5 More Viruses from The Early Days of The Internet
We’re back with another look at some more interesting computer viruses.
In this article we discussed some of the more famous computer viruses that caused chaos in the early days of the internet. In today’s article, we’ll be looking at 5 more that were well known at the time but didn’t make it on our original list. Your PC is now….Stoned? Source: Wiki
Your PC is now….Stoned? Source: Wiki
1. Stoned Virus (1987, New Zealand)
A boot sector virus, Stoned makes the list due to the fact it’s author to this day, has not been identified. Created in 1987 and first observed in both New Zealand and Australia, this DOS based virus ended up having over 90 different variants and ended up proliferating worldwide.
Spreading via infected disks, Stoned shone light on the dangers of shared media, in particular the 360KB IBM floppy disc.
Stoned made a later appearance in the early 2000’s when the signature of the virus was uploaded into the bitcoin blockchain. This caused an alert in MS Security Essentials which prompted a fix from Microsoft, preventing deletion and quarantining of the blockchain.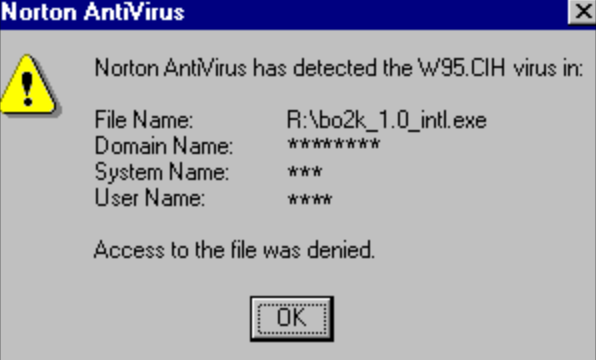 Norton warning for Chernobyl. Source: Wikipedia.
Norton warning for Chernobyl. Source: Wikipedia.
2. CIH / Chernobyl (1998, Taiwan)
Originating in Taiwan and targeting windows 9.X systems, CIH infected over 60 million systems worldwide causing an estimated 35 million USD in damage. Targeting disc drives, CIH was extremely destructive over writing critical information and in some instances destroying the bios of infected machines.
Like the creator of Melissa, the writer of CIH provided an anti virus program to assist in damage mitigation and co operated with authorities, reducing the reach of the virus. Due to no laws existing in Taiwan regarding computer interference, the writer of CIH faced no legal repercussions.
CIH makes the list due to the fact that new IBM Aptiva machines actually shipped with this virus pre installed, causing an explosion of cases in 1999. Kakworm Modifications: Source: Wikipedia
Kakworm Modifications: Source: Wikipedia
3. KAKworm (1999, Unknown)
Released in 1999, KAKworm was a Javascript worm that was able to spread by exploiting Microsoft Outlook.
Making it’s presence known on the first of each month, the worm would trigger a shutdown using SHUTDOWN.EXE whilst displaying the message “Kagou-anti-Kro$oft says not today!”.
Kakworm was reasonably sophisticated for the time, enabling a spread of up to 50 people via outlook address books as well as modifying the boot sector of the infected machine to ensure the virus would load on startup.
While the author of KAKworm remains unknown, it’s makes our list due to the fact the virus exploited two programs to succeed. Microsoft Outlook, as well as Internet Explorer. Back Orifice Logo. Source: Wikipedia.
Back Orifice Logo. Source: Wikipedia.
4. Back Orifice (1999, USA)
Originating in 1999, Back Orifice was a play on Microsoft’s Back Office Server Software. A complete Command and Control system, Back Orifice was designed by US hackers at the 1998 Defcon Conference.
Using a client — server architecture, the program actually has legitimate uses, namely Remote Administration however the program is more commonly used for exploitation purposes.
Due to being designed at Defcon, anti virus response was fast with it being immediately classified as Malware and being added to anti virus quarantine lists.
The program would face further evolution, with Back Orifice 2000 being released. Both programs were suited for Trojan Horse delivery methods as they required no user interaction to run successfully.
Because of this, this one makes our list due to the fact that it’s simplistic GUI based system made it a useful to script kiddie hackers the world over.
5. MyDoom (2004, Russia)
The youngest on today’s list, MyDoom was first observed in 2004 after infected messages originating in Russia started to spread.
Targeting windows based systems, the virus was able to infect over 50 million machines, and even had the dubious honor of knocking google’s search engine offline for a short while.
Using infected computers to send spam / junk emails, the worm spread extremely quickly, with the internet compatibility of the worm ensuring it was able to spread across systems with little resistance. The virus also targeted the decentralized nature of Peer to Peer (p2p) systems, using Kazaa to spread.
However for unknown reasons, the virus failed to target many domains ending in .edu with Rutgers, MIT and Berkley all appearing to avoid infection.
Mydoom makes our list due to the fact it is still seen in systems to this day and the author of the virus has never been identified. In fact, nearly 2% of email traffic today consists of
MyDoom infections. A noteable achievement for a near 20 year old computer worm. It also holds the record to date, for the fastest spreading virus in history.
Lastly, like the Stoned Virus, Mydoom made one late appearance in 2009 when it was used in cyber attacks conducted against South Korea and the USA.
🌟 Enjoyed this article? Support our work and join the community! 🌟
💙 Support me on Ko-fi: Investigator515
📢 Join our Telegram channel for exclusive updates or.
🐦 Follow us on Twitter
🔗 Articles we think you’ll like:
- OSINT Unleashed: 5 Essential Tools for Cyber Investigators
- What the Tech?! GPS Technology
✉️ Want more content like this? Sign up for email updates here