What is Privacy in Web3?
What is Privacy in Web3?
An Exploration of the Different Conceptions and Approaches to Privacy in Web3
Fishy On-Chain
Introduction
For Web3, privacy is the elephant in the room. It is at once crypto’s biggest selling point, going hand in hand with the principles of decentralization, anonymity, and trustlessness, and its biggest pain point, with excruciating KYCs, easily trackable PII, and an ever-suspicious gaze from the outside world.
Unfortunately, this is also a topic that is largely misunderstood and misconceived, with many people viewing crypto “privacy” as simply an excuse to finance terrorists and conduct money laundering. The fact that crypto Twitter prides itself for its “anon culture” and that mainstream media often (intentionally or unintentionally) reinforces these biases doesn’t help a case in dissolving these stereotypes.
Because Web3 privacy is such an all-encompassing concept, touching upon everything from ape profile pictures to cryptography and Zero Knowledge Proofs, its useless to talk about it in the aggregate, and make lump-sum judgements on whether it is good or bad. Instead, we must break down the problem into different smaller segments. In this essay, I will first break down and analyze Web3’s “privacy” infrastructure at three distinct levels — network level privacy, protocol level privacy, and user level privacy — before exploring the role that technological solutions such as Zero Knowledge Proofs play in the future of Web3 privacy.
Network Level Privacy
The first and oldest conception of privacy is at the network level. Network level privacy is where every transaction of a cryptocurrency on a given blockchain network is guaranteed privacy through underlying consensus mechanisms of the blockchain and network-level design choices. As such, these are also called “privacy coins.”
This conception of privacy traces its roots all the way back to the Bitcoin protocol, and its idea of anonymizing “wallet addresses” as 160-bit cryptographic hashes [1]. While Bitcoin itself has fully transparent transactions, where any user can inspect any transaction on its network, Bitcoin’s design principles of decentralization and anonymity have undoubtedly inspired the driving force behind the development of “network level privacy” and privacy-first blockchains.
One of the leading projects in establishing network level privacy is Monero, a privacy-first blockchain established in 2014. Unlike Bitcoin, Monero hides both user wallets and transactions behind “Ring Signatures,” in which users within a given “ring” have access to a certain group signature, and use that group signature to sign transactions. Therefore, for any given transaction on the Monero network, you can only tell that it comes from a certain group, but you don’t know which user in that group actually signed the transaction. In essence, this is a form of “privacy in the crowd,” in which users band together into groups in order to provide everyone with privacy. [2]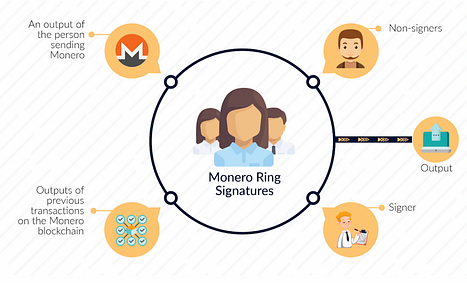
Ring Signatures in Monero. Source: https://blog.pantherprotocol.io/ring-signatures-vs-zksnarks-comparing-privacy-technologies/ [3]
Another project that tackles this same space is ZCash, an early pioneer of a form of Zero Knowledge Proofs called zk-SNARKs which has been recently popularized. The fundamental concept behind Zero Knowledge Proofs is that it is a way of proving something is true without revealing any further information (which could compromise security and privacy) [4].
A simple example of a Zero Knowledge Proof is a Gradescope autograder [5]. You need to “prove” that you did your CS homework correctly, but don’t need to tell the autograder any further details about your code implementation. Instead, the autograder checks your “knowledge” through running a bunch of hidden test cases, and your code must match the “expected” output of the Gradescope autograder. Through matching the “expected” output, you can provide a Zero Knowledge Proof that you’ve done your homework without showing your actual code implementation.
In the case of ZCash, while transactions are by default transparent, users can choose to use these “Zero Knowledge Proofs” to create private transactions. When a user wants to send a transaction, they create a transaction message that includes the sender’s public address, the recipient’s public address, and the amount of the transaction, and then convert this into a zk-SNARK proof, which is the only thing sent to the network. This zk-SNARK proof contains all the necessary information to prove the validity of the transaction, but doesn’t reveal any of the details of the transaction itself. This means that the network can validate the transaction without knowing who sent it, who received it, or the amount involved.
Despite their design and implementation differences, for both Monero and ZCash the transaction privacy is guaranteed at the blockchain level, such that all transactions happening on the network are automatically guaranteed to be private. This privacy guarantee can be easily abused by bad actors to conduct money laundering, terrorist activities, and drug trafficking, and Monero is particularly notorious for its popularity on the Dark Web [6]. Furthermore, as Monero and other “privacy coins” become synonymous with illicit financial activities, this drives away users using these “privacy coins” out of legitimate privacy concerns, feeding a negative feedback loop that only results in a more harmful shadow economy.
This is the biggest drawback of guaranteeing privacy at the network level: it is an “all or nothing” approach in design, where there is a zero-sum tradeoff between the transparency of a transaction versus the privacy of this transaction. It is precisely because of this lack of transparency that “network level privacy” draws the most ire from regulators, and the reason why several major centralized cryptocurrency exchanges, such as Coinbase, Kraken, and Huobi have delisted Monero, ZCash, and other privacy coins in several jurisdictions [7].
Protocol Level Privacy
A different approach to privacy is to ensure “protocol level privacy,” where instead of hardcoding private transactions into the consensus level of the blockchain network, we process private transactions on a “protocol” or an “application” that runs on top of a blockchain network.
Because early blockchain networks, such as Bitcoin, had limited programmability, building “protocol level privacy” was incredibly hard to do, and it was much easier to fork the Bitcoin network and implement privacy from the ground up in the form of a new blockchain and “privacy coin.” But with the advent of Ethereum and the rise of “smart contracts,” this opened a whole new avenue for privacy-preserving protocols.
One of the most notable examples of “protocol level privacy” is Tornado Cash, which is a decentralized application (dApp) on Ethereum that “mixes” transactions together into a pool in order to guarantee transaction privacy — conceptually somewhat similar to Monero’s “blend in with the crowd” approach.
Tornado Cash protocol process. Source: https://messari.vercel.app/article/on-chain-privacy [8]
The Tornado Cash protocol roughly speaking has three main steps:
- Deposit: Users send their funds to a Tornado Cash smart contract. This initiates a private transaction with a randomly generated “anonymity set,” which is a group of users who are also making transactions at the same time.
- Mixing: Tornado Cash mixes the deposited funds with other users’ funds in the anonymity set, making it difficult to trace the original sender or recipient. This process is called “mixing” or “anonymizing.”
- Withdrawal: Once the funds have been mixed, users can withdraw their funds to a new address of their choice, breaking the link between their original address and the destination address. The user can then complete the transaction by sending the funds directly from the “new” destination address to the recipient. [9]
Unfortunately, in August 2022, Tornado Cash was sanctioned by the US government, as the Office of Foreign Assets Control (OFAC) alleged that North Korean hackers were using the protocol to launder stolen funds [10]. As a result of this crackdown, US users, companies, and networks are no longer able to use Tornado Cash. USDC stablecoin issuer Circle went a step further, freezing over $75,000 worth of funds connected to Tornado Cash addresses, and GitHub deleted the accounts of Tornado Cash developers [11].
This triggered a controversial storm in the crypto sphere, as many argued that with the vast majority of users using Tornado Cash for legitimate privacy-preserving transactions, and that protocol users should not be punished for the bad actions of a small minority. But importantly, because Tornado Cash is a “protocol level privacy” on Ethereum, rather than a “network level privacy” solution, the crackdown and fallout was restricted only to this one protocol on the Ethereum network rather than affecting the entire network — unlike Monero and ZCash, Ethereum didn’t get delisted from Coinbase because of these sanctions.
An alternate approach to “protocol level privacy” pioneered by the Aztec Network focuses on “rollups” to shield user funds and support private transactions. Aztec’s primary product is zk.money, which uses a 2-layer deep recursive Zero Knowledge Proof for both scaling and privacy. The first ZKP proves the correctness of the shielded transaction, ensuring that the transaction was in fact private and there was no informational leak. The second ZKP is used for the rollup itself, in order to bundle the computation of batches of transactions together and ensure that all of these were executed correctly [12].
While rollup-based “protocol level privacy” solutions are still in their early stages, they represent the next evolution of “protocol level privacy” solutions. One key advantage of rollup solutions over dApp-based “protocol level privacy” solutions such as Tornado Cash, such as their enhanced scalability, as the heavy-lifting of the computation largely happens off-chain. Furthermore, because much rollup research has been focused solely on increasing computation, there is still ample space for exploration in applying and extending these technologies into the privacy sphere.
User Level Privacy
A third (and most recent) approach to conceptualizing privacy in Web3 is through exploring “user level privacy,” where privacy guarantees are made for an individual user’s data rather than focusing on the data of the user’s transaction. In both the “network” and “protocol” level, we witness the recurring problem of a minority of bad actors (such as Dark Web transactions and money laundering schemes) affecting the use of the network and protocol for the innocent majority that are simply concerned for their personal data privacy.
The crucial point of “user level privacy” is that through focusing on individual users of a network itself, we conduct a “targeted” form of filtering where benign users and addresses are free to interact with the blockchain network privately, while bad users can be quickly filtered out. As you can imagine, this is a Herculean task, walking a fine line between transparency and privacy. This user-centric view of privacy also spawns an entire debate (and industry) about the role and future of decentralized identity (dID) adjacent and derived from the question of Web3 privacy [13]. For the sake of brevity, I will not discuss this question of KYC and authentication in Web3.
The core insight of “user level privacy” is to separate and reimagine the relationship between the user themselves and their wallet addresses on-chain, as wallet addresses are the atomic identifiers on a blockchain network. Importantly, there is a one-to-many mapping from users to chains: users often control more than one wallet address on each blockchain network they interact with. This is the idea of “on-chain identity fragmentation.” Thus, the crux of “user level privacy” is finding a secure way of mapping users’ personally identifiable information (PII) to all these fragmented on-chain identities.
A key project in this regard is Notebook Labs, which seeks to use Zero Knowledge Proofs to link fragmented identities together with a user’s PII [14], while providing the following guarantees:
- Users can prove their humanity with any fragmented on-chain identity
- It is impossible to link these identities together (unless the user’s secret key is leaked)
- It is impossible for any third party or adversary to link a fragmented on-chain identity to the user’s real-world identity
- Credentials can be aggregated across identities
- Each human receives a single set of fragmented on-chain identities [15]
While the cryptographic specifics of the protocol are beyond the scope of this essay, Notebook Labs demonstrates two core principles of “user level privacy” — the importance of addressing reimagining the relationship between the multitude of fragmented on-chain identities with real-world human users, as well as important role that Zero Knowledge Proofs play in aggregating and linking together all of these identities [16].
Another emerging solution to the question of “user level privacy” is the idea of “stealth wallets.” Again, the idea of “stealth wallets” capitalizes on the fragmentation of on-chain identities, using the fact that a user typically has more than one identity on-chain. Unlike Tornado Cash and other “protocol level privacy” solutions, which seek to obscure the transaction data itself, stealth addresses seek to obscure who the real people are behind the sender and recipient addresses. This is implemented through essentially finding an algorithm to quickly and automatically generate “one-time wallets” for a user’s transaction [17].
One important conceptual difference between “stealth wallets” and previously discussed privacy solutions such as Monero and Tornado Cash is that this is not a form of “privacy in the crowd.” This means that unlike Tornado Cash, which can only make privacy guarantees for mainstream token transfers such as ETH, stealth wallets can also provide security guarantees for niche tokens and NFTs, or unique on-chain assets that have no “crowd” to blend into [17]. Nonetheless, thus far the discussion of “stealth wallets” on Ethereum has remained at the theoretical stage, and the implementation effectiveness and legal repercussions of this novel technological solution are yet to be seen.
ZKPs and The Future for Privacy in Web3
As we can see, privacy is complicated in Web3. Different approaches to the problem — at the network level, at the protocol level, and at the user level — invite different solutions to it, and explore different tradeoffs between transparency and privacy. That said, any discussion of privacy is incomplete without considering the flip side of the coin: transparency and accountability.
For better or for worse, regulators are right in saying that there needs to be a greater accountability in cryptocurrency transactions. Bad actors engaged in money laundering, terrorist activities, and financial fraud should be held accountable, regardless of whether they use fiat or crypto to complete their transactions. But hopefully, in Web3 this accountability can be achieved without governments resorting to shutting off privacy networks altogether and forcing people to use these blockchains “cryptographically naked.” Privacy should be seen as a basic right, and a measure of digital dignity.
For a long time, privacy and accountability were seen as a zero-sum game, where you could either hide your data and have privacy, or show your data and have transparency. The innovativeness of Web3 comes in its pioneering of elegant technological solutions, especially Zero Knowledge Proofs, to overcome this zero-sum dilemma. But the burden is on the Web3 community, not regulatory agencies, to show that these technologies can actually work in ensuring both privacy and accountability.
Far too often, Zero Knowledge Proofs are touted as the end-all-be-all for any privacy problem. But despite all their mathematical magic, ZKPs are far from being a panacea for all of Web3’s privacy concerns and have several critical drawbacks. Firstly, ZKPs are often highly specialized circuits used to prove a certain piece of information structured in a particular way. In general, they suffer from a lack of scalability and compatibility. Secondly, they are very expensive to create, run, and maintain, requiring orders of magnitude more of computation power than an equivalent non-ZKP program.
Thus, when thinking about ZKPs in the realm of privacy, the important question will always be “what” are you going to prove, and “why”? After all, there’s no free lunch, and designing a ZKP always will always come with a cost. It is just as irresponsible for tech evangelists to declare that ZKPs will solve everything in privacy as it is for regulators to shut down all privacy protocols.
Fundamentally, privacy in Web3 is not just an engineering question; it’s a first principles one. Ever since the release of the Bitcoin whitepaper and the commercial adoption of the blockchain, one of the foundational principles of Web3 is its emphasis on trustlessness — where you don’t need to trust information to any party that could potentially turn that trust against you. A network can only truly be trustless when its users’ privacy is guaranteed through a decentralized, transparent, and unbiased manner.
So what should privacy look like in Web3? That’s the most pressing question for us to decide.