North Korea's Cyber Warfare: Funding Nuclear Ambitions Through Cryptocurrency Heists
Recent revelations from a United Nations report shed light on North Korea's clandestine cyber activities, exposing a web of cyberattacks valued at a staggering $US3 billion. What's even more alarming is the purpose behind these sophisticated heists: funding the regime's nuclear and weapons programs. Let's delve into the details of this chilling article and unravel how North Korea is leveraging the digital realm to fuel its ominous ambitions.
The UN's Investigation
The UN Panel of Experts on the Democratic People's Republic of Korea (DPRK) has undertaken an extensive investigation into a multitude of cyberattacks that have been linked to North Korea. This investigation, detailed in the panel's annual report, encompasses a comprehensive analysis of 58 cyberattacks carried out between the years 2017 and 2023.
Among these incidents, a particularly alarming trend has emerged in 2023, with 17 cryptocurrency heists capturing the attention of investigators. These cyber heists, characterized by their sophistication and scale, collectively amount to a staggering value surpassing $US750 million.
The meticulous scrutiny applied by the UN Panel of Experts underscores the gravity of North Korea's cyber activities and their implications on global cybersecurity. The chronological span of the investigation, spanning several years, highlights the sustained and evolving nature of cyber threats emanating from the DPRK. Furthermore, the concentration of cryptocurrency-related crimes in 2023 accentuates the regime's strategic shift towards exploiting digital currencies as a means to finance its illicit agendas, particularly its nuclear and weapons programs.
Funding Nuclear Ambitions
The report's findings reveal a stark reality: North Korea's cyber operations play a pivotal role in the regime's financial ecosystem, accounting for approximately 50% of its foreign currency income, as reported by one member state. This illicit revenue stream, primarily derived from cybercrime activities, is not relegated to mere economic gains but is strategically channeled into the regime's weapons programs, notably its nuclear initiatives. This revelation paints a disturbing picture of a nation adept at leveraging digital means not only to evade international sanctions but also to bolster its militaristic ambitions.
The report underscores the multifaceted nature of North Korea's cyber activities, which extend beyond mere financial gain to directly fueling its weapons programs. By relying heavily on cyber operations to generate substantial foreign currency, North Korea circumvents the constraints imposed by global sanctions, thereby sustaining and advancing its militaristic endeavors. This strategic maneuvering in the digital realm represents a formidable challenge to international efforts aimed at curbing the regime's aggressive pursuits and underscores the imperative for enhanced cybersecurity measures and diplomatic interventions to address this evolving threat landscape.
The Rise of Crypto Theft
In recent years, North Korea has strategically pivoted towards cryptocurrency theft as a primary means of generating foreign currency income, marking a significant shift in its tactics. The UN report brings to light a series of targeted cyber operations orchestrated by the regime, specifically aimed at the virtual asset industry. These operations are characterized by their sophistication and precision, reflecting a concerted effort to execute high-stakes cyber heists designed to augment the regime's financial reserves.
The report underscores numerous instances where North Korea's cyber operatives have meticulously targeted cryptocurrency exchanges, wallets, and platforms, employing advanced techniques to breach security measures and siphon off digital assets. This calculated approach to crypto theft has propelled North Korea into the spotlight as the "world's most prolific cyber-thief," a dubious distinction that underscores the scale and impact of its illicit activities in the digital domain.
By focusing on cryptocurrency theft as a primary revenue stream, North Korea circumvents traditional financial channels and international sanctions, thereby bolstering its financial capabilities to support its militaristic ambitions. This strategic maneuver underscores the regime's adaptability and sophistication in navigating the evolving landscape of cybercrime, posing a formidable challenge to global cybersecurity efforts and necessitating enhanced vigilance and countermeasures to mitigate the risks posed by such malicious activities.
Operational Nuclear Facilities
Despite facing international scrutiny and enduring sanctions, North Korea's nuclear facilities persist in their operational status, defying attempts to curb the regime's advancements in nuclear capabilities. The UN report highlights ongoing activities within these facilities, including weapons testing and missile launches, which serve as tangible evidence of North Korea's unwavering commitment to military advancements.
The persistence of weapons testing and missile launches not only underscores North Korea's technological prowess but also signifies a persistent drive towards bolstering its military capabilities. This relentless pursuit of military advancements, in the face of international condemnation and sanctions, raises significant concerns about the stability and security implications within the region and beyond.
The report's revelation of ongoing operations within North Korea's nuclear facilities calls into question the effectiveness of existing measures aimed at curbing the regime's nuclear ambitions. It underscores the urgent need for renewed diplomatic efforts and robust enforcement of international sanctions to address the destabilizing impact of North Korea's unchecked technological pursuits on regional and global security.
Targeting Defense Companies and Sanctions Evasion
North Korea's cyber operations extend far beyond cryptocurrency theft, encompassing targeted attacks on defense companies worldwide. The UN report reveals a pattern of sophisticated cyber intrusions orchestrated by the regime, employing tactics such as social engineering and phishing to infiltrate the networks of defense entities. These operations are not merely opportunistic but are strategically designed to procure sensitive information crucial for advancing North Korea's weapons programs.
The use of social engineering and phishing tactics underscores the regime's adeptness at exploiting human vulnerabilities to gain unauthorized access to valuable data. By targeting defense companies, North Korea seeks to acquire technological insights, military strategies, and sensitive intelligence that can directly contribute to enhancing its arsenal and military capabilities.
Moreover, the report identifies specific cyber actors affiliated with North Korea's Reconnaissance General Bureau, a key intelligence agency linked to the regime's cyber operations. The recommendation for targeted sanctions against these actors highlights the gravity of their involvement in illicit cyber activities and underscores the international community's determination to curb North Korea's nefarious cyber pursuits.
The nexus between cyber intrusions, defense industry targeting, and sanctions evasion paints a concerning picture of North Korea's strategic maneuvering in the digital realm. It underscores the imperative for heightened cybersecurity measures within the defense sector and concerted international efforts to counter and deter malicious cyber activities orchestrated by rogue states like North Korea.
Global Impact and Recommendations
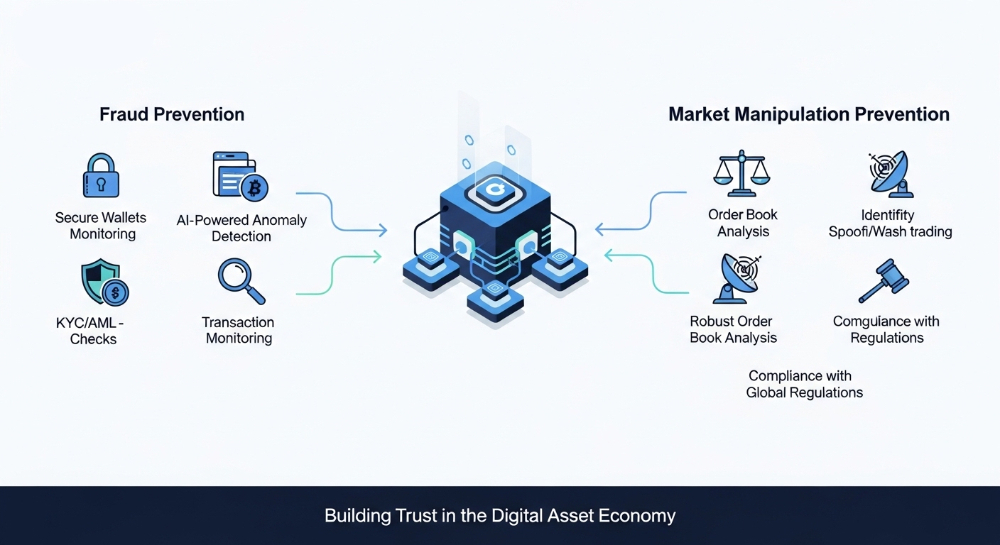
The findings of the report resonate with far-reaching implications that extend beyond national borders, necessitating a collective response and enhanced vigilance across the global digital landscape. The magnitude of North Korea's cyber activities underscores the urgent need for bolstered cybersecurity measures at various levels, including individuals, cryptocurrency exchanges, and governmental institutions.
At the individual level, heightened awareness and adherence to robust security protocols are imperative to mitigate the risks posed by cyber threats, particularly those with suspected ties to North Korea. Individuals must exercise caution in their online activities, employ strong authentication methods, and remain vigilant against phishing attempts and malware attacks orchestrated by malicious actors.
Cryptocurrency exchanges, as primary targets of North Korea's cyber operations, are urged to fortify their security infrastructure and implement stringent monitoring mechanisms to detect and thwart suspicious transactions. Enhanced due diligence practices and real-time transaction monitoring can significantly reduce the risk of illicit funds flowing into North Korea's coffers through crypto theft.
Governments play a crucial role in combating cyber threats emanating from rogue states like North Korea. The report's recommendations underscore the importance of coordinated international efforts, information sharing, and diplomatic cooperation to counter the evolving tactics of malicious cyber actors. Strengthening international cybersecurity frameworks, imposing targeted sanctions on perpetrators, and fostering collaboration among law enforcement agencies are essential components of a comprehensive strategy to address the global impact of North Korea's cyber activities.
In essence, the report serves as a clarion call for heightened cybersecurity resilience, enhanced regulatory frameworks, and concerted international cooperation to safeguard against cyber threats posed by rogue states and preserve the integrity of the digital ecosystem.
Conclusion
North Korea's foray into cyber warfare, marked by multi-billion-dollar heists and sanctions evasion, underscores the evolving nature of modern threats. As the world grapples with the nexus between cybercrime and geopolitical ambitions, the UN report serves as a stark reminder of the urgent need for robust cybersecurity measures and concerted international action to safeguard against rogue actors exploiting digital vulnerabilities for destructive ends.