Uniqueness Of Ethereum's Security.
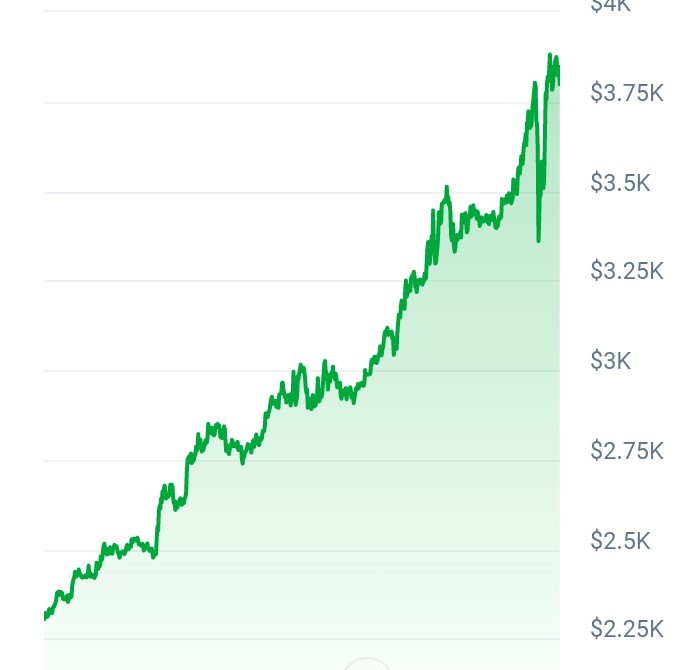
Ethereum (ETH) is one of the most powerful, stabilized and prominent asset in crypto currency World which has $459 billions market cap ( on the time of writing these lines) with almost 19% share of crypto. It stands on second place right after Bitcoin in coin position by Cap & Rank. The recent flash of crypto market spike put price of Ethereum at $3800 today. Ethereum gained 150% growth within couple of months after Bitcoin ETFs approval because Eth ETFs are on the table of SEC to approve.
Ethereum is a decentralized open-source blockchain platform that enables the creation of smart contracts and decentralized applications (dApps). Ether (ETH) which is used to pay for transactions and computational services on the network. Ethereum works in four layers parallel
as follows ,
- Web interface for users to interact with the Ethereum blockchain and perform transactions.
- Database for Ethereum clients to store the blockchain data.
- Cryptographic mechanisms for security purposes.
- Internet infrastructure to support blockchain communications among Ethereum nodes.
Key features of Ethereum's security
Consensus algorithm.
Ethereum uses a consensus algorithm called Proof-of-Stake (PoS) to secure the network.This means that instead of relying on miners to validate transactions and create new blocks, Ethereum uses "stakers" to secure the network. Stakers deposit Ether as collateral to become validators and are rewarded with newly minted Ether for their efforts.
Smart contract security.
Ethereum's smart contracts are self-executing contracts with the terms of the agreement between buyer and seller being directly written into lines of code. Smart contracts are stored on the Ethereum blockchain and are secured using cryptographic techniques. However, vulnerabilities in smart contract code can lead to security breaches.
Immutability.
Once a transaction is recorded on the Ethereum blockchain, it cannot be altered or deleted. This means that all transactions are permanent and transparent, making it difficult for malicious actors to tamper with the network.
Security audits.
Ethereum's code is regularly audited by security experts to identify and fix vulnerabilities. The Ethereum community also runs bug bounty programs to incentivize white-hat hackers to find and report vulnerabilities.
Defense mechanisms.
Ethereum has several defense mechanisms in place to protect the network from attacks, including the ability to revert transactions and block malicious actors from accessing the network.
Upgrading evolve.
Ethereum community is active and keep Hawkeye on development in crypto field and look into requirements of users. The implementation of zk-SNARKs, zk-STARKs, confidential contracts, and robust security measures ensures user privacy and protection against fraudulent activities. Then ETH 2.0 , proposal of ETFs and Layer2 protection are main things which has been implemented.
These features making ethereum more unique, vibrant and dynamic.According to CoinMarketCap there are approximately 200 million Ethereum wallets in existence which is proof of its credibility and integrity.
That's all for today. Like , upvote and leave comments for feedback. I was absent from here for a week due to some wedding ceremonies in other part of my country which didn't allow me to stay active here. But thanks God all is over and now with you all.
Note: The article also published on Publish0x.
Cheers,
Amjad