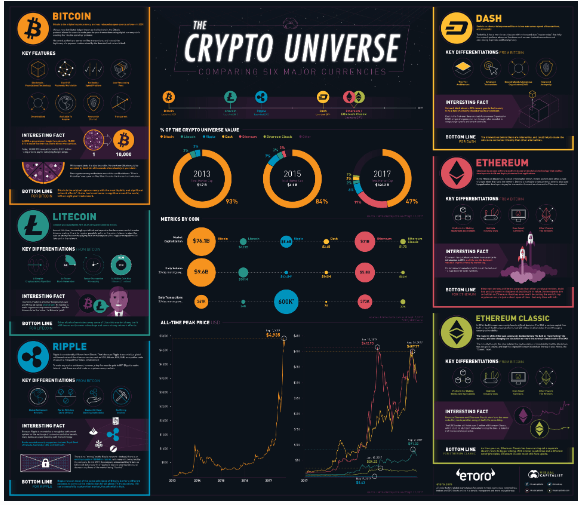
Shedding light on the ethical and technological aspects of hacking”
Title: “Shedding light on the ethical and technological aspects of hacking”
Abstract:
In the digital age, the term “hacking” evokes many connotations, from comes to creative problem solving. This article begins a nuanced exploration of computer hacking, delving into its historical roots, ethical implications, and technological manifestations in contemporary society. In dissecting the multifaceted nature of hacking, we identify the blurred lines between security exploitation, creative discovery, and ethical innovation. Through case studies and
expert opinions, we explain the complexities of hacking culture, its impact on cybersecurity, and its role in shaping the technical landscape number of the 21st century.
Introduction:
Computer hacking has evolved from a subversive pastime carried out in the shadows into a widespread phenomenon shaping the digital frontier.Its origins lie in the playful tinkering of early computer enthusiasts who sought to push the boundaries of technology and explore its untapped potential. However, as technology advances and networks expand, hacking has taken on new dimensions, crossing the line between innovation and exploitation. In this article, we begin our journey to explore the multifaceted nature of hacking, examining its historical context, ethical dilemmas, and transformative impact on society
Part 1: The Evolution of Hacking
Traces the evolution of hacking from its origins in the 1960s counterculture to its current manifestations in cybersecurity and digital activism. Explore the pioneering efforts of hackers like Richard Stallman and the ethos of the early hacker community, driven by curiosity, collaboration, and a fervent belief in freedom of information. Walk through important milestones in the history of hacking, from the birth of phreaking to the emergence of computer viruses and the rise of
hacker collectives like Anonymous. By examining the sociopolitical context surrounding computer hacking, learn about the tensions between individual freedom, corporate control, and state surveillance.
Part 2: Ethical Dilemmas in Hacking
Navigate the ethical minefield of hacking, where the lines between good and evil blur in the quest for knowledge and power.Explore the ethical frameworks that govern hacking activities, from the ethics of information sharing to the legal and ethical implications of unauthorized access and data breaches. Dive into case studies of ethical hacking initiatives, where hackers work with organizations to identify and remediate security vulnerabilities. Contrast these efforts with the dark side of hacking, where malicious actors exploit vulnerabilities for personal gain or geopolitical influence. , by examining real-world scenarios and ethical debates, confronts the ethical complexities inherent in hacking culture.
Part 3: The Technological Frontier of Hacking
Enter the cutting-edge field of cybersecurity research, where hackers and security experts engage in a never-ending game of cat and mouse to discover vulnerabilities and enhance defense. Explore the methods and tools hackers use to break into systems, from phishing and social engineering attacks to zero-day exploits and cryptographic vulnerabilities. Dive into the world of bug bounty programs and participate in chess competitions where ethical hackers demonstrate their skills and contribute to the overall security of cyberspace. By dissecting the architecture of cyberattacks and defense strategies, you will better understand the changing landscape of digital warfare and the urgent need for cybersecurity resilience in a connected world.
Conclusion:
Hacking represents a paradoxical duality, both a symbol of innovation and disruption, liberation and exploitation.As we navigate the complex terrain of the digital age, it is imperative to cultivate a deep understanding of hacking, its historical legacy, and its ethical dimensions.By promoting a culture of disclosure, responsible collaboration and digital literacy, we can harness the transformative potential of hacking for the greater good of society. In the ever-expanding frontier of cyberspace, let us tread carefully, mindful of the ethical imperatives that are shaping the technological landscape and determining our shared future.
Title: “Hacking: Demystifying the Digital Frontier”
Summary:
The world of hacking is a multifaceted landscape, evolving with technology and leaving an indelible mark on our connected society our. This article explores different areas of hacking, from ethical hacking and cybersecurity to darker malicious activities. By delving into history, techniques and ethical considerations, we identify the thin line between digital capabilities and cyber threats. By examining the motivations that drive hackers, the rise of hacking culture, and the ongoing battle for cybersecurity, we gain insight into a sector that is simultaneously driving innovation and setting new expectations. unprecedented challenge for hackers in the digital age.
Introduction:
As our lives become increasingly intertwined with technology, the term “hacking” arouses both curiosity and concern.In this article, we embark on a global exploration of hacking, aiming to shed light on its various aspects. From the pioneers of ethical hacking to the shadowy figures involved in cybercrime, we delve deeper into the history, motivations and ethical considerations that shape the world hack.
Part 1: The Evolution of Hacking
Tracing the origins of hacking from the early days of discovery and curiosity to the complex landscape of modern cyber threats. Explores the role of hacking in the development of computer systems, the emergence of hacker subcultures, and the transformative impact of information technology. Learn about the ethical dilemmas surrounding computer hacking as it has evolved from a subversive activity into a valuable skill set in both legal and illegal contexts.Part 2: Ethical Hacking and Cybersecurity
Enter the field of ethical hacking, where skilled individuals leverage their expertise to identify and remediate vulnerabilities in technical systems number. Explore the methods used by ethical hackers in penetration testing and vulnerability assessments. Dive into the world of cybersecurity, where experts strive to protect digital assets from malicious attacks. Consider the symbiotic relationship between ethical hackers and cybersecurity, working together to strengthen the digital frontier.
Part 3: Malicious Hacking and Cybercrime
Explore the dark side of hacking, where malicious actors exploit vulnerabilities for personal gain or disruption. Explore the motivations that drive cybercrime, from financial incentives to ideological conflicts. Investigate the major cyberattacks that have shaped the digital security landscape and analyze the tactics used by malicious hackers. Examines the legal and ethical challenges of fighting cybercrime as law enforcement and security professionals grapple with the elusive nature of online threats.
Part 4: Hacking culture and innovation
Learn about the dynamic culture surrounding hacking, from hacker conferences to online forums that promote knowledge exchange.Explore the symbiosis between hacking and technological innovation, as hackers help push the boundaries of digital possibility. Consider the ethical considerations of responsible disclosure and the ongoing debate around hacktivism – the use of hacking skills for political or social ends.
Conclusion:
In the digital age, hacking is a driving force that is shaping our technological landscape. As we marvel at the ingenuity of ethical hackers and the innovation fueled by hacking culture, we must also address the challenges posed by cyber threats and malicious hacking. By promoting a deeper understanding of hacking and promoting ethical practices, we can resiliently cross digital borders and ensure that the benefits of technology are harnessed wisely. responsible for the prosperity of society.
Title: “Revealing the Layers of Hacking: From Art to Threat”
Summary:
Hacking, once limited to the IT sector, has become a multifaceted phenomenon penetrating every aspect of our digital and physical lives. This article delves into the maze of hacking, revealing its diverse manifestations, from the ingenious exploits of ethical hackers to the sinister schemes of cybercriminals. By tracing hacking's historical roots and dissecting its contemporary manifestations, we navigate the ethical, legal, and social implications of hacking in the digital age. From the challenges of cybersecurity to the ethics of information freedom, hacking appears not only as a technical task but also as a reflection of human ingenuity, curiosity, and the endless search for knowledge. knowledge and power.
Introduction:
Hacking, a term once synonymous with subversion and cybercrime, has transcended its negative connotations to become a symbol of innovation, creativity, and technological prowess.As the digital landscape expands and becomes interconnected, the lines between hacking as an art form, a tool of discovery, and a weapon of disruption are blurring. In this article, we begin our journey to explore the multifaceted nature of hacking, from its humble origins in MIT computer labs to its ubiquitous presence in the global cyber ecosystem. bridge.
Part 1: The Evolution of Hacking
Travel through the annals of history to discover the origins of hacking, from the pioneering exploits of early computer enthusiasts to its emergence of hacker subcultures in the 20th century. Explore the philosophy of exploration and experimentation that underpinned early hacker communities, from the Homebrew Computer Club to the legendary exploits of the Railroad Club MIT Technology Model. Follow the evolution of hacking techniques and technologies, from phone hacking and network intrusion to the emergence of ethical
hacking as a profession.Through case studies and historical anecdotes, gain a better understanding of hacking's transformative impact on technology, society, and the human imagination.
Part 2: The Ethical Hacker's Arsenal
Enter the world of ethical hacking, where white hat hackers use their skills for the greater good of cybersecurity. Explore the methods and tools used by ethical hackers to identify vulnerabilities, assess risk, and strengthen digital defenses against malicious actors. Dive into the ethical dilemmas facing cybersecurity professionals, from the limits of responsible disclosure to the tensions between privacy and security. Through real-world examples and an ethical framework,
examines the role of ethical hacking in protecting critical infrastructure, protecting sensitive data, and promoting a culture of digital resilience.
Part 3: The Dark Side of Hacking
Delve into the dark underworld of cybercrime, where black hat hackers exploit vulnerabilities for personal, political and nefarious purposes.Learn about the tactics and techniques used by cybercriminals, from phishing and ransomware to sophisticated attacks against nation-states. Explore the economic motivations behind cybercrime, from the lucrative business of data theft to secret markets on the dark web. Through case studies and forensic analysis, confront the harsh reality of cyber threats and their profound impacts on individuals, businesses and society at large.
Part 4: Ethical and legal implications
Navigate the complex legal and ethical landscape surrounding hacking, from the patchwork of cybersecurity regulations to digital ethics principles and human right. Examines the tension between security and privacy, freedom of expression and the rule of law in the digital age.Explore the role of government agencies, law enforcement, and international cooperation in combating cyber threats and promoting responsible cybersecurity practices. Through interdisciplinary perspectives and stakeholder engagement, explore innovative approaches to address the ethical and legal challenges of hacking in the evolving digital landscape fast.
Conclusion:
Hacking demonstrates the duality of human nature, reflecting both our capacity for innovation and our vulnerability to exploitation. As we navigate the complexities of the digital age, the ethical and social implications of hacking become important, requiring careful consideration, proactive engagement, and collective action. Whether used as a force for good or a malicious tool, hacking reminds us of the power of technology to shape our world and the imperative of ethical stewardship in its use. use it.In our pursuit of digital empowerment and security, let us harness the spirit of hacking to build a more resilient, equitable, and ethical future for all.