Web3 & DeFi Security 101
Photo by Mika Baumeister on Unsplash
This is a CYW3B short guide intro on web security in the context of Web3 and Defi Security. Let's understand the potential threats and vulnerabilities that can compromise your digital assets.
This guide will equip you with the knowledge and tools to fortify your defenses and navigate decentralized finance like a true champion.
The Web3 Threats
The initial step in safeguarding your digital assets is understanding the various threats within the Web3 ecosystem.
By acquainting yourself with diverse risks—including hacking attempts, phishing attacks, smart contract bugs, and vulnerabilities—you enhance your preparedness for potential consequences arising from these threats.
Securing Web3 Applications | Mudit Gupta | TEDxBostonStudio
Awareness of these risks enables you to take proactive measures to mitigate the chances of falling victim to them. It helps to ensure the security of your valuable digital assets.
From hacking attempts and phishing attacks to smart contract bugs and vulnerabilities, let's explore the potential risks and consequences.
Hacking Attempts and Phishing Attacks
Hacking attempts and phishing attacks are prevalent in any digital ecosystem, and Web3 is no exception. Hackers often employ sophisticated techniques to gain unauthorized access to wallets, accounts, or private keys.
They may create fake websites or send deceptive emails to trick users into revealing sensitive information.
To protect yourself against hacking attempts and phishing attacks:
- Be cautious of suspicious emails or messages asking for your private keys or login credentials.
- Double-check the URL of websites before entering any sensitive information.
- Enable two-factor authentication (2FA) for an added layer of security.
Smart Contract Bugs and Vulnerabilities
Smart contracts are at the heart of DeFi platforms and protocols. However, they can contain bugs or vulnerabilities that attackers can exploit.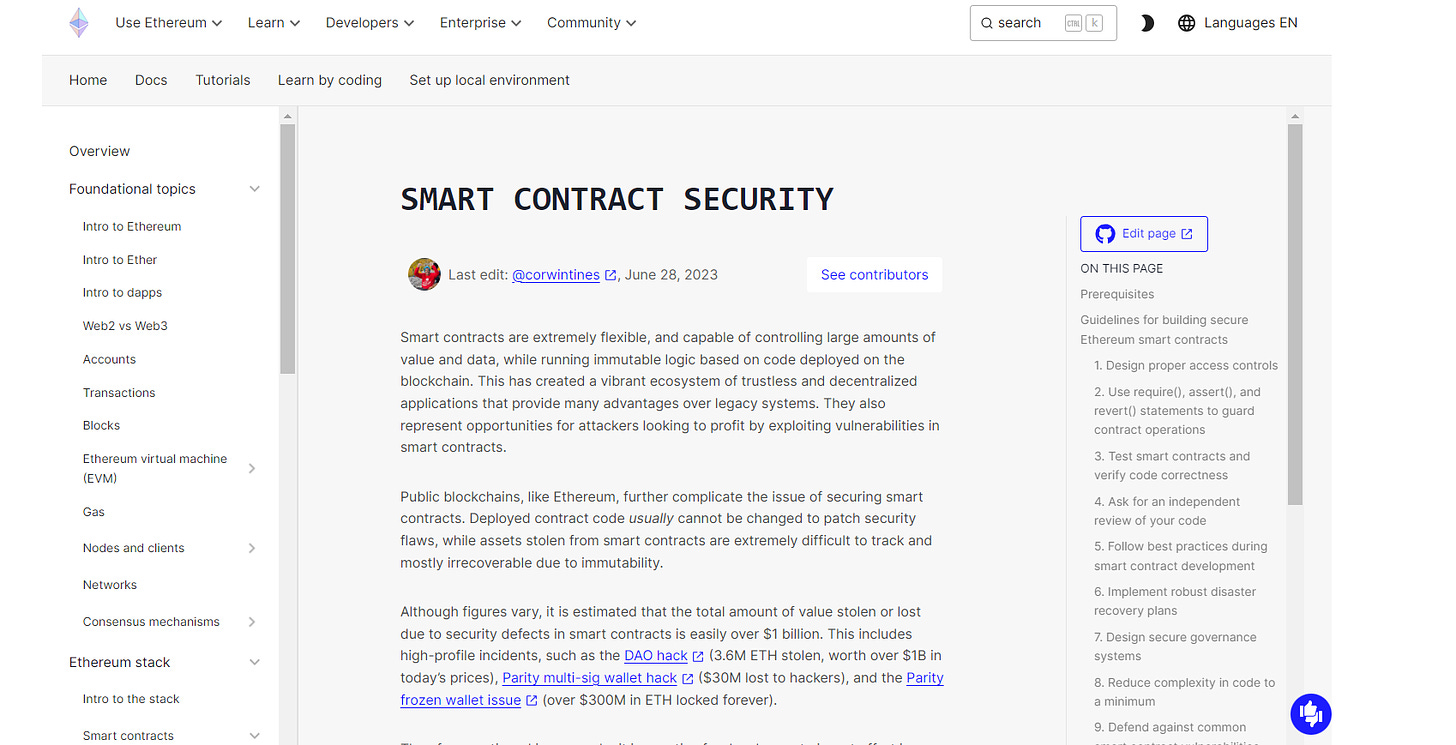
These vulnerabilities can lead to significant financial losses or even the complete collapse of a project.
To mitigate the risks associated with smart contract bugs and vulnerabilities:
- Choose DeFi platforms and protocols that have undergone thorough code reviews and security audits.
- Stay updated with the latest security advisories and patches for the projects you interact with.
- Consider using third-party tools that analyze smart contracts for potential vulnerabilities.
Strategies for Fortifying Your Defenses
Now that we understand the potential threats let's explore the strategies and best practices to help fortify your defenses in the Web3 and DeFi ecosystem.
Encryption and Secure Wallet Management
Encryption plays a crucial role in protecting your digital assets. Encrypting your private keys and sensitive information can ensure they remain unreadable even if they fall into the wrong hands.
To leverage encryption effectively:
- Use hardware wallets or cold storage solutions for storing your private keys offline.
- Utilize solid and unique passwords for all your online accounts.
- Consider using password managers to store and generate complex passwords securely.
Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide additional proof of identity. This can be a verification code sent to a mobile device or a biometric factor like fingerprint or facial recognition.
To enhance your security with MFA:
- Enable MFA wherever possible, especially for your wallets and exchange accounts.
- Utilize authenticator apps like Google Authenticator or hardware tokens for generating verification codes.
- Avoid relying solely on SMS-based authentication, as SIM-swapping attacks can bypass this method.
DeFi Security
DeFi, short for Decentralized Finance, is a term that refers to the use of blockchain, cryptocurrencies, smart contracts, and other technologies to disrupt and modernize the traditional financial system.
DeFi platforms allow users to lend, borrow, trade, earn interest, and manage assets in a decentralized manner.
Is DeFi Safe? Learn and Use These Security Measures
DeFi Security refers to the measures and practices implemented to protect these DeFi platforms and their users from hacking, fraud, technical failures, and other threats.
1. Smart Contract Audits - Smart contracts are the backbone of DeFi platforms. These self-executing contracts with the terms of the agreement directly written into code need to be thoroughly audited to ensure no bugs or vulnerabilities could be exploited.
2. Rug Pulls Prevention - Rug pulls occur when developers abandon a project and run away with users' funds. Measures need to be put in place to prevent such scenarios.
3. Insurance Cover - Some DeFi platforms offer insurance options for their users to cover potential losses due to unforeseen circumstances.
4. Secure Wallet Practices - Users are encouraged to adopt secure wallet practices like not sharing private keys and using hardware wallets for storing their cryptocurrencies.
5. Front-running Protection - Front-running is a practice where someone gets in front of a known future transaction to profit from it. Some DeFi platforms have mechanisms in place to prevent such actions.
DeFi Platforms and Protocols
You must conduct thorough due diligence before diving into any DeFi platform or protocol. This involves researching the project's team, auditing reports, community feedback, and overall reputation.
To conduct adequate due diligence:
- Please review the project's whitepaper and technical documentation to understand its underlying technology.
- Look for projects that have undergone security audits by reputable firms.
- Participate in community discussions and forums to gauge user experiences and feedback.
Continuous Monitoring and Risk Assessment
Safeguarding your digital assets requires continuous monitoring and risk assessment. By staying vigilant and proactive, you can identify potential threats early on and take appropriate measures.
1. Regularly Monitor Your Digital Assets
Regularly monitoring your digital assets lets you detect suspicious activities or unauthorized access promptly. Monitor your wallet balances, transaction history, and any unusual account behaviors.
2. Stay Up-to-Date with Security Advisories
Stay informed about the latest security advisories, patches, and updates related to the DeFi platforms and protocols you interact with.
Subscribing to official project announcements, following security-focused blogs, and joining relevant community channels can help you stay ahead of potential vulnerabilities.
3. Conduct Periodic Risk Assessments
Periodic risk assessments enable you to evaluate the security posture of your digital assets. Identify potential weaknesses or areas of concern and take proactive steps to mitigate those risks. This includes reassessing the security practices of the platforms you utilize regularly.
Audits and Security Assessments
Audits and security assessments play a vital role in ensuring the integrity of DeFi projects. By having independent experts review the codebase and infrastructure, potential vulnerabilities can be identified before they are exploited.
1. Importance of Code Reviews
Code reviews involve scrutinizing the codebase for potential bugs, vulnerabilities, or insecure practices. Conducting thorough code reviews helps identify weaknesses in smart contracts, backend systems, or front-end interfaces.
2. Security Audits by Reputable Firms
Security audits by reputable firms provide an additional layer of assurance regarding the safety of a DeFi platform or protocol. These audits comprehensively analyze the project's codebase, infrastructure, and security practices.
3. Penetration Testing
Penetration testing involves simulating real-world attacks to identify a system's weaknesses or entry points. By conducting penetration tests regularly, projects can proactively address any vulnerabilities before attackers exploit them.
Harnessing Collective Intelligence
In addition to audits and security assessments, harnessing collective intelligence through community-driven security initiatives and bug bounty programs enhances the overall security posture of the Web3 ecosystem.
1. Community-Driven Security Initiatives
Community-driven security initiatives involve individuals or groups identifying potential vulnerabilities or risks within DeFi projects. These initiatives often conduct independent audits or share their findings with project teams to help improve security practices.
2. Bug Bounty Programs
Bug bounty programs incentivize security researchers or ethical hackers to identify vulnerabilities within DeFi projects. Projects can tap into a global pool of expertise by offering rewards for responsibly disclosing vulnerabilities to uncover potential weaknesses.
Guide Completed!
You've read the CyW3B 101 short guide intro on web security in the context of Web3 and DeFi. Armed with knowledge about the potential threats and vulnerabilities and strategies for fortifying your defenses, you are well on your way from being a novice to a hero in Web3 security.
Remember to stay vigilant and adopt best practices such as encryption, multi-factor authentication, and secure wallet management. Conduct due diligence when choosing DeFi platforms or protocols, continuously monitor your digital assets and stay informed about security advisories.
Now go forth confidently, safeguard your digital assets like a true champion, and thrive in decentralized finance.
----
What is CYW3B?
We're thrilled to announce our newsletter on Web3 Security! This is your chance to stay updated with the latest trends, tips, and insights.
- Get firsthand information from Web3 security experts
- Discover best practices to protect your digital assets
- Learn about the latest security protocols and standards for web3
Don't miss out on learning about web3 security.
CYW3B BY INCYB3R 🦉 | 👉 Click here to subscribe.
----
References
I originally published it on the web3 security blog, CYW3B.
----
Join INCYB3R - The primary focus of this blog is to provide valuable insights on cybersecurity education and career guidance.
I have set up this blog to share my firsthand experiences and the knowledge I have acquired while completing my master's degree in cybersecurity. Feel free to click on the banner to access more information. 👇 Join Us 👉 WhatsApp InCyb3r channel for insights and education.