitigation and psychological effect. A good example of this is the Mosskva sinking, where good conditions and a bit of luck sunk the Russian Flagship, with the flow on effect from this being that many black sea assets were now deemed to be at risk. This meant that to prevent further asset loss, Russian ships needed to modify their behavior. A net positive for Ukraine, as well as setting the tone for some operations to be based on psychological effects as much as kinetic.
However one favorable indication that this may in fact be legitimate can be drawn by analyzing the media releases presented by the two different countries. This article by the Russian state based, TASS news agency was particularly vague with information, providing no details upon release, but noticeably being edited after the fact.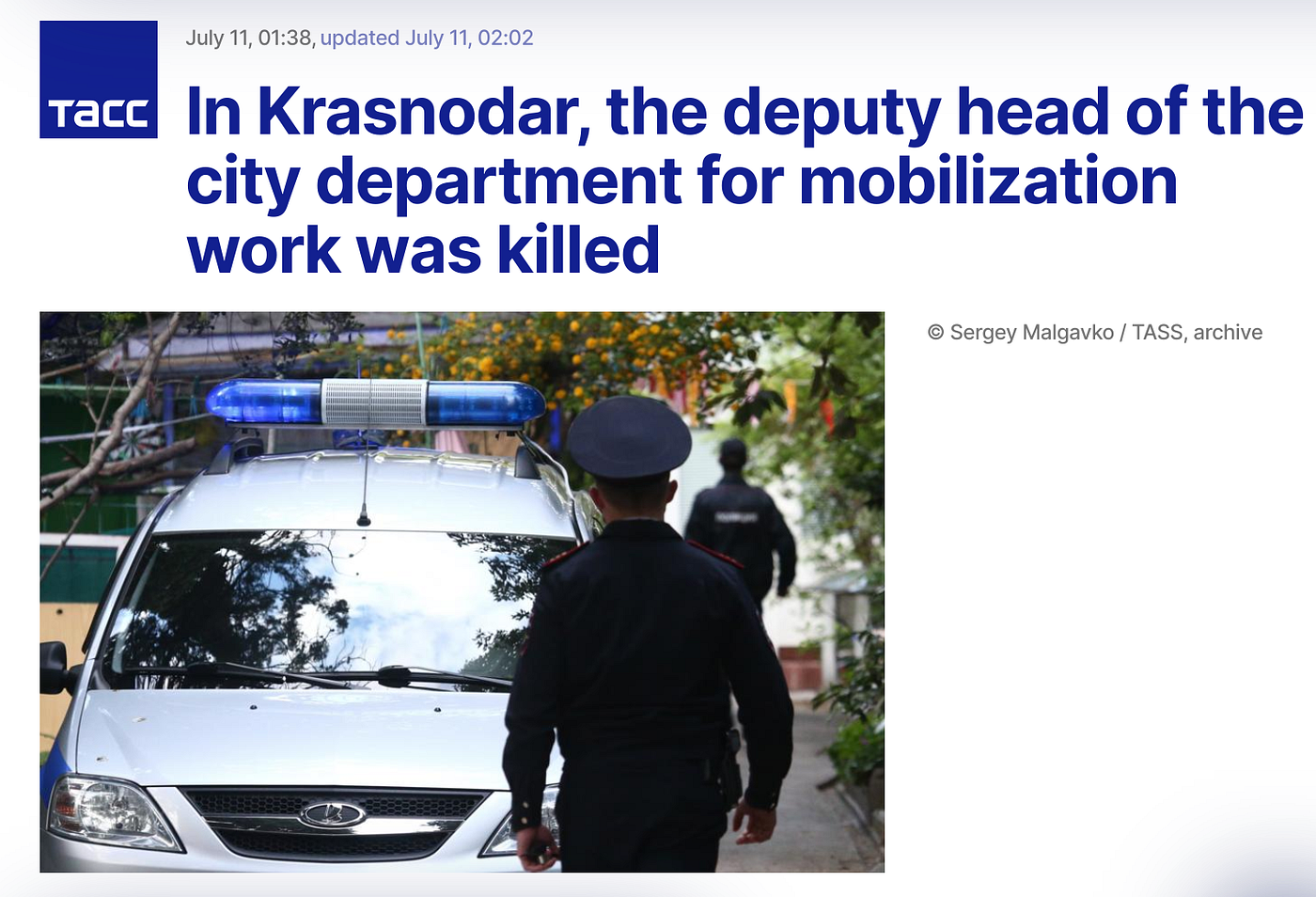 While this press release from Ukrainian government sources was particularly informative, giving a detailed time, reporting and even a specific number of gunshots. While we’ve had to use translate to show you an English version you can see that it’s unusually specific.
While this press release from Ukrainian government sources was particularly informative, giving a detailed time, reporting and even a specific number of gunshots. While we’ve had to use translate to show you an English version you can see that it’s unusually specific.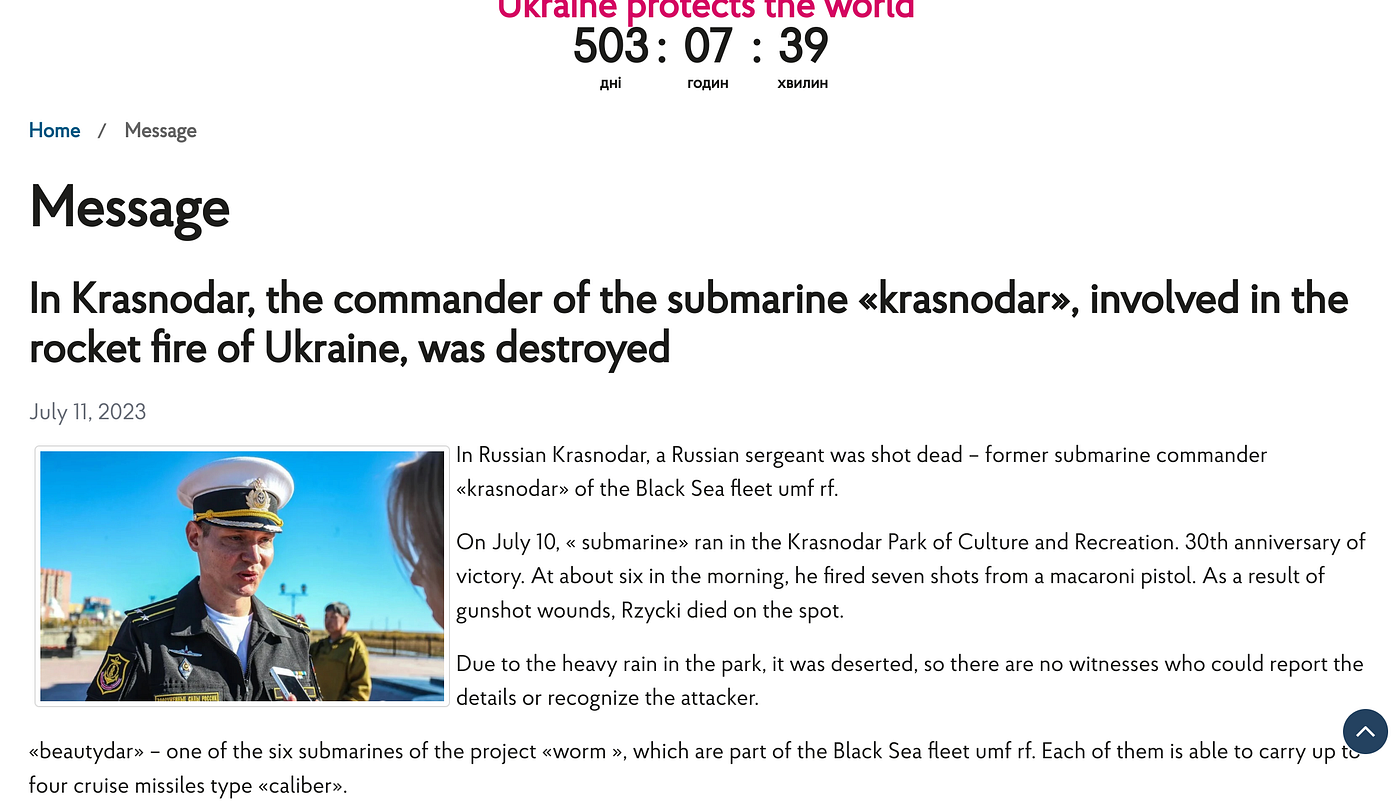 A few errors due to translate but you get the drift. Source: UA Govt
A few errors due to translate but you get the drift. Source: UA Govt
It’s around this point we’d usually close the article and leave it to you to decide, but given the whole element of strange around this event, we’ll leave you with one additionally important piece of information.
In Oct 2022, the open source sleuthing agency Bellingcat provided this press release in which they claimed to have conducted OSINT inquiries that lead to the picture below, identifying key members of the team responsible from programming the many missiles used in attacks on Ukraine following the invasion. Key members of the Offensive Weapons team. Source: Bellingcat
Key members of the Offensive Weapons team. Source: Bellingcat
While this isn’t a smoking gun in anyway what it does show, is that significant research has gone into identifying key participants that assist in perpetuating Russian aggression. And that given this is a kinetic conflict, these individuals are legitimate targets within this conflict given the laws that govern armed conflict. Either way, this has developed in to one interesting story.
The two important question to be asked at this point though is firstly. Did Ukraine State Intelligence action a wartime assassination using open source data scraped from Strava? And if so, then what else has been scraped from Strava that turns out to be actionable intelligence. Time will tell but when we checked the profile while researching the story, it wasn’t particularly difficult to identify other military members within the network so it’s anyone’s guess.
If you’d like to support Ukraine in the defense of their homeland you can do so by following this link.
🌟 Enjoyed this article? Support our work and join the community! 🌟
💙 Support me on Ko-fi: Investigator515
📢 Join our Telegram channel for exclusive updates or.
🐦 Follow us on Twitter
🔗 Articles we think you’ll like:
- I Spy with My Tineye: Reverse Image Searching
- Unmasking the Illusion: Sock Puppets & Social Media
✉️ Want more content like this? Sign up for email updates here