SHA256 the core of Bitcoin working mechanism
Introduction
Bitcoin, the trailblazing cryptocurrency that revolutionized the financial landscape, operates on a decentralized system powered by a sophisticated technological framework. At its core lies a cryptographic function known as SHA256, an elemental component intricately woven into the fabric of Bitcoin's operational mechanism.
In this article, we delve into the fundamental significance of SHA256 within the Bitcoin network. By understanding the pivotal role of this cryptographic hash function, we gain insights into how Bitcoin transactions are secured, validated, and seamlessly integrated into the blockchain.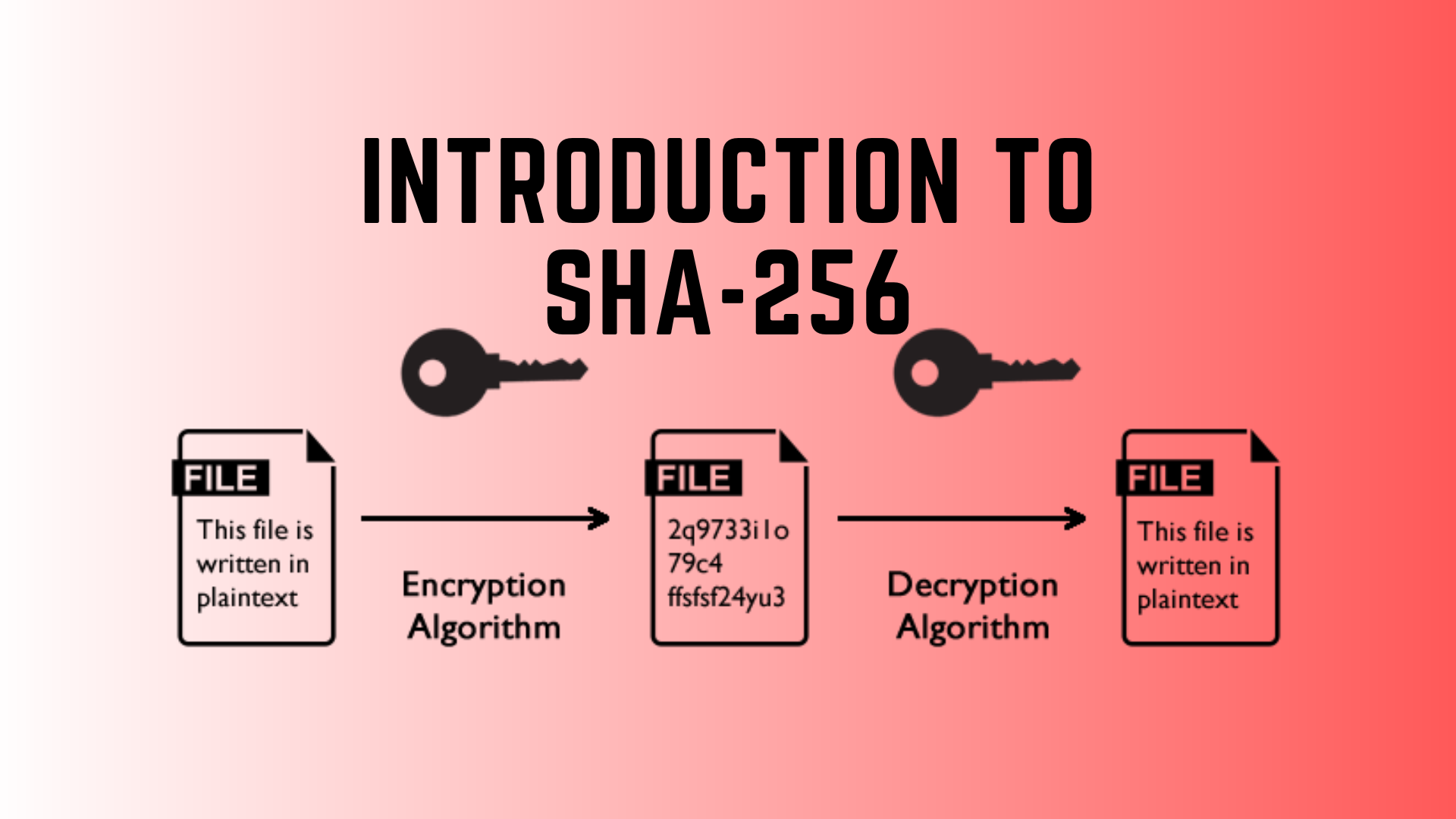
A. Overview of Bitcoin's Innovation
Bitcoin emerged in 2009 as the brainchild of an anonymous entity known as Satoshi Nakamoto. This groundbreaking digital currency was introduced as an alternative to traditional financial systems, aiming to enable peer-to-peer transactions without the need for intermediaries.
B. The Essence of Cryptographic Hash Functions
Cryptographic hash functions form the bedrock of secure digital communication by converting input data into a fixed-size string of characters. They possess crucial properties such as irreversibility, collision resistance, and deterministic output, making them invaluable in ensuring data integrity and authentication.
C. Significance of SHA256 in Bitcoin's Architecture
SHA256 (Secure Hash Algorithm 256-bit) stands as the cryptographic cornerstone that underpins Bitcoin's security and trustless nature. It plays an integral role in mining, transaction verification, and block validation, fostering the immutable and transparent nature of the blockchain ledger.
SHA256, which stands for Secure Hash Algorithm 256-bit, is a cryptographic hash function that belongs to the SHA-2 (Secure Hash Algorithm 2) family of cryptographic algorithms. It is one of the most widely used hashing algorithms in various applications due to its robustness and security features.
Characteristics of SHA256:
- Hash Function: SHA256 is a mathematical algorithm that takes an input (message) of any size and produces a fixed-size output (hash) of 256 bits, regardless of the input's length.
- Deterministic Output: For the same input data, SHA256 always generates the same unique 256-bit output, providing consistency and predictability.
- Irreversibility: It is computationally infeasible to reverse the output of SHA256 to obtain the original input data. This property ensures that the original data cannot be derived from its hash.
- Collision Resistance: SHA256 is designed to minimize the probability of two different inputs producing the same hash output. While not impossible, the likelihood of a collision (two different inputs generating the same hash) is extremely low, making it secure for cryptographic purposes.
- Used in Cryptography: SHA256 is widely used in various cryptographic applications, including digital signatures, password hashing, data integrity verification, and, notably, in the context of Bitcoin and other cryptocurrencies.
Role of SHA256 in Bitcoin:
In the Bitcoin network, SHA256 serves a crucial role in the mining process, block creation, and transaction validation:
- Mining: Miners compete to solve complex mathematical problems related to the creation of new blocks in the blockchain. They use SHA256 to repeatedly hash block headers with different nonce values until they find a hash that meets a specific difficulty target.
- Block Validation: Each block in the Bitcoin blockchain contains a hash of the previous block's header. Any change in the block's data would result in a different SHA256 hash, thereby breaking the chain's continuity and signaling potential tampering.
- Transaction Verification: Transactions within blocks are hashed, and the resulting Merkle root (a cryptographic hash of all transaction hashes) is included in the block's header. This process ensures the integrity of transactions within the block.
SHA256 possesses several key security features that contribute to its robustness and reliability as a cryptographic hash function. These features play a vital role in ensuring data integrity, authentication, and resistance against various cryptographic attacks. Here are the primary security features of SHA256:
1. Collision Resistance:
SHA256 is designed to minimize the probability of producing the same hash value for two different inputs. While it's theoretically possible for different inputs to generate the same hash (a collision), the probability is extremely low due to the large output space (256 bits). The cryptographic strength of SHA256 lies in its resistance to collision attacks, making it highly secure for practical cryptographic applications.
2. Deterministic and Unpredictable Output:
For a given input, SHA256 always produces the same fixed-size (256-bit) output, ensuring determinism. However, the output appears random and unpredictable, making it infeasible to deduce the input data solely from the hash value. This property is crucial for maintaining data integrity and securing sensitive information.
3. Preimage Resistance:
SHA256 exhibits preimage resistance, meaning it's computationally infeasible to reverse-engineer the original input data from its hash value. Given a hash output, finding a specific input that generates that hash is prohibitively difficult, especially due to the massive search space.
4. Avalanche Effect:
Even a small change in the input data results in a vastly different output hash value. This property, known as the avalanche effect, ensures that a slight modification in the input significantly alters the resulting hash, making it nearly impossible to predict the output without knowing the original data.
5. Cryptographic Security:
SHA256 has undergone rigorous cryptanalysis and is considered cryptographically secure against known attacks when used as intended. Its design elements and the complexity of the algorithm have withstood extensive scrutiny by the cryptographic community.
6. Widely Adopted and Trusted:
SHA256 is widely adopted in various cryptographic applications, including digital signatures, data integrity verification, blockchain technology (such as Bitcoin), password hashing, and more. Its extensive use and acceptance in secure systems over time contribute to its credibility and trustworthiness.
7. Secure for Practical Use:
While theoretical attacks may exist (e.g., brute force attacks against weak passwords), SHA256 remains a strong and secure hash function for most practical purposes. Continuous research and advancements in cryptography aim to ensure its resilience against potential future.
Read me this article also quantum-computing-threats-to-crypto:- https://www.bulbapp.io/p/9740698d-ef7d-4f16-88b3-c1808418aa82/quantum-computing-threats-to-crypto