Historical Hacks: The SQL Slammer
This hack exploited an unpatched buffer overflow to make mischief
You don’t have to be ridiculously old to hear people talk about the good old days of the internet. While it’s pretty questionable if anyone would ever refer to dial-up as good, there’s no arguing that in some ways the early days of the internet were very different to what we see now.
In today's world, the internet has become the playground of state-backed intelligence agencies and hackers for hire looking to exploit information for value. And, while this still occurred in the good old days, a lot of early hacks and exploits were carried out by curious minds simply looking to explore how things work. Damage is damage, but it’s not unreasonable to say there’s a big difference in the motivations of individuals that have evolved over time.
Today's hack happened in the days before social media, before 24/7 connectivity and as always some bad security really helped it along its way and made it more damaging than it would have been if the patch had been applied. It’s the 2003 SQL Slammer (CVE-2002–0649).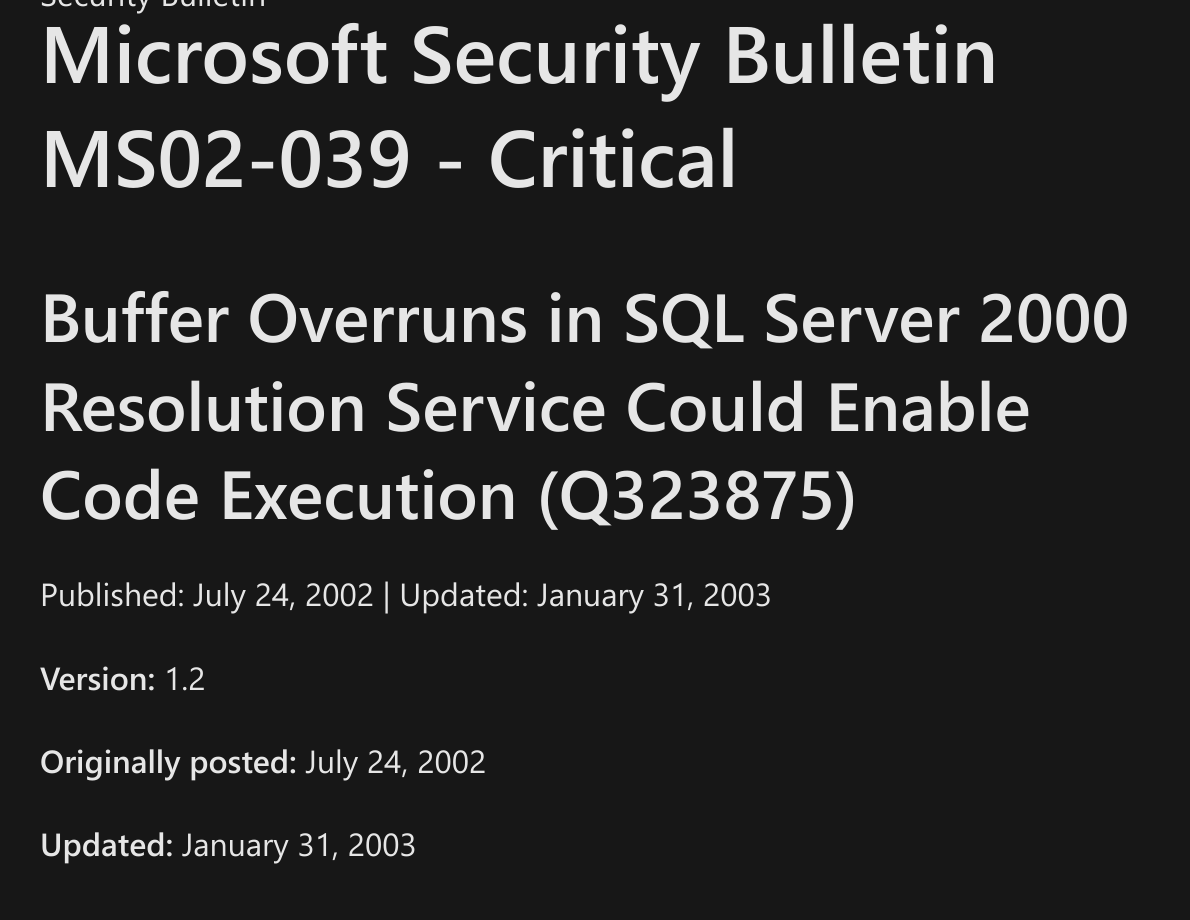 The CVE was identified well before the initial attack. Patch your systems folks! Source: Microsoft.com
The CVE was identified well before the initial attack. Patch your systems folks! Source: Microsoft.com
Background
Some viruses have a slow burn, using time-related properties or other conditions to slow their progress or enable them to look for certain conditions before being triggered. The slammer was not one of these types of viruses.
Happening shortly after the new year in 2003, the exploit was based on a proof of concept that had been discussed at Black Hat Briefings. A relatively small and unsophisticated piece of code, the malware would simply generate random IP addresses and forward itself to them where the process would simply start all over again.
Due to its simplicity and usage of the UDP protocol, the worm was able to fit inside a single packet. This would lead to a fire-and-forget type situation where the worm would fire off packets without requiring any further action.
Pwned!
Once it was in the wild all hell would end up breaking loose. Due to the type of attack and the fact the packets needed no authentication, once embedded on a machine the worm would simply spray packets across the internet. This caused large numbers of useless traffic levels which would slow legitimate traffic dramatically and eventually lead to a Denial of Service as the worm would be consuming most of the bandwidth.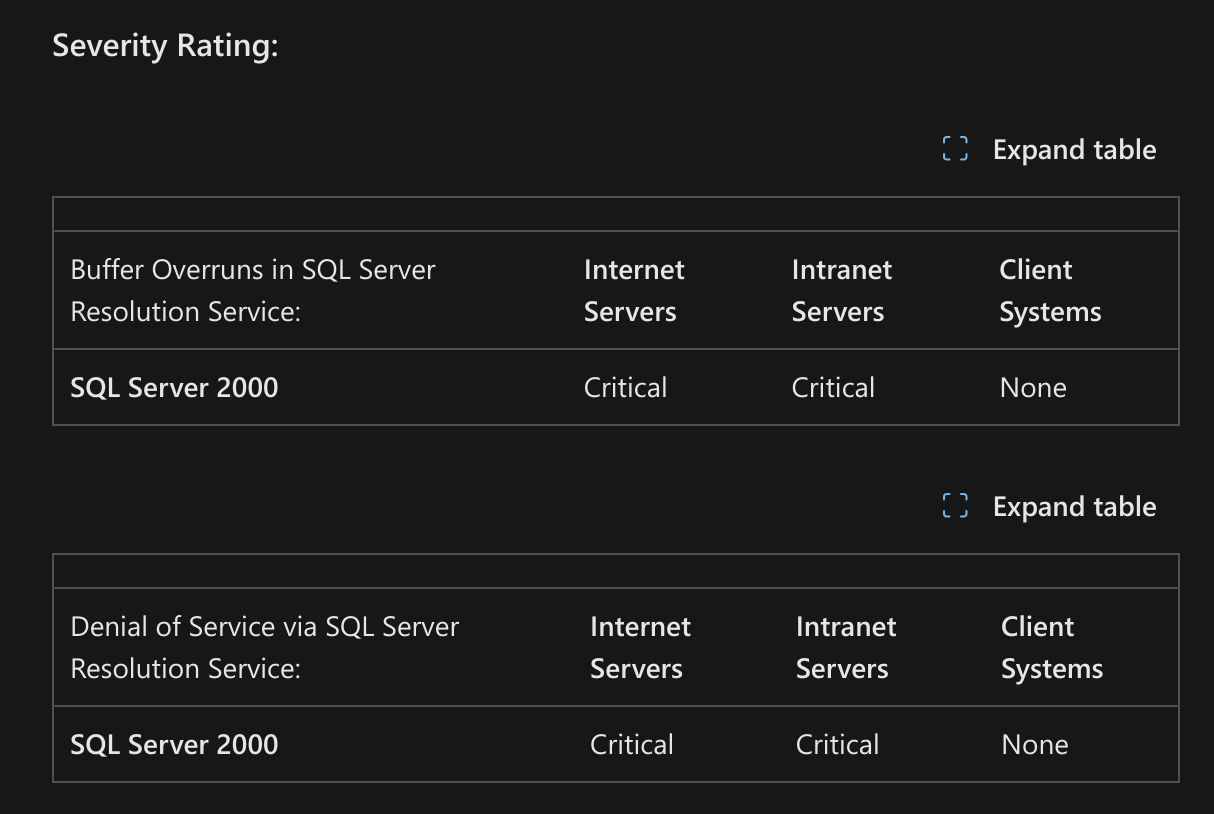 Despite the exploit being revealed nearly a full year earlier and the fact that a patch had existed for over six months, the simple reality of the situation was that most systems had never had the patch applied.
Despite the exploit being revealed nearly a full year earlier and the fact that a patch had existed for over six months, the simple reality of the situation was that most systems had never had the patch applied.
With almost perfect conditions to propagate, the virus went wild. At its peak, the number of infected machines was doubling every eight seconds or so leading to over 75,000 machines being exploited within a 10-minute window.
At this rate, legitimate traffic was struggling significantly, but due to its tiny size, the worm was still able to get through on occasions when other traffic could not. Destruction via efficiency, clearly!
One other point worth mentioning is that it wasn’t just personal machines that were affected. A large number of embedded systems like Automatic Teller Machines would end up falling prey to the worm as well.
A Ghost
Today, most exploits are identified. If someone hasn’t taken responsibility for the attack then often, they’ll be identified through other means. Sometimes it’s government authorities doing the enforcing and other times, Information Security specialists are able to apply their technical skills to identify who was responsible.
Interestingly enough, in this case for the most part, things were very quiet in the aftermath. There was no one claiming responsibility, no fingers were being pointed anywhere and the whole matter looked pretty suspect regarding ever being able to accurately identify a culprit. There were, however, a few considerations.
The first one was that it was the work of “Script Kiddies” who had released the malware without fully grasping its consequences. Another claim was that the malware escaped from a research lab, before going rouge on machines out in the wild. Exactly which lab or researcher was being accused of this wasn’t named.
Often, we’ll see further details come to light with the passage of time but in this instance, we’re still left with far more questions than we have answers. In fact, it’s scenarios like this that make cybersecurity a very interesting topic to write about.
Legacy
The Dream
Due to the rapid proliferation of the worm and the fact that a patch existed, the worm would have a lasting effect on cybersecurity. Systems would now issue patches the instant they were pushed, and big money would be driven towards IT and cyber programs, helping to ensure that companies had the resources to correctly deal with and mange cyber incidents.
The Reality
The above paragraph sounds great but obviously, it’s not in the least true. Cybersecurity programs in most small businesses remain an afterthought and the reality is that there are many unpatched systems in the wild that are running critical infrastructure. The fact is, that we continue to make some of the mistakes that have caught us out in the past.
Final Considerations
The reality is that for a lot of people, security simply isn’t worth worrying about. It’s either not a concern or someone else's problem to deal with. While this isn’t really accurate, good luck convincing someone that money spent on a good defensive posture is money well spent.
As educators, one of the best things we can do is break down some of these problems in ways that people understand and can relate to. If we use too much jargon and paint a threat as unrealistically big or security as too difficult, then we risk losing the attention of those we are trying to engage.
The best results come from making things achievable and relatable to the end users. If you’re in IT or Infosec, then that's your job.
Medium has recently made some algorithm changes to improve the discoverability of articles like this one. These changes are designed to ensure that high-quality content reaches a wider audience, and your engagement plays a crucial role in making that happen.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
🌟 Enjoyed this article? Join the community! 🌟
📢 Join our OSINT Telegram channel for exclusive updates or
📢 Follow our crypto Telegram for the latest giveaways
🐦 Follow us on Twitter and
🟦 We’re now on Bluesky!
🔗 Articles we think you’ll like:
- What The Tech?! Rocket Engines
- OSINT Investigators Guide to Self Care & Resilience
✉️ Want more content like this? Sign up for email updates