Exploring the Darkweb: History & Mystery
Today we go for a walk back through the history of the Dark Web
For normal, everyday internet users, the dark web can be a clandestine and mysterious place. If you believe the mainstream media, it’s full of drugs, hitmen for hire, and hackers. Capturing the attention of the authorities as well as bad actors, this corner of the internet plays an integral role in the online world, despite its somewhat murky reputation After a slow start, TOR entered the mainstream. Source: Wikipedia
After a slow start, TOR entered the mainstream. Source: Wikipedia
The Beginnings
While it took time for the general understanding of the dark web concept to reach the general public, the truth is that the dark web has existed almost as long as the internet itself. As strong encryption evolved and became more commonplace, the dark web moved through phases and became more complex and established.
In the early days, the dark web provided a place for privacy-focused users to leverage secure communications. However, as it evolved, it became an internet all of its own, providing secure and hidden, websites, messaging boards, and internet forums. These provided a range of information and services, of both legal and illegal types, and some of these, (like the Silk Road) would eventually come to mainstream knowledge in later years.
Like many other forms of technology, policing was slow to adapt to the new form of technology with criminal activity easy and prolific in those earlier days. However that wouldn’t last for long, and by the modern era, the dark web would end up being one of the most heavily surveilled places on the internet. While it doesn’t preclude crime from occurring, it does mean that law enforcement, military, and intelligence agencies have a far deeper understanding of just what type of activity occurs on the dark web, as well as where to find it.  The dark web is policed far better now. Source: Wikipedia
The dark web is policed far better now. Source: Wikipedia
Legitimate Uses
Despite the myriad of bad publicity the dark web receives, the fact is that it actually has plenty of legitimate usages as well that offset this. Activists, Journalists, and Political dissidents can use the dark web to communicate safely and you’ll also find regular, privacy-focused users will often leverage its anonymity as well.
In fact, while it’s generally known to the public that the dark web exists, one fact that is far less commonly known is that it was the US government that actually implemented and designed onion routing in its early days.
Researched by employees at the US Naval Research laboratory, onion routing ( the technique used by the TOR browser) was originally designed to protect US intelligence communications online. Seeing the utility of the protocol, however, the public release of TOR occurred just one year after its launch in 2003. Soon after it reached the attention of internet subculture and the rest, as they say, is history.
While the dark web and the TOR project in general are valuable tools to the worldwide community for many reasons, both the media and the general public can often lack understanding of this function and utility. This leads to bad reporting and outright fear-mongering which takes its form in clickbait journalism and disinformation.
TOR is simply another tool in the privacy toolkit for those who want it. It has issues with protocol and doesn't provide outright security despite those who claim it is a crime haven for just those reasons. Given that policing criminal activity is always a challenging balancing act of both resources and attention anywhere, policing and regulating the dark web properly starts to look more like something that needs a targeted approach rather than being an unattainable goal.  The method behind TOR is ingenious but effective. Source: Wikipedia
The method behind TOR is ingenious but effective. Source: Wikipedia
Notable Dark Web Events
The Silk Road
The most noteworthy of our incidents, the first would have to be the implementation and subsequent takedown of the Silk Road marketplace. Silk Road, which provided an online black market for everything from Drugs, to fake identities and pornography was taken down in 2014 after intensive surveillance to identify the main players.
We’ve often spoken about privacy and the de-anonymising of data before and hold the opinion that the Silk Road story is a great place to go and learn more about that process. Covering everything from the identification of users and machines to the tracking of online cryptocurrency payments, exploring the story shows an in-depth look at some of the challenges that come when you look at policing the dark web and other spaces on the internet. It also provides insight into data matching and processing techniques that will become more relevant in our data-focused world. 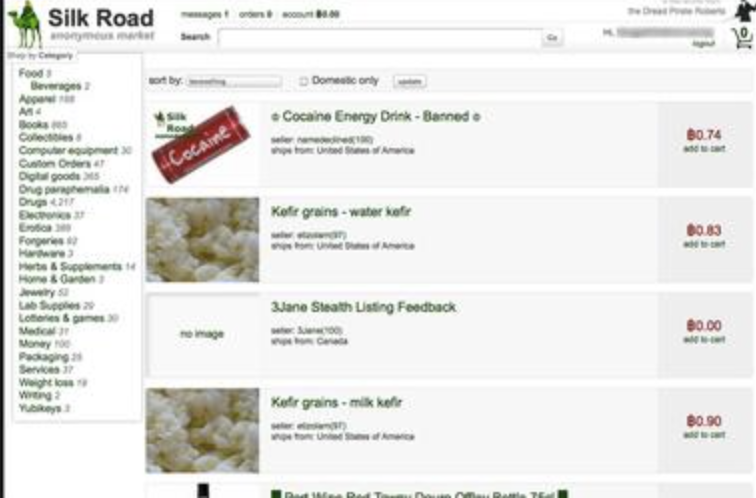
AlphaBay Takedown
Launched in 2014 as the next-gen Silk Road, AphaBay provided the next dark web black market services, providing just as many features as before. However AlphaBay gets a mention for sheer staying power, as well as being reborn for a second time. Shut down by authorities in 2017, it emerged using different formats and locations in an attempt to evade enforcement actions.
Unique for its usage of online reputations and digital contracts, AlphaBay attempted to provide a user-friendly black market where you could be assured you were getting what you paid for. However, despite users numbering in the hundreds of thousands, AlphaBay would eventually close it’s own doors, with the market going dark in 2023 after failing to provide a renewal for one of its canaries. The administrators haven’t been heard from since.
Despite its relative success, AlphaBay suffered several severe data breaches that led to user identification, as well as leaked messages from the platform. Both breaches occurred by exploiting AlphaBays API, allowing access to the data as a result. AlphaBay also faced coordinated action from law enforcement. Source: Wikipedia
AlphaBay also faced coordinated action from law enforcement. Source: Wikipedia
Crypto Mixing & Ransomware
Rather than being notable for a single incident, our next notable darkweb incidents occur repeatedly each day. Ransomware incidents in particular are noteworthy for the use of the dark web to process cryptocurrency payments and provide communications services.
Many of these ransomware attacks have the backing of nation-states, with both North Korean & Russian hackers receiving particular attention with regards to this. Both countries have an extensive history of conducting ransomware campaigns with crypto payment services.
While ransomware is well known, however, crypto mixing services are lesser known. Designed to provide a way of turning regular, trackable crypto into untrackable privacy coins mixing services have been around since the early days of crypto and have been used for nefarious purposes ever since.
Also known as tumblers, these services provide a way of laundering crypto that attempts to make it untraceable by authorities. While they were quite popular in the early dark web days, the evolution of privacy-focused wallets that provide a similar service became more popular, eventually taking over. Bitmixer was a popular mixing service that closed down in 2017 after receiving pressure from regulators around the provision of it’s services. However even today, there is still privacy-focused coins like Kapsa and Monero that aim to provide anonymity from transactions.
In Closing
In writing this article we’ve really only touched the surface on the dark web and some of its history. There certainly is plenty of mystery that remains. And while many people may never use it, it still provides those that chose with the ability to leverage its privacy-focused tools. Like many parts of the internet though, it’s reasonable to expect that it will continue to evolve in the way that other corners of the internet have.
We should also assume that researchers, criminals, intelligence agencies and police agencies will be right alongside it, watching it evolve as well.
Medium has recently made some algorithm changes to improve the discoverability of articles like this one. These changes are designed to ensure that high-quality content reaches a wider audience, and your engagement plays a crucial role in making that happen.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Support our work and join the community! 🌟
💙 Support me on Ko-fi: Investigator515
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- Software Defined Radio & Radio Hacking
- OSINT Unleashed: 5 Essential Tools for Cyber Investigators
✉️ Want more content like this? Sign up for email updates here