Cybersecurity in 2024: Security Trends and Predictions
The year 2024 introduces a multitude of challenges and opportunities in the field of cybersecurity. With the ongoing expansion of the digital ecosystem, the threats concealed within the virtual realm are also on the rise. This article explores the anticipated cybersecurity trends that will influence the defense strategies of both organizations and individuals in 2024
1. Advanced Persistent Threats (APTs) on the Rise:
As technology evolves, so do the tactics of cyber adversaries. Advanced Persistent Threats (APTs) are anticipated to become more sophisticated in 2024, requiring organizations to bolster their defenses with advanced threat detection and response capabilities.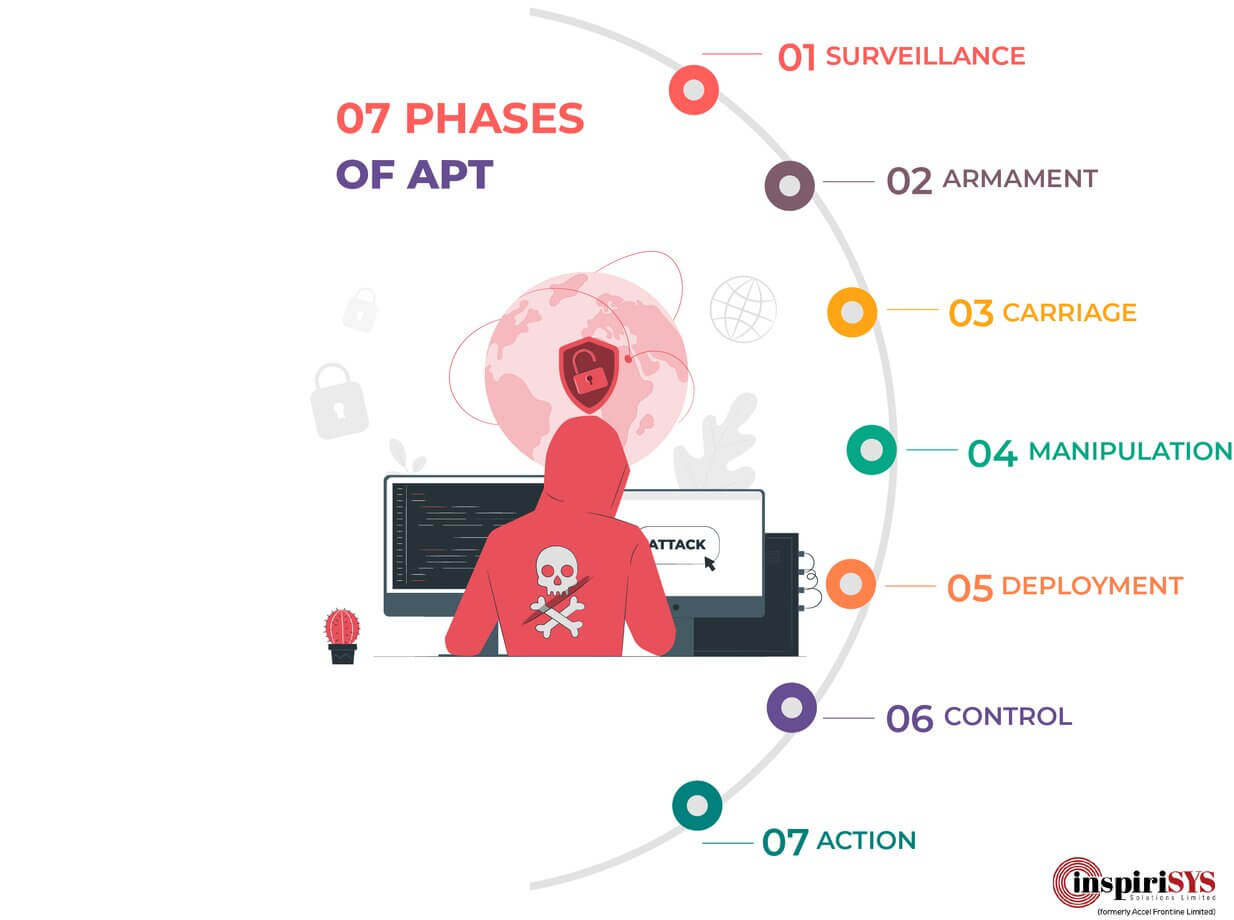
2. AI and Machine Learning Integration:
The integration of Artificial Intelligence (AI) and Machine Learning (ML) will play a pivotal role in enhancing cybersecurity measures. Predictive analytics and automated response systems will become essential tools in identifying and mitigating potential threats in real-time.
3. Zero Trust Architecture Adoption:
The Zero Trust model will gain prominence as organizations move away from traditional perimeter-based security. This approach assumes no inherent trust, requiring verification from anyone trying to access resources, regardless of their location or network connection.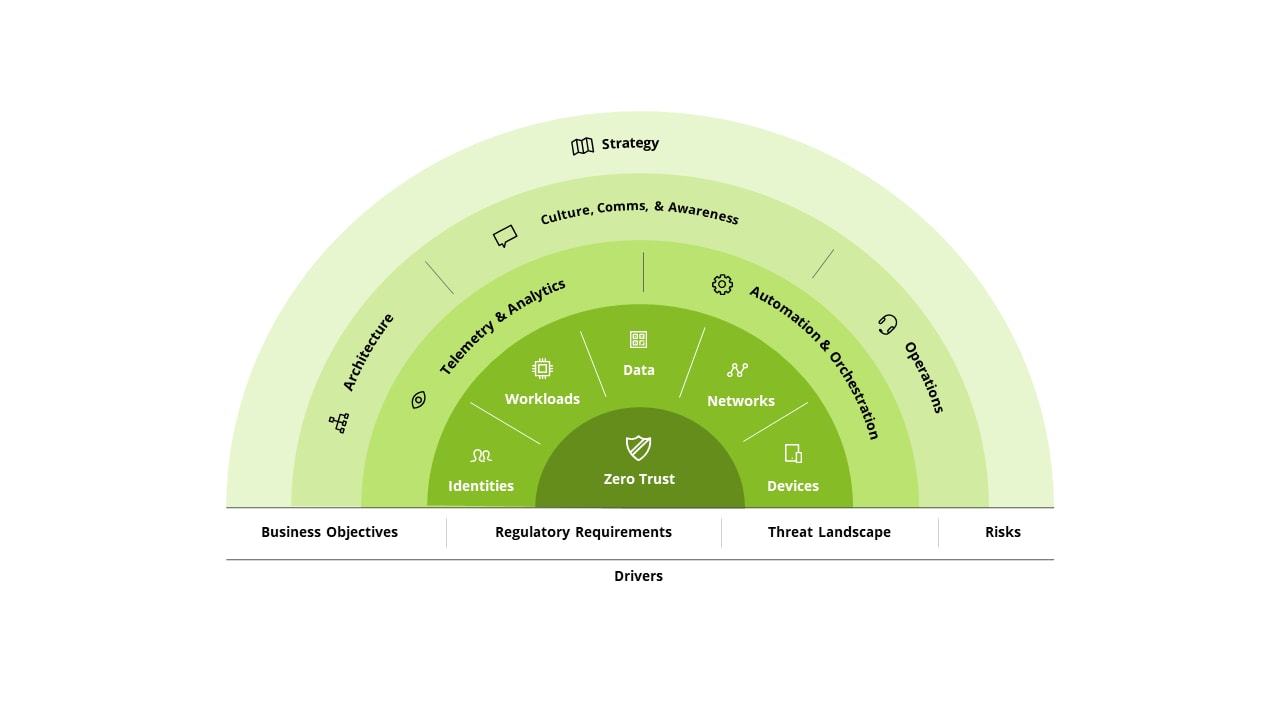 4. Cloud Security Evolution:
4. Cloud Security Evolution:
With an increasing reliance on cloud services, the evolution of cloud security will be a focal point. Comprehensive security strategies will need to address the unique challenges posed by cloud environments, ensuring the protection of sensitive data stored and processed in the cloud.
5. Cybersecurity Skills Shortage Mitigation:
As the demand for cybersecurity professionals continues to outpace the available talent pool, organizations will invest in training programs and automation to mitigate the skills shortage. Collaborative efforts between academia and industry will be crucial in cultivating the next generation of cybersecurity experts.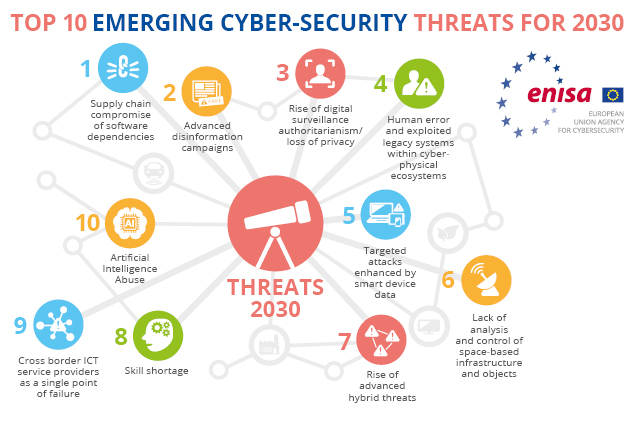
6. Privacy Concerns and Regulatory Compliance:
Growing concerns over data privacy and the enforcement of stringent regulations will shape cybersecurity practices. Organizations will need to navigate evolving compliance requirements, ensuring they meet the standards while safeguarding user data and maintaining transparency.
Ransomware attacks have transformed into exceptionally sophisticated operations, characterized by threat actors employing tactics such as double extortion. In this method, stolen data is not only encrypted but is also under the threat of being leaked unless a ransom is paid. The adoption of advanced encryption algorithms and the targeting of critical infrastructure have significantly heightened the impact of ransomware attacks.
Effectively defending against these evolving threats necessitates a comprehensive approach. This includes implementing resilient backup strategies to safeguard against data loss, providing thorough employee training to enhance cybersecurity awareness, and employing advanced threat detection tools. As the landscape of ransomware continues to evolve, organizations must adopt a multi-faceted defense strategy to mitigate risks and ensure the resilience of their digital infrastructure.
Quantum computing presents an unprecedented potential for solving intricate problems, yet concurrently, it introduces a substantial threat to existing encryption standards. As quantum computers continue to advance in power, there emerges a conceivable risk of them breaking widely employed encryption algorithms, thereby making conventional security measures obsolete. In anticipation of this impending challenge, organizations are actively investigating quantum-resistant cryptographic solutions. The aim is to guarantee the confidentiality of sensitive information in what is often referred to as the post-quantum era.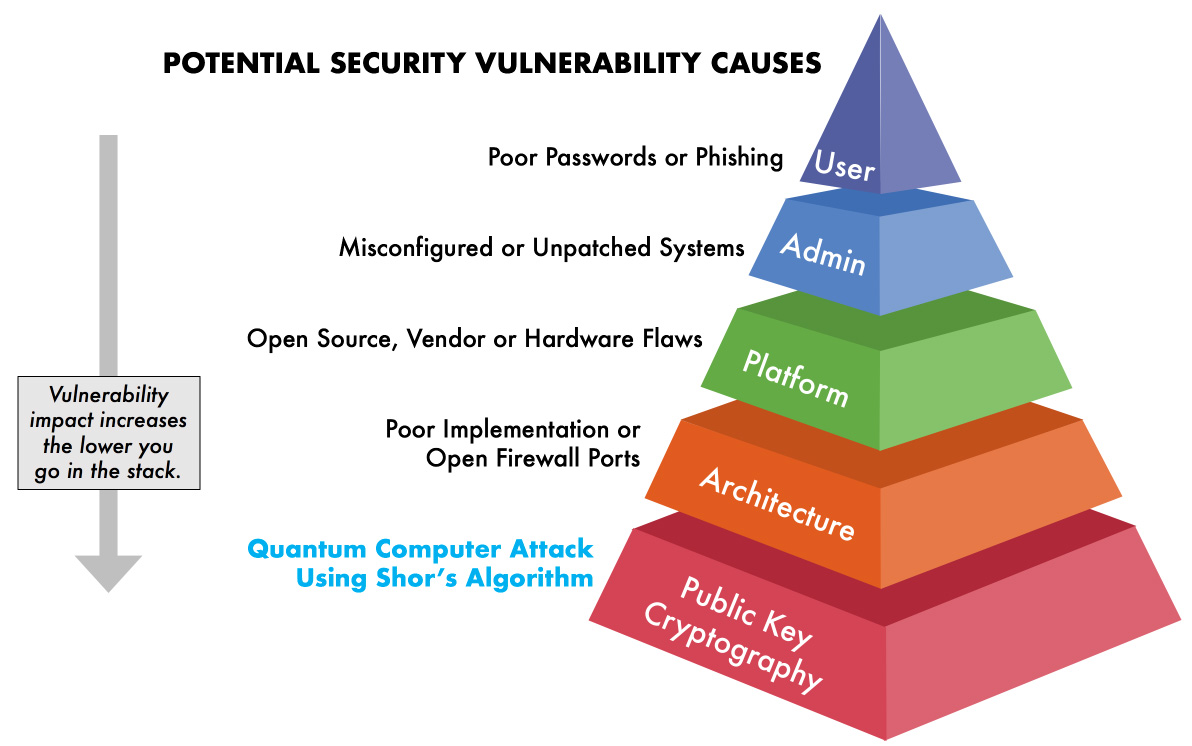
The widespread adoption of IoT devices has broadened the attack surface for cybercriminals. In the year 2024, we anticipate a surge in attacks specifically aimed at IoT devices, taking advantage of vulnerabilities present in their frequently insufficient security measures. Given that these devices have seamlessly integrated into our daily routines, prioritizing their security is imperative. This proactive approach is essential not only to thwart potential disruptions but also to safeguard user privacy in an increasingly connected and digitally reliant world. 
In conclusion, the cybersecurity landscape in 2024 is poised for significant transformations. Staying ahead of emerging threats requires a proactive approach, incorporating the latest technologies and strategies. As organizations and individuals adapt to the evolving digital landscape, understanding and implementing these cybersecurity trends will be paramount in fortifying our defenses against the ever-changing cyber threats of the future.



























