Azure: How to select right key offering?
Today, security is a top concern for every business, especially those that host apps that are essential to their operations. Therefore, it’s important to comprehend how to secure data and handle its lifecycle management when operating on cloud.
Encryption keys in azure are either Platform managed (PMK) or Customer managed (CMK).
Platform Managed Keys are generated, stored and managed by Microsoft, where customers do not have any control. By default, most of the azure services (ex: Azure Disk, Storage Accounts etc.) are all encrypted at rest using PMK without an additional cost.
Customer Managed Keys on the other hand, can be managed and/or administered by the customer based on the category of Key offerings. They are again classified as (software backed keys, hardware backed keys), and organizations have various options to closely manage encryption models depending upon the use-case.
The degree of FIPS compliance, administrative burden, and key management vary between these choices. A quick comparison is shown below: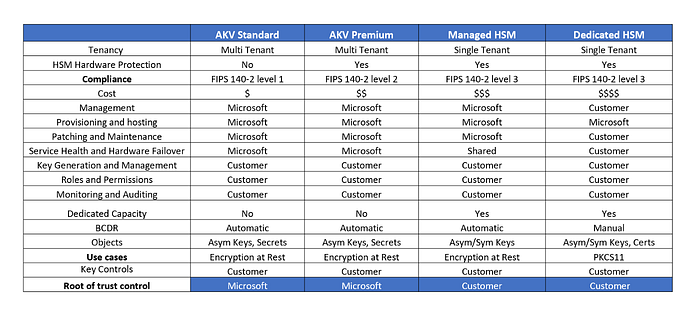 Photo by Author ©
Photo by Author ©
The most popular key management service in Azure is AKV (Azure Key Vault Standard), which is a FIPS 140–2 Level 1 validated multi-tenant cloud key management service that can also be used to store secrets and certificates. Azure Key Vault standard keys are software-protected (encrypted with RSA, AES Algorithm) for various azure services, applications. It is a more cost-effective operating model than others used for simple workloads that do not handle personally identifiable information.
Azure encryption at rest models envelope encryption, which encrypts a data encryption key (DEK) with a key encryption key (KEK). Photo by Author ©
Photo by Author ©
Data Encryption Key (DEK): A symmetric AES256 key that is used to encrypt a data block or partition; often known as just a Data Key. There could be numerous partitions and Data Encryption Keys for a single resource. Crypto analysis assaults are made more challenging by encrypting every block of data using a distinct key.
Key Encryption Key (KEK): It is used to wrap or encrypt the Data Encryption Keys utilizing envelope encryption. DEK themselves can be encrypted and managed with the use of a KEK that never leaves the key vault. Customers can cryptographically delete DEKs and other data since the KEK is necessary to decode the DEKs.
Azure Key Vault (Premium Tier): A FIPS 140–2 Level 2 verified multi-tenant HSM (Hardware security modules) offering that used to store keys in a secure hardware boundary managed by Microsoft, and keys kept in Azure Key Vault Premium for encryption-at-rest and encryption-at-transit. When users need to store KEK keys supported by secure hardware boundaries (HSM) but can’t afford to administer or operate HSM in the cloud, this is preferred.
Azure Managed HSM: A single-tenant HSM product that has been FIPS 140–2 Level 3 validated and allows users to get complete control over an HSM for encryption-at-rest, Keyless SSL, and custom applications where Microsoft manages the provisioning, patching, maintenance, and hardware failover of the HSMs, but does not have access to the keys themselves because the service runs within Confidential Compute in Microsoft Data center. Customers receive a pool of three HSM partitions, acting together as one logical, highly available HSM appliance, fronted by a service that exposes crypto functionality through the Key Vault API. When a customer has dedicated capacity for their HSM requirement and prefers a robust encryption approach for business-critical tasks, this is typically recommended.
Azure Dedicated HSM: A Single-tenant FIPS 140–2 Level 3 HSM service where customers can rent a multipurpose HSM equipment that is housed in Microsoft datacenters through the Azure Dedicated HSM service, where bare-metal device is wholly owned by the customer, who is also in charge of patching and updating the firmware as needed. Dedicated HSM is not connected with any Azure PaaS services, and Microsoft has no access to the device or the key material. With the use of the PKCS#11, JCE/JCA, and KSP/CNG API’s users communicate with the HSM. This product is best suited for traditional lift-and-shift workloads, PKI, SSL Offloading, Keyless TLS, OpenSSL apps, Oracle TDE, and Azure SQL TDE IaaS. Supported integrations include F5, Nginx, Apache, Palo Alto, and more.
References:
I'm writing on medium, please find my article here :Azure: How to select right key offering? | by Musunuru Sharmila | Jul, 2022 | Medium