How Smart Contract Audits Are Used to Scam You
How Smart Contract Audits Are Used to Scam You

 NEFTURE SECURITY I Blockchain Security
NEFTURE SECURITY I Blockchain Security
·
Follow
Published in
Dissecting Web3
14 min read
·
Apr 14, 2023
Listen
Share
More W
W
eb3 can be a minefield for users and actors alike. When they don’t fall for fraudulent projects, they become victims of hackers.
The situation is getting worse every year, with 2022 seeing a total of $84,8 million lost to hacks and fraudulent projects.
All in all, web3 is a space in dire need of security, safety, and a measure of control.
Users and builders alike need assurance that it’s safe enough to invest in.
Nobody wants to enter, interact with, or stay in a space where they’re only a few clicks away from losing everything to scammers or a Casa de Papel-style crypto heist that leaves devastation in its wake.
So, what has been used by web3 actors to build this high-in-demand trust ?
Smart Contract Audits.
Since 2020, code auditing performed by third parties has become the default expectation for reputable DeFi platforms.
They serve a dual function:
1 — They “secure” the DeFi protocol
2 — They are a stamp of security and legitimacy approval for potential users
Today’s discussion will not be about the security (or lack thereof) paradigm in Web3 and how the existence of smart contract audits has become the go-to excuse for some Web3 builders to ignore bad code, have a zero security budget, and exempt themselves from the necessary ongoing commitment to the security and safety of their users.
Nope, that’s a discussion for another day.
Today, we will explore how the ingrained idea that audit means security has been artfully used by fraudsters to trick people into putting their trust and hard-earned money into their bogus projects.
When Audits Equate Trust
Web3 users overall suffer from a serious affliction: thinking that a project is secure just because it has been audited. And they certainly cannot be blamed for this.
Web3 builders have been using audits as a marketing strategy tool for the past few years. For crypto projects, being perceived as safe means gaining the trust of potential users, which translates to “Money! Money! Money!”
As soon as they launch or announce their projects, they will claim that it is safe and will be audited by top audit powerhouses to prove it.
In web3, safety equals audits. Period.
In this Wild Wild West, audits and audit companies like Certik, Peackshield, Hacken, Slowmist, etc., are perceived as the only barriers that seem to exist between safety and unfathomable risks for web3 users. On paper, audits protect a project from hackers, and protect users from fraudulent projects with built-in backdoors or other shenanigans.
Audits offer the delusion that they are somehow protected, somehow safe. Otherwise, how could they choose to actively participate in a project that could turn them into easy prey?
This almost blind trust of web3 users in audits could not be better illustrated than in one of the leading audit firms, Peackshield’s disclaimer. At the very last line, it reads:
“Last but not least, this security audit should not be used as an investment advice.”
Scammers caught on to that pretty quickly.
This vulnerability of them.
The art of scam is eliciting trust where none should be felt. And since trust is (partially) built on audits on web3, audits would, of course, be used as a tool of choice to lure people into lowering their cautiousness.
The most classic MO used by your average joe scammer is creating fake authentication by audit firms and slamming a Certik or Peckshield logo on their website, forcing these same firms to issue statements that this or this project was not audited by them every week, sometimes multiple times a week. These fraudulent projects are easy enough to debunk, suffice to go to the concerned audit firm’s website and type the name of the project that pretends to be audited by them and check if it’s the case.
Although unfortunately, it seems easy enough to debunk them, people still fall for these scammers, since most of them do not think that they would be able to understand an audit, so they do not check if they really exist or if they are legitimate or not.
But this, again, is not the subject of this article.
Although fake audits are an issue on their own, the true looming and worrying issue is the use of real audits to sell fraudulent projects.
Real Audits, Fraudulent Projects
What could be more powerful for a web3 hoax than an honest-to-God audit?
Nothing.
So, of course, some very patient scammers who don’t mind building and running their sham for months if not years, choose to use genuine smart contract audits to build trust in their deceitful project.
How so?
1 — Selecting what is going to be audited
Fraudsters profit from the idea that most web3 users assume that when a project says they have been “audited”, it means everything that needs to be audited has been audited, especially the most vulnerable to attack or backdoor exploit code.
When it’s absolutely not the case.
As Certik underlines in its disclaimer:
“CertiK conducts security assessments on the provided source code exclusively.”
They follow up with an unhelpful:
“Conduct your own due diligence before deciding to use any info listed on this page.”
Well, if every person could do their own due diligence on a smart contract or project, why would there be a need for audit firms?
Sigh.
This aside, audit firm Slowmist is even more extensive in explaining how their range of action and analysis is conditioned by what their clients provide:
“The security audit analysis and other contents of this report are based on the documents and materials provided to SlowMist by the information provider until the date of the insurance report (referred to as “provided information”). SlowMist assumes: The information provided is not missing, tampered with, deleted or concealed.
If the information provided is missing, tampered with, deleted, concealed, or inconsistent with the actual situation, the SlowMist shall not be liable for any loss or adverse effect resulting therefrom. SlowMist only conducts the agreed security audit on the security situation of the project and issues this report. SlowMist is not responsible for the background and other conditions of the project.”
Not only does an audit not provide a full assessment of a project, but the assessment is made on information provided by the clients.
Suffice to say, the owner of a fraudulent project only needs to audit an “harmless” smart contract and be able to claim on every platform that its project has been “audited”.
Maybe the worst part about it is that this myth of a project being foolproof when a single audit exists is perpetuated by standard actors.
On October 2, 2022, Transit Swap, a cross-chain DEX aggregator, was hacked for over $23 million.
At that time, when you visited their website, you could see that Transit Swap proudly underlined at the very place you would engage in a transaction on the platform that “Transit Swap aggregator contract is audited by Peckshield.” Here again, audits are used to claim loudly and proudly that the platform is safe as a whole, everything is safe, your funds are safe.
Here again, audits are used to claim loudly and proudly that the platform is safe as a whole, everything is safe, your funds are safe.
The message could not be more clear:
“You can interact with the platform safely because we have ensured that everything is secure through our audit.”
After the hack, when fingers were pointing at Peckshield for maybe not doing their job properly, they had to come forward to explain that “the exact contract being hacked is not part of the audit.” Uh oh.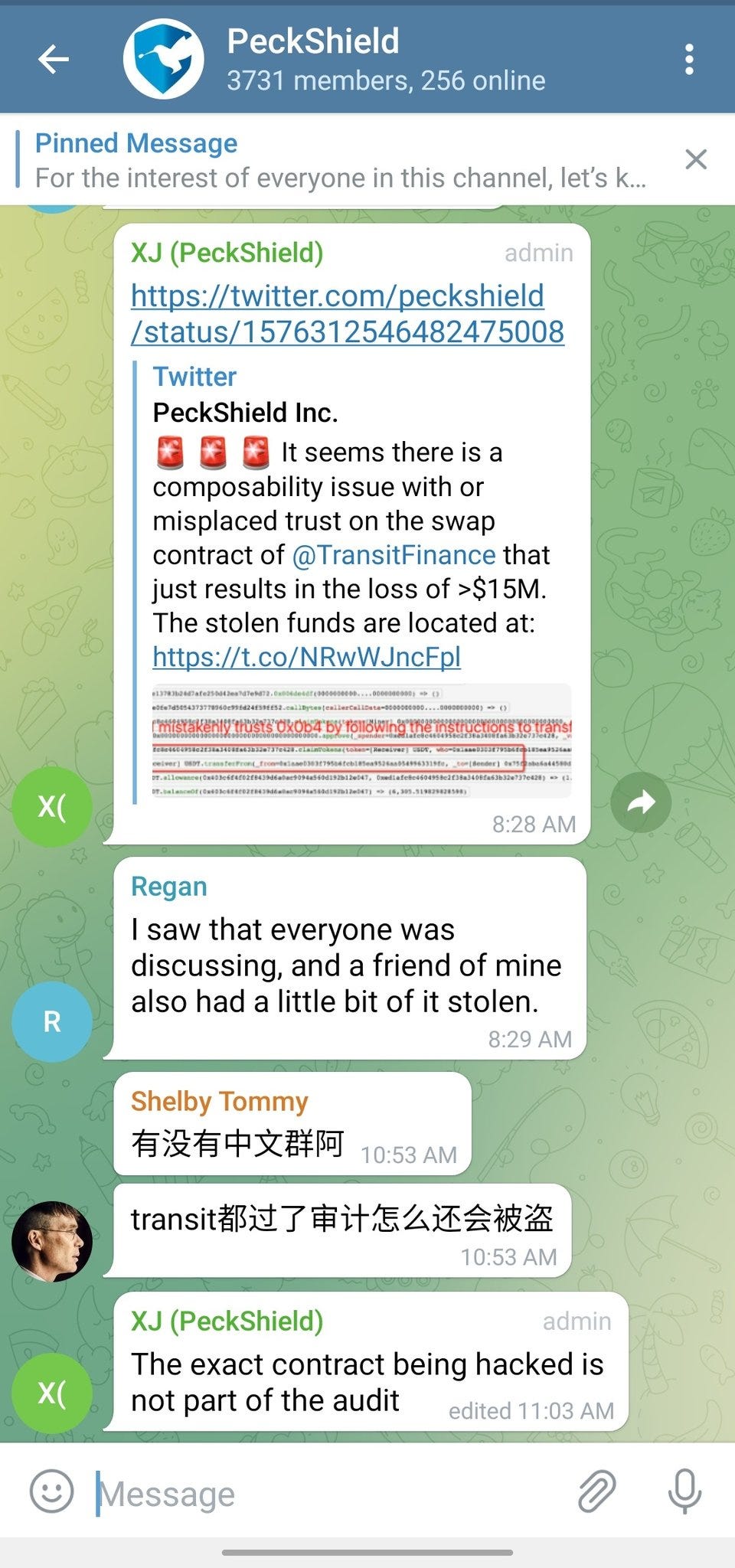 This is the perfect scenario to illustrate how it can be so easy for fraudsters to use smart contract audits to deceive people into blindly trusting them.
This is the perfect scenario to illustrate how it can be so easy for fraudsters to use smart contract audits to deceive people into blindly trusting them.
If even allegedly legitimate actors use audits to build trust by creating a sense of safety by only auditing part of their protocol while avoiding auditing smart contracts that could, once exploited, result in the siphoning of at least $23 million of their users’ funds, what is stopping bad actors from doing the same?
And how, if fraudsters and legitimate actors share the same self-serving mispractice built on the ignorance of what audits entail, will web3 users know who to trust and who to mistrust?
2 — Audits are not automatically corrective
Ignorance here again is key.
In general, when a web3 user will read that a smart contract has been audited, he will think that maybe issues have been spotted and then corrected by the auditing firm.
Profiting of the idea that most web3 users think that auditors systematically fix the issues encountered during an audit! When often it’s the project team’s job to implement security patches, if in the contract between the auditor and the audited there is not a close for rewriting the code to fix the security issues spotted.
3 — Counting on the fact that they are the clients of audit firms. An asymmetric dynamic that they can use to cover up mischief.
Life is tough for web3 audit firms.
That’s why they love their disclaimers, and do what in other industry actors could never fathom, sending their clients to rival firms.
As PeckShield put it:
“As one audit cannot be considered comprehensive, we always recommend proceeding with several independent audits and a public bug bounty program to ensure the security of smart contract(s).”
These audit firms are in a very peculiar position; the ones who pay the bill are the ones they are supposed to grill and discover if they are legit or not, fraudsters or not, have a backdoor that could allow them a crypto heist or not.
And depending on the terms of the contract or the position of the auditing firms, things that should not be overlooked are, and stamps of approval are given when they should not.
Audit firms can be subjected to extreme pressure by their clients to give them the pass when they should not. And for newer, more vulnerable, fragile audit firms, it could be too much to resist.
A striking example of this is when Certik, which is the undisputed web3 audit leading firm, had to face a defamatory and hate-filled campaign led by Safuu Protocol.
As previously explained, DeFi protocols love to announce their upcoming auditing process, sometimes the very day they have been born, which was the case for Safuu Protocol. They promised an audit from the highly trusted Certik, after they had already been audited by a firm called Solidity Finance!

































