Bridging the Gap in Cryptocurrency
Addressing Security Concerns in Token Bridges
In the realm of cryptocurrency, the concept of token bridges has emerged as a pivotal mechanism for interoperability between different blockchain networks. These bridges serve as vital conduits, facilitating the seamless transfer of assets across disparate platforms. However, beneath the veneer of convenience lies a pressing concern: the vulnerability of token bridges to malicious attacks.
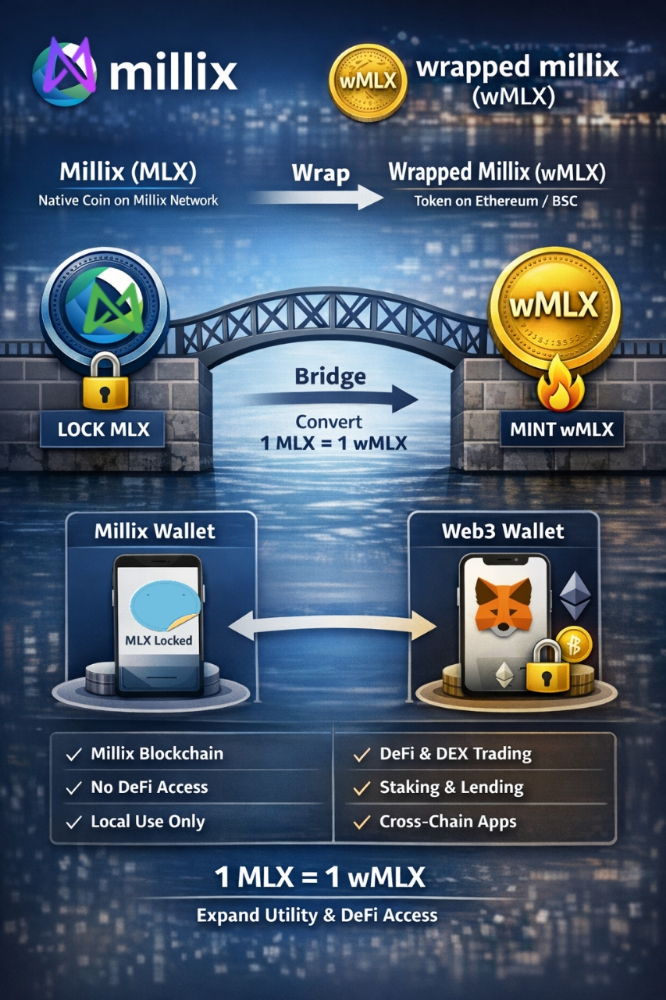
At the heart of the issue lies a fundamental misconception – the notion that digital assets traverse physical bridges akin to their real-world counterparts. In reality, cryptocurrencies and tokens do not physically move from one blockchain to another. Instead, token bridges function as intricate protocols that lock assets on one chain while issuing corresponding tokens on another. This process creates an illusion of movement without the assets ever leaving their original blockchain.
While this design offers unparalleled convenience and efficiency, it also exposes token bridges to a myriad of security risks. One of the most pressing concerns is the susceptibility to attacks. As centralized points of control, token bridges become lucrative targets for hackers aiming to exploit vulnerabilities and siphon off digital assets. A successful breach could result in devastating financial losses and undermine trust in the entire cryptocurrency ecosystem.
The decentralized nature of blockchain technology presents a paradoxical challenge. While decentralization is celebrated for its resilience against censorship and single points of failure, it also complicates the task of securing token bridges. Traditional security measures, such as firewalls and encryption, are insufficient in a decentralized context where control is distributed among numerous nodes.
Addressing the security concerns surrounding token bridges necessitates a multi-faceted approach. First and foremost, developers must prioritize rigorous testing and auditing to identify and rectify vulnerabilities in bridge protocols. Additionally, the implementation of robust cryptographic techniques, such as zero-knowledge proofs and multi-signature schemes, can bolster the security posture of token bridges.
Furthermore, the community must foster a culture of transparency and accountability. Projects responsible for deploying and maintaining token bridges should regularly disclose audit reports and undergo independent scrutiny to ensure compliance with best practices and industry standards. Open dialogue and collaboration among stakeholders are essential for identifying emerging threats and devising effective countermeasures.
Ultimately, the security of token bridges is a shared responsibility that demands proactive engagement from developers, users, and regulators alike. By acknowledging the inherent risks and implementing robust security measures, we can safeguard the integrity and stability of cryptocurrency ecosystems. Only through collective effort and vigilance can we bridge the gap between innovation and security in the ever-evolving landscape of digital finance.