Enhancing Cryptocurrency Wallet Security: Comprehensive Factors for Robust Protection
- Private Keys:
- Private keys are essentially the passwords that grant access to your cryptocurrency holdings. They must be kept secret and secure at all times.
- Avoid sharing your private keys with anyone, and never enter them on websites or platforms unless you're absolutely certain of their legitimacy.
- Store private keys in a secure manner, preferably offline in a hardware wallet, paper wallet, or encrypted storage.
- Consider using passphrase-protected private keys for an added layer of security.
- Backup and Recovery:
- Regularly backup your wallet's seed phrase or private keys in multiple secure locations, such as encrypted USB drives, paper backups stored in a safe, or secure cloud storage (if encrypted).
- Ensure that your backup is stored in a location where it is unlikely to be damaged or accessed by unauthorized individuals.
- Test your backup and recovery process to ensure it works effectively in case of emergencies.
- Two-Factor Authentication (2FA):
- Enable 2FA wherever possible, especially for online wallets and exchanges.
- Use an authenticator app or hardware token for 2FA instead of relying solely on SMS authentication, which can be vulnerable to SIM swapping attacks.
- Store backup codes for 2FA securely in case you lose access to your primary 2FA device.
- Security Updates:
- Regularly update your wallet software to the latest version to patch any known security vulnerabilities.
- Subscribe to security alerts and notifications provided by wallet providers to stay informed about any emerging threats or updates.
- Secure Environment:
- When accessing your wallet, ensure you are on a secure network, preferably a trusted home network rather than public Wi-Fi.
- Use trusted devices that are free from malware and other security threats.
- Consider using a dedicated device or operating system for cryptocurrency transactions to minimize the risk of compromise.
- Phishing Awareness:
- Be vigilant against phishing attempts, which often involve fake websites, emails, or messages designed to trick users into revealing their private keys or login credentials.
- Always verify the authenticity of websites and messages before providing any sensitive information.
- Use bookmarks and type URLs directly into the address bar instead of clicking on links from unsolicited emails or messages.
- Transaction Verification:
- Before confirming any cryptocurrency transaction, double-check the recipient address, amount, and transaction fee to ensure accuracy.
- Verify the transaction details on multiple devices or wallets if possible, especially when dealing with large sums of cryptocurrency.
- Diversification:
- Consider diversifying your cryptocurrency holdings across multiple wallets and storage methods to spread risk.
- Use a combination of hot wallets for convenience and liquidity and cold storage solutions for long-term storage and security.
By implementing these detailed security measures and best practices, cryptocurrency users can significantly reduce the risk of unauthorized access, theft, and loss of funds. Constant vigilance and proactive security measures are essential in the dynamic and evolving landscape of cryptocurrency.
- Wallet Selection and Reputation:
- Choose wallets from reputable and trusted providers with a proven track record of security and reliability.
- Research and review user feedback, ratings, and independent reviews before selecting a wallet.
- Avoid using wallets with a history of security breaches or poor security practices.
- Encryption and Password Management:
- Ensure your wallet and any associated backups are encrypted using strong encryption algorithms.
- Use strong, unique passwords for accessing your wallet and associated accounts. Consider using a password manager to generate and store complex passwords securely.
- Privacy and Anonymity:
- Consider the privacy features offered by the wallet, such as support for privacy-focused cryptocurrencies like Monero or Zcash.
- Implement additional privacy measures, such as using VPNs or Tor to obfuscate your IP address when accessing your wallet.
- Multi-Signature and Time-Locked Transactions:
- Utilize multi-signature wallets that require multiple private keys to authorize transactions. This adds an extra layer of security, especially for shared wallets or accounts.
- Explore time-locked transactions, which allow you to set a delay before a transaction is executed, providing a window for cancellation in case of unauthorized access.
- Cold Storage and Air-Gapped Solutions:
- Consider cold storage solutions for long-term storage of large amounts of cryptocurrency. Cold storage methods include hardware wallets, paper wallets, and offline computers or air-gapped devices.
- Keep the majority of your cryptocurrency holdings in cold storage, with only a small amount held in hot wallets for day-to-day transactions.
- Security Practices for Exchanges:
- Exercise caution when storing cryptocurrency on exchanges, as they are prime targets for hacking and security breaches.
- Only keep funds on exchanges that are needed for trading, and withdraw funds to your personal wallet for long-term storage.
- Enable additional security features offered by exchanges, such as withdrawal whitelists and IP address restrictions.
- Regular Security Audits and Monitoring:
- Conduct regular security audits of your wallets and associated devices to identify and address any vulnerabilities or weaknesses.
- Monitor your wallet and transaction history for any suspicious activity, such as unauthorized logins or unexpected transactions.
- Stay informed about the latest security threats and best practices through reputable sources and communities within the cryptocurrency space.
By considering these additional factors and incorporating them into your cryptocurrency security strategy, you can enhance the protection of your funds and minimize the risk of unauthorized access or loss. Remember that security is an ongoing process that requires diligence and proactive measures to stay ahead of potential threats.
- Physical Security:
- Protect physical access to hardware wallets, paper wallets, or any other physical storage mediums where private keys are stored.
- Store hardware wallets and backup devices in a secure location, such as a safe or safety deposit box, to prevent theft or physical damage.
- Be cautious when traveling with hardware wallets or backup devices, and avoid exposing them to potential theft or loss.
- Social Engineering Awareness:
- Be wary of social engineering attacks, where attackers manipulate individuals into divulging sensitive information or performing actions that compromise security.
- Be cautious of unsolicited communication, especially requests for private keys, passwords, or other sensitive information.
- Educate yourself and your team about common social engineering tactics and how to recognize and respond to them effectively.
- Regular Security Training and Education:
- Invest in ongoing security training and education for yourself and your team members to stay informed about the latest security threats and best practices.
- Stay up-to-date with advancements in cryptocurrency security technology and methodologies through conferences, webinars, and industry publications.
- Foster a culture of security awareness and responsibility within your organization or community to promote proactive security measures and risk mitigation.
- Disaster Recovery Planning:
- Develop and maintain a comprehensive disaster recovery plan for your cryptocurrency holdings, including procedures for recovering from various types of security incidents or data loss.
- Regularly review and test your disaster recovery plan to ensure its effectiveness and make any necessary updates or improvements.
- Consider factors such as data backup strategies, emergency communication protocols, and alternative storage options in your disaster recovery planning efforts.
- Legal and Regulatory Compliance:
- Stay informed about the legal and regulatory requirements relevant to cryptocurrency ownership and storage in your jurisdiction.
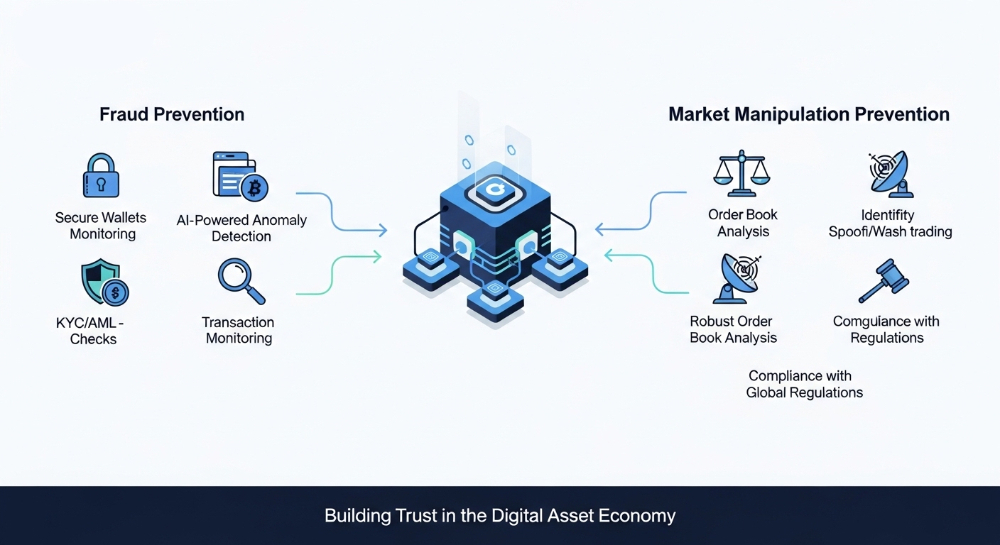
- Ensure compliance with relevant regulations, such as anti-money laundering (AML) and know your customer (KYC) requirements, to avoid legal repercussions and financial penalties.
- Seek guidance from legal and regulatory experts to ensure that your cryptocurrency operations are conducted in accordance with applicable laws and regulations.
- Community and Peer Reviews:
- Participate in cryptocurrency communities and forums to share knowledge, exchange ideas, and collaborate on security-related topics.
- Engage with peers and experts in the cryptocurrency space to solicit feedback and reviews of your security practices and infrastructure.
- Contribute to open-source projects and initiatives aimed at improving cryptocurrency security and fostering collaboration within the community.
By incorporating these additional factors into your cryptocurrency wallet security strategy, you can further strengthen the protection of your funds and assets against a wide range of threats and risks. Remember that security is a collective effort that requires ongoing attention, collaboration, and adaptation to emerging challenges and opportunities.