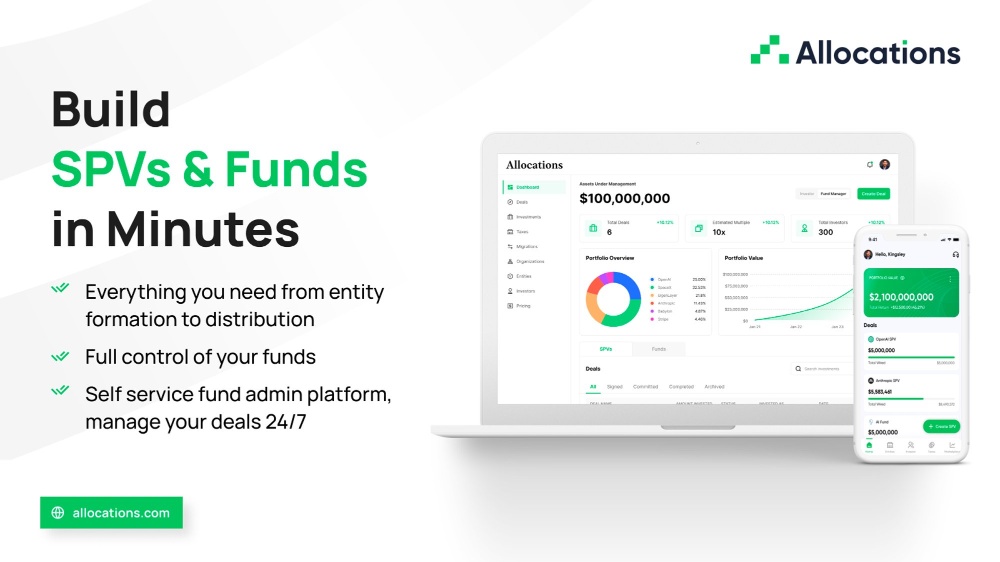
Decenterlized Crypto Wallet
Because of past hacks and breaks, most digital money trades have made their security conventions strong to guarantee their clients' assets and different subtleties. Notwithstanding these precautionary measures, it is dependably protected to store the crypto possessions in a presumed wallet-either equipment or programming. In this article, we will survey a product wallet called Trust Wallet, how to utilize Trust Wallet, what are its upsides and downsides, and so forth.
Programming wallets are applications introduced in your cell phones and in this manner can be worked whenever. However they are not generally so secure as equipment wallets, they are as yet a superior choice for putting away your crypto possessions as opposed to putting away them on a concentrated trade. Toward the finish of this Trust Wallet survey, merchants will actually want to check regardless of whether this wallet is a helpful choice for them
How Really does Believe Wallet Work?
The Trust Wallet portable application works in the accompanying ways:-
It goes about as an extension interfacing individual blockchain networks through their hubs. Each blockchain network has its own arrangement of public locations, frequently called the public key. Crypto resources are put away and encoded in these addresses.
Trust Wallet holds no cryptographic forms of money in its servers; it just gives clients admittance to its wallet.
It is an allowed to-utilize application that procures nothing when clients use it. Every one of the gas expenses (exchange handling charges) that are gathered are paid to the validators or diggers.
Trust Wallet assists clients with dealing with their public locations for sending and getting digital currencies. The application additionally permits clients to execute other crypto exchanges, such as exchanging and crypto marking.
According to our Trust Wallet survey, there are no obvious explanations not to qualify the versatile wallet as a solid one. Likewise, as indicated by the different other Trust Wallet Surveys accessible on the web, clients have lauded the wallet and considered it a safe multi-crypto wallet with next to no grievance. Its direct connection point and an immense scope of upheld resources make it one of the main crypto wallet till date. Trust Wallet plainly gives an upper hand to different wallets with its wallet marking functionalities that most wallets don't for even a moment give the choice to its clients.
Besides, the wallet presents clients the capacity to get to different DApps through Trust Wallet itself, which is again a far-located move that will have long haul benefits as DeFi grows. By utilizing Trust Wallets clients can likewise procure interest all alone crypto. Entrust Wallet's organization with Binance draws in additional clients (for cash financial planning) from everywhere the world and in this way is an or m
ore for the wallet.