OSINT Unleashed: 5 Essential Tools for Cyber Investigators
When you’re using open source intelligence the ability to obtain and analyse information is key to achieving your goals. The correct tools will help you streamline this process, giving you the ability to delve deeper in to your open source investigations in a faster, more efficient way. In this article, we’re going to take a quick look at 5 tools that we regularly use to streamline our investigations and extract information that is pertinent to the target of our investigations. While we may have mentioned one or two of these at points in previous articles, it’s because for the most part they are very effective when used properly.
Maltego: Visualizing Data
Maltego is a unique tool, as it enables investigators to visualize data obtained via search. Given that most investigations function around being able to use that data and show it effectively, Maltego has a place in every investigative toolkit. While the learning curve can be a little step for those that haven’t used it before, it’s worth learning as it has many integrations that are able to be used for data matching purposes. With a distinct ability to connect and map the footprint and connections between online sources of data, Maltego can provide you with additional sources of information on your target that you may not easily find elsewhere. Whilst it is a paid program, there is a freeware version that is able to be used by open source analysts and investigators free of charge.
_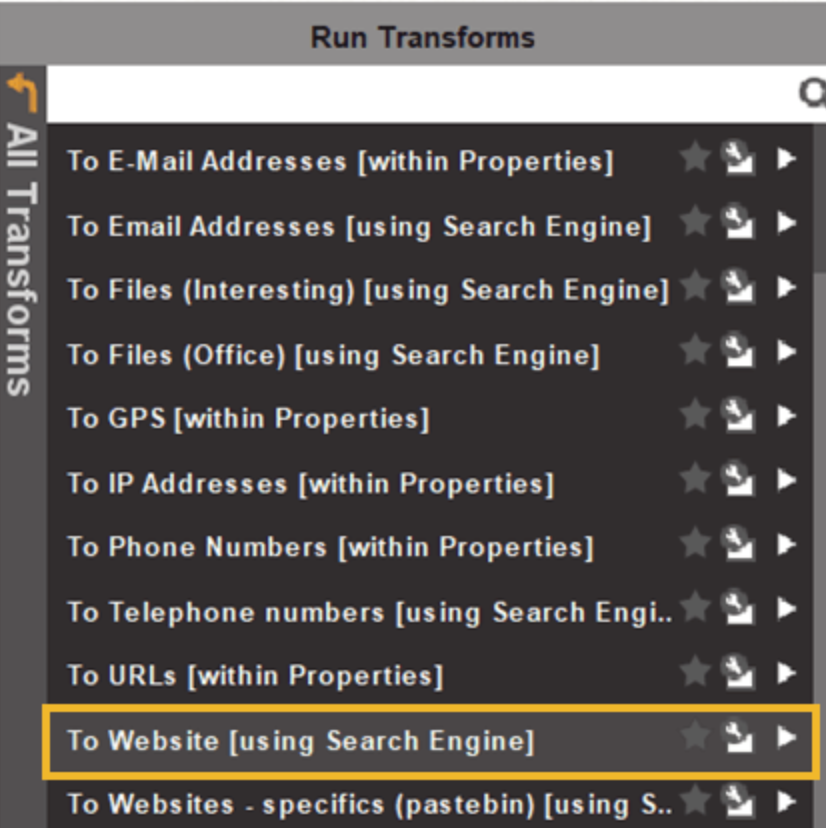 Just some of the transforms available on Maltego
Just some of the transforms available on Maltego
Shodan: Scanning the Internet
If you’ve heard us talk about Shodan before in previous articles, there’s a reason for that. Shodan is awesome, that’s the reason. Standing for Sentient Hyper Optimized Data Access network this tool uses web scraping to profile and display all connected devices to the internet. Whilst it’s a search engine, it’s not your typical search engine as it searches for data from ports and then displays them in different ways. This data can be used for current and historical information on hosts, devices and even countries. With interfaces for both web based and terminal access, you’ll find a way to process shodan data via a method of your choice. Whilst you’ll need to have a paid plan to make the most of it, there is a usable free tier that’s accesible should you want to try it out. Alternately if you’re a student or educator, you can use you educational email address and be given free access to an educational tier, that’s able to be used for research purposes.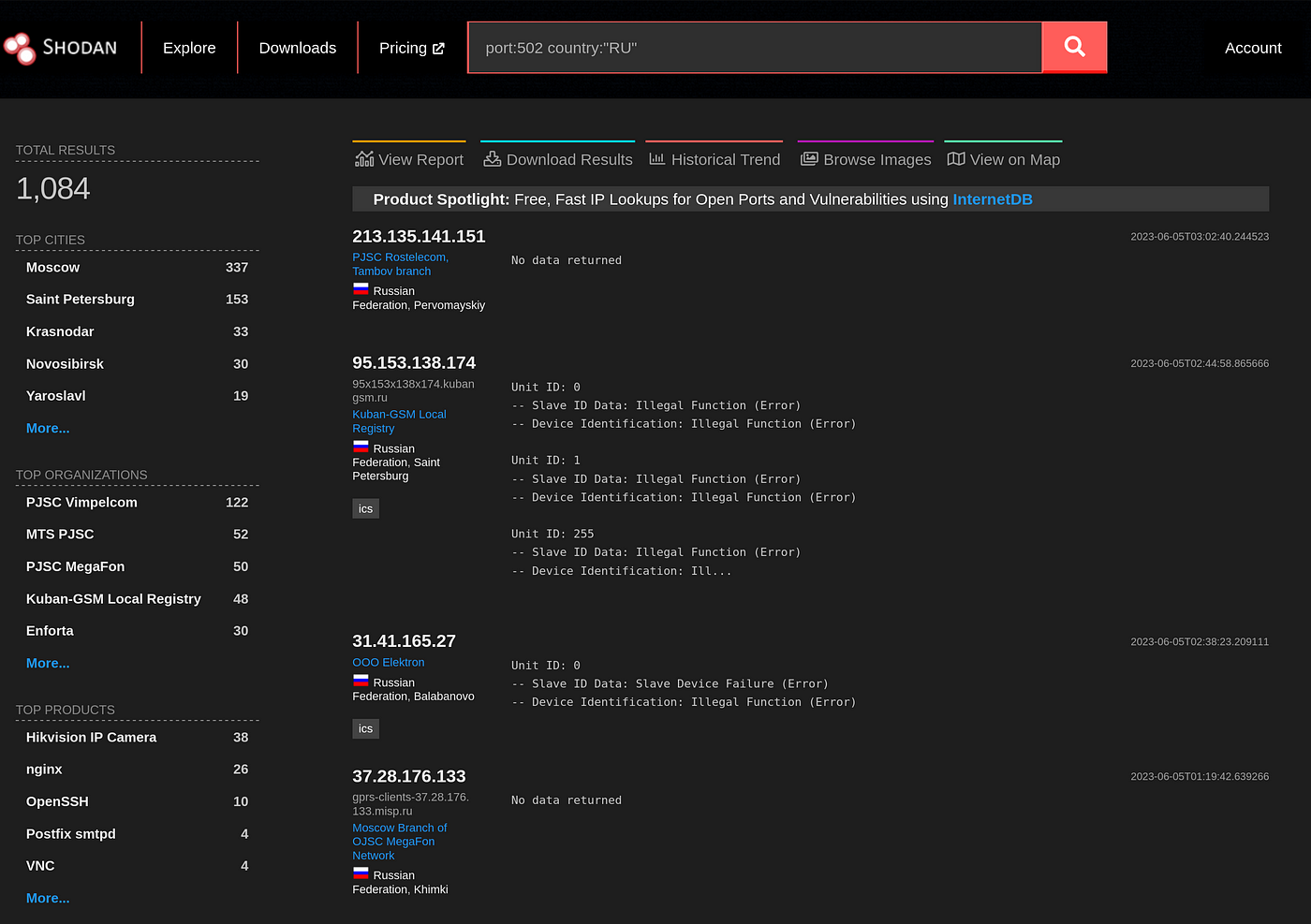 Shodan is a great too for identifying systems.
Shodan is a great too for identifying systems.
Spiderfoot: OSINT Automated
Efficiency is Spiderfoot’s business, and business is good! Spiderfoot automates the collection and processing of opensource intelligence records, drawing on a vast array of services and sources to scrape historical data and present it to the user. With an easy to use interface, Spiderfoot has been both easy to configure and use. Probably one of the biggest issues with using the program appropriately is finding an effective “signal to noise” ratio that isn’t presenting you with large amounts of irrelevant data. Hence your search input’s are the key, and providing accurate search inputs and phrasings provides a clearer and more detailed data output for the end user, requiring less processing post search.. Cybersecurity Professionals and Threat Analyst’s will find Spiderfoot particularly useful, being able to leverage both the command line and web interface to process data more effectively than typical users.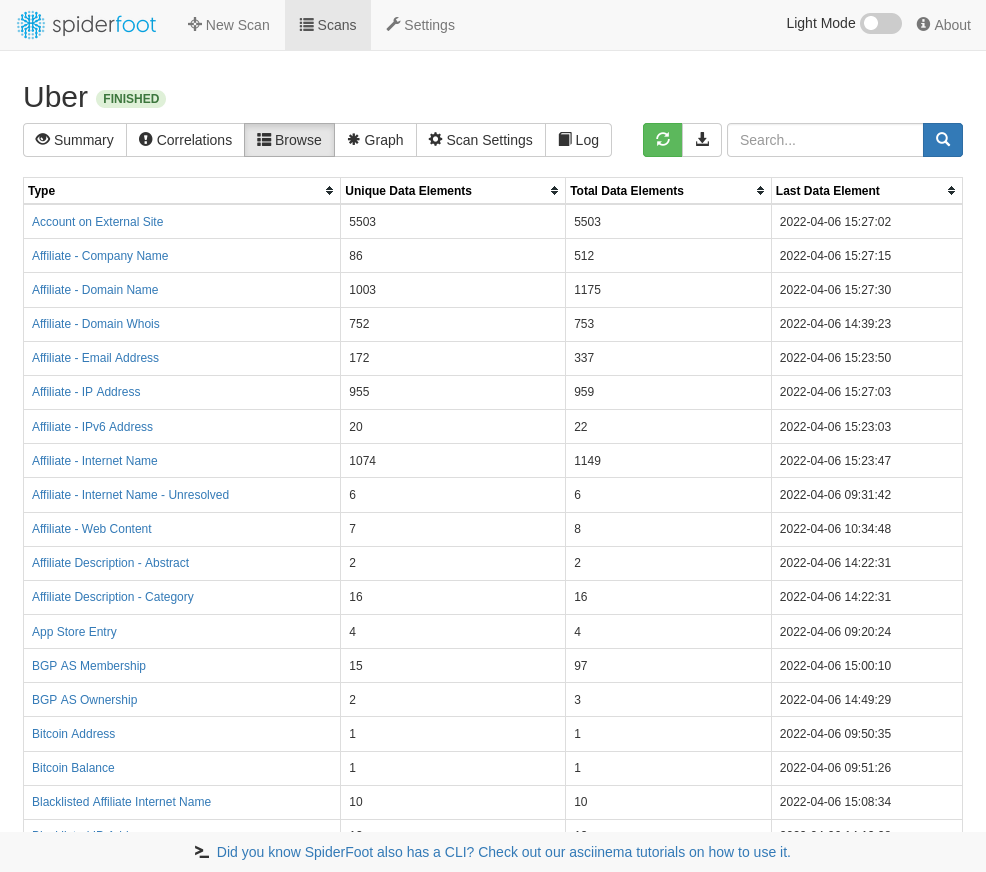 The Harvester: Domain and Email information
The Harvester: Domain and Email information
When it comes to uncovering email addresses, domain information, and related data, theHarvester is a go-to tool for cybersecurity professionals. By collecting information from public sources, theHarvester aids in reconnaissance, social engineering, and email phishing analysis. It helps identify potential attack vectors, enhances overall cybersecurity preparedness, and supports targeted investigations. While theHarvester is a command line tool which means you’ll need some terminal experience to configure, doing so is one of the easier options with regards to command line based osint. The package is also installed on the standard version of Kali Linux, meaning if you’re installing on VM or bare metal, it should be ready to run inside your installation without any further configuration issues.
Recon-NG: The OSINT Framework for Command Line
Recon-ng is an open-source reconnaissance framework that offers a comprehensive set of modules for OSINT gathering. It allows cybersecurity professionals to perform footprinting, enumeration, and data gathering from multiple sources. The extensibility of Recon-ng makes it adaptable to specific investigative needs, providing professionals with a versatile and powerful tool for their OSINT endeavors. Whilst the setup of Recon-ng can require third party API’s and some intensive configuration, when configured you are left with a system that’s easy to use and integrate into your workflow. Recon-Ng homescreen
Recon-Ng homescreen
Start your Journey Here
While the art of Open Source Intelligence, can sometimes seem like a bit of a Dark Art, it’s important to remember that with most open source tools, we get out what we put in. That means that while some tools or skill sets may take some time to correctly develop and hone, once you’ve obtained those skills it becomes easier to apply them to other programs and search techniques, meaning you can develop your technique in a style and way that suits your learning strategy. We’d like to remind people that if you have a strong interest in learning about open source intelligence and developing your skills, that we’ll continue to drop short tutorials and educational absed content that’s designed to assist beginners in selecting tools, using and configuring their system and developing their investigative skillsets. While some tutorials will be paid content, we’ll continue to drop usable content that’s free for readers to use and share. Thanks for reading, and don’t forget to follow us on for our latest article releases across all platforms.
Follow us on medium here
Follow us on telegram here